Improve security of Wifi network system
TipsMake.com - Maybe you are too familiar with using Wifi network at home and office, office work, but few people doubt that it is in this familiar environment that contains unexpected things. In any case, the advantages and disadvantages always exist side by side, and the wifi network we are talking about is no exception. In the following article, we will introduce and present some basic operations for users to improve as well as improve the performance and security of the Wi-Fi network they are using.

Optimize the performance of Wifi for VoIP, video and game:
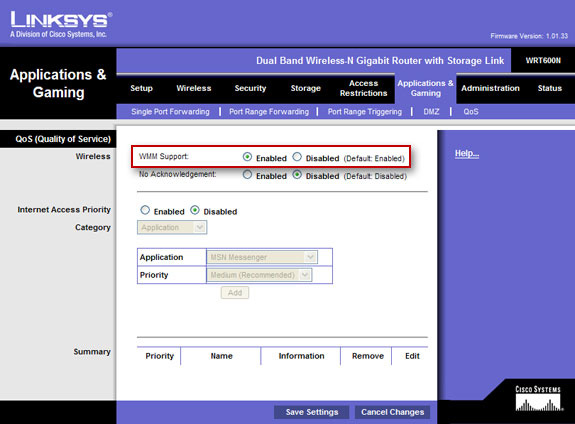
If your Skype or Second Life game is interrupted halfway through, the process of transferring music through iTunes has the same problem when someone in the house starts playing World of Warcraft . this is is the right time to think about buying a new router device. Most routers in the last 20 years have Quality of service - QoS features , although users will have to perform firmware upgrades to activate them. For example, the QoS configuration section for Linksys routers is usually in the Applications & Gaming section (but must first enable WMM Support - as shown).
Select the corresponding QoS application:

To continue, we need to enable Internet Access Priority support for programs that require a lot of voice and media data. As an example here, you select each application in the list one by one.
Prioritize different data packets:

When switching to this step, we can select the priority levels - Priority for the program, with the levels High, Medium, Normal, or Low , then click the Add button below. For example, you can set Low mode for programs, download services such as BitTorrent , High for VoIP . to ensure quality. In addition, you should note that Linksys also supports users more specifically for VoIP devices, such as phones when connected directly to the network. However, not all router devices have this feature, but at least still QoS or WMM , the system will automatically manage and divide the amount of data accordingly, but the feature above is not enabled in default mode (as mentioned above).
Turn off Wifi when not in use:
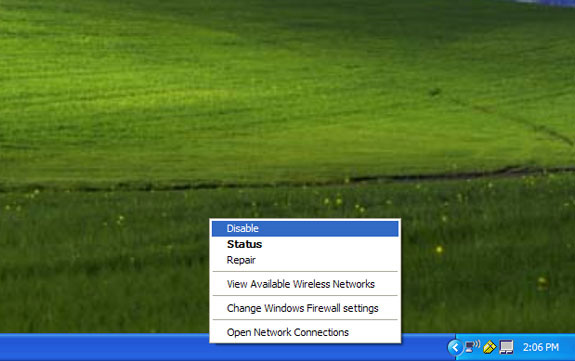
Technically, this is also an energy saving way of laptop computers, which is to turn off the function of Wifi network card when not in use. At the same time, this process also helps you avoid the broadcast area accidentally containing all kinds of malicious code, besides helping users extend the life of laptop batteries. Many laptops now have a button that turns on or off Wifi, or in Windows XP, we just need to right-click the Wifi icon under the system tray and select Disable.
Turn on Wifi in Windows XP:
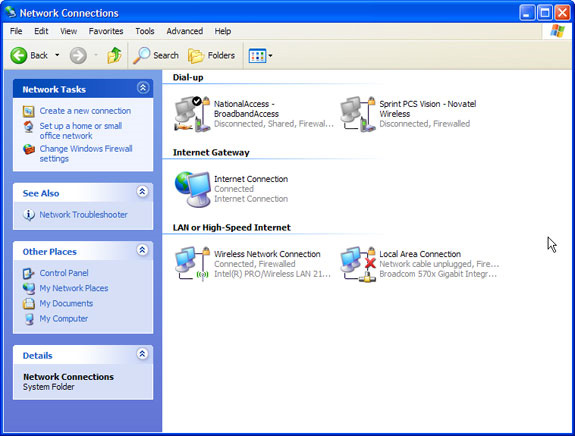
Turning off Wifi as above will temporarily remove the program's icon from the system tray, to restore in Windows XP operating system, open Network Connections in Control Panel, then double-click the Wifi icon.
