HTTPS (Hypertext Transfer Protocol Secure) is a secure hypertext transfer protocol that helps increase website security.

All that time spent glued to the screens of those electronic devices can have a variety of negative effects on both your body and mind. To counteract these problems, you can opt

The file has the ARW extension, which stands for Sony Alpha Raw and is therefore a Sony RAW Image file. It is based on the TIF file format and is similar to other RAW files from

This article explains what an ADP file is and how to open it on your computer.

Windscribe VPN is a cross-platform application that helps unblock all blocked websites, remove ads during use, and it can also help protect your WiFi connection, increasing privacy

What is wireless charging? Wireless charging is a type of charging where you don't need to plug a cable into your smartphone to charge it. Simply place it on a special pad or stand

You may have heard people telling you to back up your computer or that you need to have more secure passwords. Good tech habits aren't just for geeks, they can save you money and

Can your computer open ICO files? Today's article will explain what they are used for and suggest software that can open or process your .ICO files.

There is a long-standing belief that magnets can damage electronic devices placed nearby.

File syncing and backup may seem similar, but they serve very different purposes—and failing to differentiate between them can lead to data loss.

A file with the EXE extension is an executable file used in operating systems such as Windows, MS-DOS, OpenVMS, and ReactOS to open software programs.

This article will cover what a RAF file is and what programs can open or convert it.

IMEIs are mysterious, obscure numbers stamped around various parts of a phone. IMEIs are often used to identify phones, but some people wonder if they can be used for surveillance

The DNS Server Isn't Responding error is a common error message when your browser cannot connect to the DNS (Domain Name System) server.

GitIgnore is a file in a Git project, called .gitignore. Its main function is to list files or directories that you don't want Git to track or store.

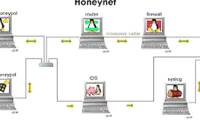
A Honeynet is a network of multiple Honeypots designed to simulate a real network, complete with multiple systems, databases, servers, and other digital assets.

HTTP Authentication is a security mechanism that helps verify the identity of users when they access web resources.

Google Remote Procedure Call (gRPC) is an HTTP/2-based RPC protocol that allows clients and servers to communicate via methods defined in protobuffers.

GPU (Graphics Processing Unit) is a type of microprocessor specially designed to enhance image and video processing capabilities.

Figma is a powerful, cloud-based online vector graphics and user interface design tool.
 HTTPS (Hypertext Transfer Protocol Secure) is a secure hypertext transfer protocol that helps increase website security.
HTTPS (Hypertext Transfer Protocol Secure) is a secure hypertext transfer protocol that helps increase website security. All that time spent glued to the screens of those electronic devices can have a variety of negative effects on both your body and mind. To counteract these problems, you can opt
All that time spent glued to the screens of those electronic devices can have a variety of negative effects on both your body and mind. To counteract these problems, you can opt The file has the ARW extension, which stands for Sony Alpha Raw and is therefore a Sony RAW Image file. It is based on the TIF file format and is similar to other RAW files from
The file has the ARW extension, which stands for Sony Alpha Raw and is therefore a Sony RAW Image file. It is based on the TIF file format and is similar to other RAW files from This article explains what an ADP file is and how to open it on your computer.
This article explains what an ADP file is and how to open it on your computer. Windscribe VPN is a cross-platform application that helps unblock all blocked websites, remove ads during use, and it can also help protect your WiFi connection, increasing privacy
Windscribe VPN is a cross-platform application that helps unblock all blocked websites, remove ads during use, and it can also help protect your WiFi connection, increasing privacy What is wireless charging? Wireless charging is a type of charging where you don't need to plug a cable into your smartphone to charge it. Simply place it on a special pad or stand
What is wireless charging? Wireless charging is a type of charging where you don't need to plug a cable into your smartphone to charge it. Simply place it on a special pad or stand You may have heard people telling you to back up your computer or that you need to have more secure passwords. Good tech habits aren't just for geeks, they can save you money and
You may have heard people telling you to back up your computer or that you need to have more secure passwords. Good tech habits aren't just for geeks, they can save you money and Can your computer open ICO files? Today's article will explain what they are used for and suggest software that can open or process your .ICO files.
Can your computer open ICO files? Today's article will explain what they are used for and suggest software that can open or process your .ICO files. There is a long-standing belief that magnets can damage electronic devices placed nearby.
There is a long-standing belief that magnets can damage electronic devices placed nearby. File syncing and backup may seem similar, but they serve very different purposes—and failing to differentiate between them can lead to data loss.
File syncing and backup may seem similar, but they serve very different purposes—and failing to differentiate between them can lead to data loss. A file with the EXE extension is an executable file used in operating systems such as Windows, MS-DOS, OpenVMS, and ReactOS to open software programs.
A file with the EXE extension is an executable file used in operating systems such as Windows, MS-DOS, OpenVMS, and ReactOS to open software programs. This article will cover what a RAF file is and what programs can open or convert it.
This article will cover what a RAF file is and what programs can open or convert it. IMEIs are mysterious, obscure numbers stamped around various parts of a phone. IMEIs are often used to identify phones, but some people wonder if they can be used for surveillance
IMEIs are mysterious, obscure numbers stamped around various parts of a phone. IMEIs are often used to identify phones, but some people wonder if they can be used for surveillance The DNS Server Isn't Responding error is a common error message when your browser cannot connect to the DNS (Domain Name System) server.
The DNS Server Isn't Responding error is a common error message when your browser cannot connect to the DNS (Domain Name System) server. GitIgnore is a file in a Git project, called .gitignore. Its main function is to list files or directories that you don't want Git to track or store.
GitIgnore is a file in a Git project, called .gitignore. Its main function is to list files or directories that you don't want Git to track or store. A Honeynet is a network of multiple Honeypots designed to simulate a real network, complete with multiple systems, databases, servers, and other digital assets.
A Honeynet is a network of multiple Honeypots designed to simulate a real network, complete with multiple systems, databases, servers, and other digital assets. HTTP Authentication is a security mechanism that helps verify the identity of users when they access web resources.
HTTP Authentication is a security mechanism that helps verify the identity of users when they access web resources. Google Remote Procedure Call (gRPC) is an HTTP/2-based RPC protocol that allows clients and servers to communicate via methods defined in protobuffers.
Google Remote Procedure Call (gRPC) is an HTTP/2-based RPC protocol that allows clients and servers to communicate via methods defined in protobuffers. GPU (Graphics Processing Unit) is a type of microprocessor specially designed to enhance image and video processing capabilities.
GPU (Graphics Processing Unit) is a type of microprocessor specially designed to enhance image and video processing capabilities. Figma is a powerful, cloud-based online vector graphics and user interface design tool.
Figma is a powerful, cloud-based online vector graphics and user interface design tool.