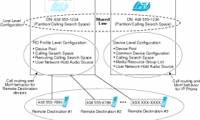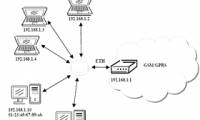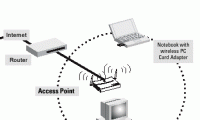
In the next part of this series, I will show you some of the security mechanisms available in wireless hardware.

In the next part of this article series, I will show you some of the wireless network security options in Windows Server 2008 operating system.

In this next article, I will show you how to deploy policy servers and how to enroll certificates and register Active Directory for that server.
In this article, I will show you how to use Windows 7 to log in to the domain using a single sign-on mechanism via a virtual private network connection.

In the following article, we will show you some basic steps to set up and configure the site to VPN site with Cisco ASA system. Currently, the concepts and applications of VPN for

In this article we will show you some of the issues that are needed when setting up WPA2-Enterprise wireless security.

In the following article, we will cover some basic operations to configure and set up Cisco ASA systems with devices based on Android, VPN operating system and Active Directory

You may be accustomed to using Wi-Fi networks at home and at work, offices, but few doubt that it is in this familiar environment that contains unexpected things. In any case, the

DHCP will help us easily set up access via network in the office, home, port - Port forwarding ... In the following article, we will guide you how to implement the process.

If you cannot keep the computer running continuously during the day, you can use the Wake - on - LAN (WOL) feature to access and remote control. This is really a difficult and

In the following article, we will show you how to fix Access Denied when accessing shared folders on any computer using Windows 7 operating system from another Windows 7 computer

Owning a server media system is great, unless other users don't know how to change and share bandwidth. By applying some basic rules of QoS, we can set the priority mode and

If you are using both a Mac and PC at home or office, due to business needs, you want to access files on a Windows 7 computer using Mac OS X Lion.

In the following article, we will show you how to access remote computers using DNS on the DD-WRT enabled device.

This article will introduce a new tool called NetSpot, a tool that allows users to statistics and create maps in wireless network design.

In this article we will list the six biggest Wi-Fi security errors that users often get, to help you avoid and protect your wireless network better.

Monitor bandwidth and quality of service (QoS) on the router line using Tomato firmware, combined with two tools, Mark Vejvoda's IPTables Bandwidth Monitor and Script 's Robert

In this tutorial we will show you how to configure a one-to-one NAT Rule for internal hosts.

In this tutorial, we will look at the main troubleshooting tasks to fix computers that cannot connect or keep a stable connection.

To solve the problem with a computer with dynamic IP, we need to have a DNS address that can update IP addresses regularly.
 In the next part of this series, I will show you some of the security mechanisms available in wireless hardware.
In the next part of this series, I will show you some of the security mechanisms available in wireless hardware. In the next part of this article series, I will show you some of the wireless network security options in Windows Server 2008 operating system.
In the next part of this article series, I will show you some of the wireless network security options in Windows Server 2008 operating system. In this next article, I will show you how to deploy policy servers and how to enroll certificates and register Active Directory for that server.
In this next article, I will show you how to deploy policy servers and how to enroll certificates and register Active Directory for that server. In this article, I will show you how to use Windows 7 to log in to the domain using a single sign-on mechanism via a virtual private network connection.
In this article, I will show you how to use Windows 7 to log in to the domain using a single sign-on mechanism via a virtual private network connection. In the following article, we will show you some basic steps to set up and configure the site to VPN site with Cisco ASA system. Currently, the concepts and applications of VPN for
In the following article, we will show you some basic steps to set up and configure the site to VPN site with Cisco ASA system. Currently, the concepts and applications of VPN for In this article we will show you some of the issues that are needed when setting up WPA2-Enterprise wireless security.
In this article we will show you some of the issues that are needed when setting up WPA2-Enterprise wireless security. In the following article, we will cover some basic operations to configure and set up Cisco ASA systems with devices based on Android, VPN operating system and Active Directory
In the following article, we will cover some basic operations to configure and set up Cisco ASA systems with devices based on Android, VPN operating system and Active Directory You may be accustomed to using Wi-Fi networks at home and at work, offices, but few doubt that it is in this familiar environment that contains unexpected things. In any case, the
You may be accustomed to using Wi-Fi networks at home and at work, offices, but few doubt that it is in this familiar environment that contains unexpected things. In any case, the DHCP will help us easily set up access via network in the office, home, port - Port forwarding ... In the following article, we will guide you how to implement the process.
DHCP will help us easily set up access via network in the office, home, port - Port forwarding ... In the following article, we will guide you how to implement the process. If you cannot keep the computer running continuously during the day, you can use the Wake - on - LAN (WOL) feature to access and remote control. This is really a difficult and
If you cannot keep the computer running continuously during the day, you can use the Wake - on - LAN (WOL) feature to access and remote control. This is really a difficult and In the following article, we will show you how to fix Access Denied when accessing shared folders on any computer using Windows 7 operating system from another Windows 7 computer
In the following article, we will show you how to fix Access Denied when accessing shared folders on any computer using Windows 7 operating system from another Windows 7 computer Owning a server media system is great, unless other users don't know how to change and share bandwidth. By applying some basic rules of QoS, we can set the priority mode and
Owning a server media system is great, unless other users don't know how to change and share bandwidth. By applying some basic rules of QoS, we can set the priority mode and If you are using both a Mac and PC at home or office, due to business needs, you want to access files on a Windows 7 computer using Mac OS X Lion.
If you are using both a Mac and PC at home or office, due to business needs, you want to access files on a Windows 7 computer using Mac OS X Lion. In the following article, we will show you how to access remote computers using DNS on the DD-WRT enabled device.
In the following article, we will show you how to access remote computers using DNS on the DD-WRT enabled device. This article will introduce a new tool called NetSpot, a tool that allows users to statistics and create maps in wireless network design.
This article will introduce a new tool called NetSpot, a tool that allows users to statistics and create maps in wireless network design. In this article we will list the six biggest Wi-Fi security errors that users often get, to help you avoid and protect your wireless network better.
In this article we will list the six biggest Wi-Fi security errors that users often get, to help you avoid and protect your wireless network better. Monitor bandwidth and quality of service (QoS) on the router line using Tomato firmware, combined with two tools, Mark Vejvoda's IPTables Bandwidth Monitor and Script 's Robert
Monitor bandwidth and quality of service (QoS) on the router line using Tomato firmware, combined with two tools, Mark Vejvoda's IPTables Bandwidth Monitor and Script 's Robert In this tutorial we will show you how to configure a one-to-one NAT Rule for internal hosts.
In this tutorial we will show you how to configure a one-to-one NAT Rule for internal hosts. In this tutorial, we will look at the main troubleshooting tasks to fix computers that cannot connect or keep a stable connection.
In this tutorial, we will look at the main troubleshooting tasks to fix computers that cannot connect or keep a stable connection. To solve the problem with a computer with dynamic IP, we need to have a DNS address that can update IP addresses regularly.
To solve the problem with a computer with dynamic IP, we need to have a DNS address that can update IP addresses regularly.