Turn on and off Wifi in Windows Vista:
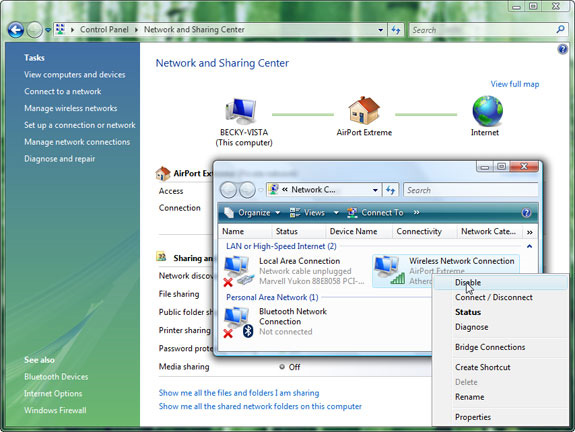
To do this in Windows Vista, just open the Network and Sharing Center in Control Panel and select View status under Connections .
Keep track of unusual phenomena in your network:
When using or managing a home or office Wi-Fi network, will you be able to detect who is accessing the system? In fact, there are many users who think their Wi-Fi network is completely secure, the data encryption methods they use are very secure . But technically, security mechanisms, in particular WEP can be easily hacked, even data streams allocated via MAC addresses can be tampered with. To fix it, download and use the free version of Network Magic Essentials application - this program will display the corresponding display map of all computer components, servers, printers or devices. Peripherals are connecting to the user's network.
Receive notifications whenever a connected device is available:
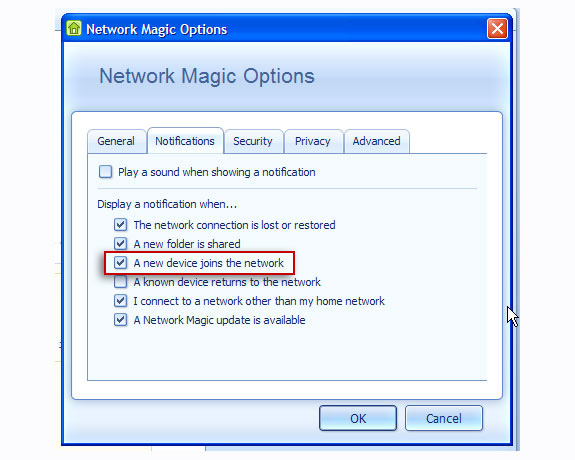
But in fact, it is not always possible to turn on Network Magic in active mode, but instead, we can set the display mode of pop-up notifications when there is a new device. Any connection to the network, so can easily detect and take precautions against the intrusion of strangers. To do so, select the Options tab from the Tools menu, then select the Notifications tab and check the box A new device joins the network.
'Tracking' intruders - Intruder:
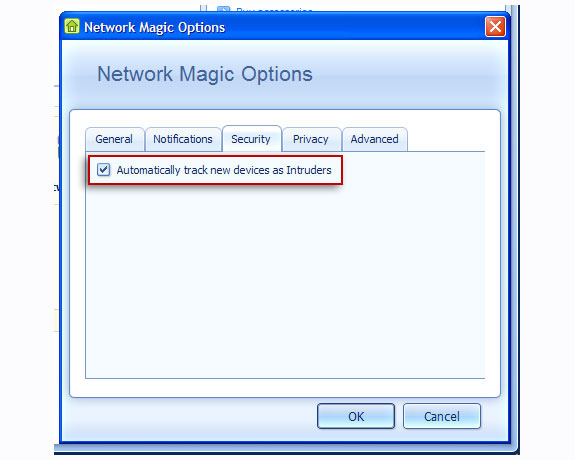
Finally, select the Security tab and check Automatically track new devices as Intruders, so users can monitor all activities of the components that are supposed to be Intruder .
