For years, many people have followed the advice to change their passwords every few months. But is this necessary in today's world?

Many devices today incorporate Bluetooth technology to enable wireless communication with other Bluetooth devices. Before using Bluetooth, it is important to understand what this

Nowadays, free wifi networks are installed everywhere, from coffee shops, amusement parks, shopping malls, etc. This is very convenient for us users to be able to connect to the

In this age of information explosion, some people don't think about what they share on Facebook. However, there are some things you should not share on Facebook.

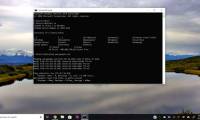
Hidden deep within Windows is a command line world that few people know about. In this article, we will show you how to resolve errors and make your computer more secure using the

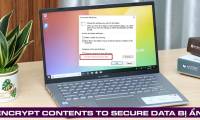
In case Encrypt contents to secure data is hidden, please follow the instructions in TipsMake's article to know how to handle it.

Disk consolidation and data loss is a problem that many computer users encounter. To avoid losing data after merging drives, don't miss TipsMake's article.

Microsoft has an external tool that can be used to scan and find malware on your Windows system: Microsoft Safety Scanner.

In PC computers, much of your personal information can be accessed illegally. That's because Windows data stored publicly on the drive is not encrypted or protected by encryption

Hiding your IP address when surfing the Web in public places will help you avoid troubles from the Internet.

In this article, TipsMake.com will help you learn about some cases of forging http headers to achieve unauthorized access.

In this article, TipsMake.com will learn with you about how to attack Session Fixation.

This is an article on how to change your computer's password if you accidentally forget it. You can do this in several ways on Windows and Mac computers.

In PC computers, much of your personal information can be accessed illegally. That's because Windows data stored publicly on the drive is not encrypted or protected by encryption

Internet Protocol (IP)/Internet Control Message Protocol (ICMP) Fragmentation DDoS attack is a common form of denial of service attack. In such an attack, datagram fragmentation

User authentication is a security process that prevents unauthorized users from accessing your device or network.

So what is the price to pay for a hacked website? How does it affect your business? Let's find the answer with TipsMake.com.

We invite you to join TipsMake.com to learn about security issues in the HTTP protocol.

The VENOM vulnerability affects all major CPU vendors, including Intel, AMD, and ARM. VENOM allows malicious actors to read the contents of a computer's memory and potentially

In this article, TipsMake.com learns about cookies and related security issues.
 For years, many people have followed the advice to change their passwords every few months. But is this necessary in today's world?
For years, many people have followed the advice to change their passwords every few months. But is this necessary in today's world? Many devices today incorporate Bluetooth technology to enable wireless communication with other Bluetooth devices. Before using Bluetooth, it is important to understand what this
Many devices today incorporate Bluetooth technology to enable wireless communication with other Bluetooth devices. Before using Bluetooth, it is important to understand what this Nowadays, free wifi networks are installed everywhere, from coffee shops, amusement parks, shopping malls, etc. This is very convenient for us users to be able to connect to the
Nowadays, free wifi networks are installed everywhere, from coffee shops, amusement parks, shopping malls, etc. This is very convenient for us users to be able to connect to the In this age of information explosion, some people don't think about what they share on Facebook. However, there are some things you should not share on Facebook.
In this age of information explosion, some people don't think about what they share on Facebook. However, there are some things you should not share on Facebook. Hidden deep within Windows is a command line world that few people know about. In this article, we will show you how to resolve errors and make your computer more secure using the
Hidden deep within Windows is a command line world that few people know about. In this article, we will show you how to resolve errors and make your computer more secure using the In case Encrypt contents to secure data is hidden, please follow the instructions in TipsMake's article to know how to handle it.
In case Encrypt contents to secure data is hidden, please follow the instructions in TipsMake's article to know how to handle it. Disk consolidation and data loss is a problem that many computer users encounter. To avoid losing data after merging drives, don't miss TipsMake's article.
Disk consolidation and data loss is a problem that many computer users encounter. To avoid losing data after merging drives, don't miss TipsMake's article. Microsoft has an external tool that can be used to scan and find malware on your Windows system: Microsoft Safety Scanner.
Microsoft has an external tool that can be used to scan and find malware on your Windows system: Microsoft Safety Scanner. In PC computers, much of your personal information can be accessed illegally. That's because Windows data stored publicly on the drive is not encrypted or protected by encryption
In PC computers, much of your personal information can be accessed illegally. That's because Windows data stored publicly on the drive is not encrypted or protected by encryption Hiding your IP address when surfing the Web in public places will help you avoid troubles from the Internet.
Hiding your IP address when surfing the Web in public places will help you avoid troubles from the Internet. In this article, TipsMake.com will help you learn about some cases of forging http headers to achieve unauthorized access.
In this article, TipsMake.com will help you learn about some cases of forging http headers to achieve unauthorized access. In this article, TipsMake.com will learn with you about how to attack Session Fixation.
In this article, TipsMake.com will learn with you about how to attack Session Fixation. This is an article on how to change your computer's password if you accidentally forget it. You can do this in several ways on Windows and Mac computers.
This is an article on how to change your computer's password if you accidentally forget it. You can do this in several ways on Windows and Mac computers. In PC computers, much of your personal information can be accessed illegally. That's because Windows data stored publicly on the drive is not encrypted or protected by encryption
In PC computers, much of your personal information can be accessed illegally. That's because Windows data stored publicly on the drive is not encrypted or protected by encryption Internet Protocol (IP)/Internet Control Message Protocol (ICMP) Fragmentation DDoS attack is a common form of denial of service attack. In such an attack, datagram fragmentation
Internet Protocol (IP)/Internet Control Message Protocol (ICMP) Fragmentation DDoS attack is a common form of denial of service attack. In such an attack, datagram fragmentation User authentication is a security process that prevents unauthorized users from accessing your device or network.
User authentication is a security process that prevents unauthorized users from accessing your device or network. So what is the price to pay for a hacked website? How does it affect your business? Let's find the answer with TipsMake.com.
So what is the price to pay for a hacked website? How does it affect your business? Let's find the answer with TipsMake.com. We invite you to join TipsMake.com to learn about security issues in the HTTP protocol.
We invite you to join TipsMake.com to learn about security issues in the HTTP protocol. The VENOM vulnerability affects all major CPU vendors, including Intel, AMD, and ARM. VENOM allows malicious actors to read the contents of a computer's memory and potentially
The VENOM vulnerability affects all major CPU vendors, including Intel, AMD, and ARM. VENOM allows malicious actors to read the contents of a computer's memory and potentially In this article, TipsMake.com learns about cookies and related security issues.
In this article, TipsMake.com learns about cookies and related security issues.