Hotspot sharing:

Currently, the Linksys Wireless-G Travel series of products have a unique feature: allowing users to share their Wi-Fi connection via an encrypted wired network. Therefore, in fact, we can apply this method to share a paid broadband connection.
Use Wifi to share Wifi:
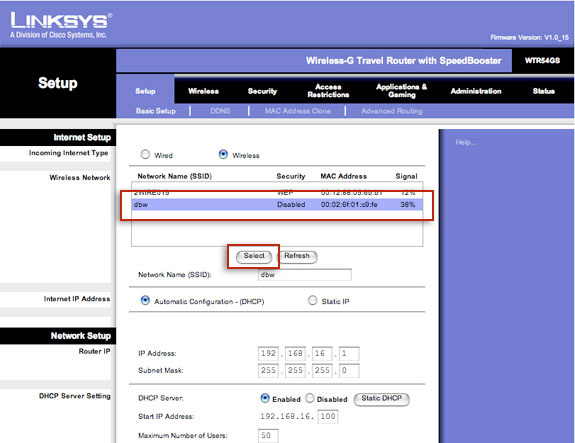
To share Wifi, you just need to turn on the router, connect via Wifi, open the settings - Configuration with the browser, here select the Hotspot section we want to connect from the list (eg T-Mobile) and press the Select button. Then open a new window on your browser and log in to that Hotspot, do any necessary setup, and from now on, other computers that can connect to Linksys Travel Router will also automatically This connection via Hotspot charges this fee, but they do not need to pay any extra costs.
Safety guarantee for Hotspot connection:
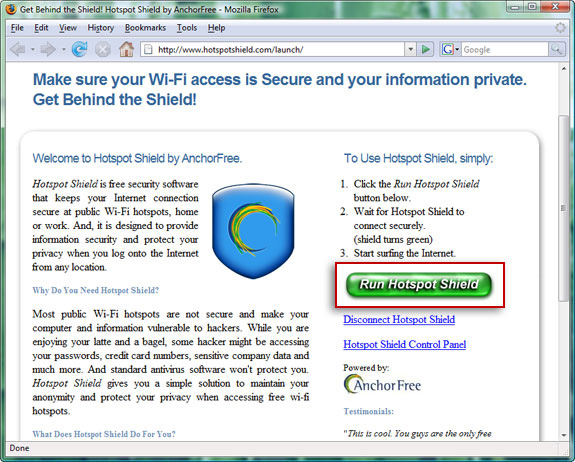
In fact, public hotspots - Public hotspot is an attractive target of hackers, besides some networks are not equipped with any form of security to serve. for all customers in that area. Unless the administrator uses a VPN software, anyone can see all the wireless Internet traffic, including the password strings and email messages. If you are not using any VPN function, please consult and use Hotspot Shield - AnchorFree's free software. All you need to do is download and install, your browser will display the screen above, click Run Hotspot Shield and the program's protection will start.
Turn off Hotspot Shield's VPN:
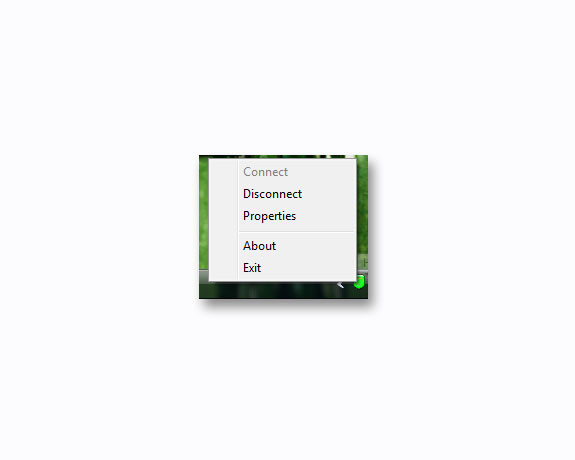
If you don't want to use Hotspot Shield , just right-click the program icon under the system tray and select Disconnect , the icon color will change from green to red. To activate again, right-click and select Connect .
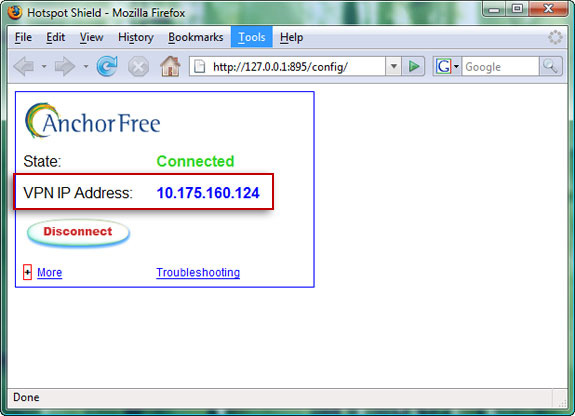
In addition, during the connection process, to know the current IP address of the system, select the Properties in the menu displayed. Because Hotspot Shield is a free application, we will see a banner ad at the top of the browser.
Turn off the Peer - to - Peer (Ad - Hoc) function via Wi-Fi:
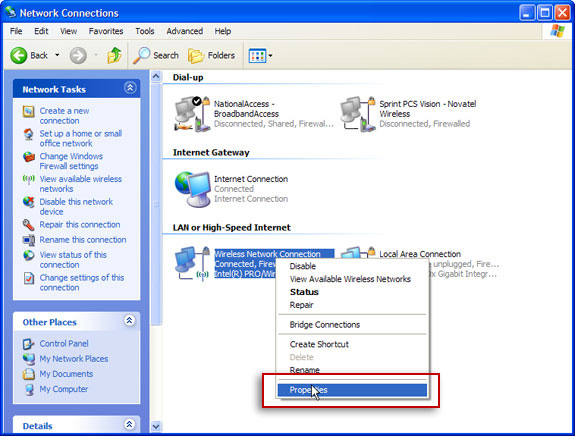
One of the most common and common causes for bad guys to infiltrate and distribute malicious code via public Wi-Fi connections is the ad-hoc Wifi network, originating from any computer in the system. For example, an attacker sits within the scope of an airport and starts connecting to the SSID called T-Mobile or Free Wi-Fi. Many other users may accidentally or automatically connect to the correct SSID, and other types of malicious programs will get into their computers. To turn off this feature in Windows XP, open the Network Connections section from Control Panel, right-click the Wifi connection section and select Properties .
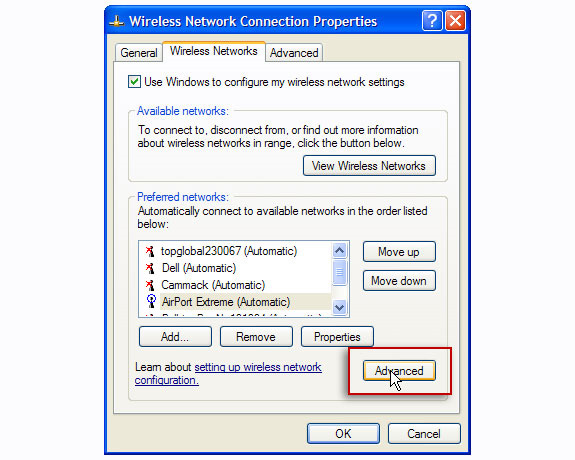
Select the Wireless Networks tab and click the Advanced button.
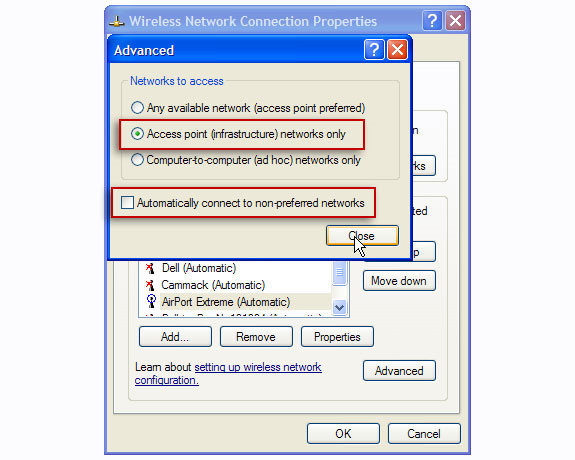
Finally, select the Access point (infrastructure) networks only section, and do not forget to remove the check box in Automatically connect to non-preferred networks . In Windows Vista or 7, we don't need to do that because there is an ad-hoc network option mechanism right in the first step.
Good luck!