Still using 123456 or your birth year as your password? It's time to stop! Using weak and commonly used passwords is one of the main reasons why you might get hacked.

Threats, from cyberattacks to unauthorized surveillance, are real, but you can prevent intruders from accessing your webcam and invading your personal space.

QR codes seem pretty harmless until you scan a bad one and get something nasty thrown at your system. If you want to keep your phone and data safe, there are a few ways you can

Email scams are more sophisticated than ever, but you can still keep yourself (and your business) safe by taking some necessary due diligence.

Luckily, this great app will alert you if you scan something bad, making it a great first line of defense and it's completely free.

Downloading cracked software comes with many risks that far outweigh the benefits of getting something for free. There is a reason why developers and cybersecurity experts advise

While no one wants to think about having their personally identifiable information exposed, it's important to know what to do if this situation ever arises.

Security is important when shopping online, which is why many people are starting to use virtual or disposable credit cards.

While VPN is the most popular solution, many people prefer to use Smart DNS Proxy as it is a simpler and more efficient way to access content that is not available locally.

From phishing to database breaches, protecting yourself online is becoming more and more difficult these days. Hardware security keys are a viable solution to add an extra layer of

Backing up your data is essential, but encrypting your files prevents unauthorized access. Encryption converts files into unreadable data, ensuring that even if your backup is

The number of DDoS attacks has increased significantly in scale and complexity, causing business disruption, financial loss and reputational damage. Effective anti-ddos software

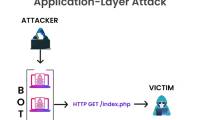
Application Layer Attacks are a type of Distributed Denial of Service (DDoS) attack that is a type of cyber attack that targets the top layer in the OSI model, where protocols like

Protocol Attacks are a type of cyber attack that is carried out by exploiting weaknesses in communication protocols.

Volumetric Attacks are a type of cyber attack that falls under the category of DDoS (Distributed Denial of Service). Attackers will send large amounts of unwanted data to a

A Trojan or Trojan horse is a type of malicious code or software that can take control of a user's computer remotely.

APT is a broad term used to describe an attack campaign, usually carried out by a group of attackers. How does APT attack work? Let's find out in the following article.

Cyber Kill Chain is a cybersecurity model developed by Lockheed Martin that consists of eight stages from information gathering to the attacker stealing data.

Joker malware is a sophisticated malware that targets mobile devices, especially on Android and iOS operating systems.

DLP (Data Loss Prevention) is a set of solutions, strategies, processes, and technologies to protect sensitive data from being lost, stolen, accessed without authorization, or
 Still using 123456 or your birth year as your password? It's time to stop! Using weak and commonly used passwords is one of the main reasons why you might get hacked.
Still using 123456 or your birth year as your password? It's time to stop! Using weak and commonly used passwords is one of the main reasons why you might get hacked. Threats, from cyberattacks to unauthorized surveillance, are real, but you can prevent intruders from accessing your webcam and invading your personal space.
Threats, from cyberattacks to unauthorized surveillance, are real, but you can prevent intruders from accessing your webcam and invading your personal space. QR codes seem pretty harmless until you scan a bad one and get something nasty thrown at your system. If you want to keep your phone and data safe, there are a few ways you can
QR codes seem pretty harmless until you scan a bad one and get something nasty thrown at your system. If you want to keep your phone and data safe, there are a few ways you can Email scams are more sophisticated than ever, but you can still keep yourself (and your business) safe by taking some necessary due diligence.
Email scams are more sophisticated than ever, but you can still keep yourself (and your business) safe by taking some necessary due diligence. Luckily, this great app will alert you if you scan something bad, making it a great first line of defense and it's completely free.
Luckily, this great app will alert you if you scan something bad, making it a great first line of defense and it's completely free. Downloading cracked software comes with many risks that far outweigh the benefits of getting something for free. There is a reason why developers and cybersecurity experts advise
Downloading cracked software comes with many risks that far outweigh the benefits of getting something for free. There is a reason why developers and cybersecurity experts advise While no one wants to think about having their personally identifiable information exposed, it's important to know what to do if this situation ever arises.
While no one wants to think about having their personally identifiable information exposed, it's important to know what to do if this situation ever arises. Security is important when shopping online, which is why many people are starting to use virtual or disposable credit cards.
Security is important when shopping online, which is why many people are starting to use virtual or disposable credit cards. While VPN is the most popular solution, many people prefer to use Smart DNS Proxy as it is a simpler and more efficient way to access content that is not available locally.
While VPN is the most popular solution, many people prefer to use Smart DNS Proxy as it is a simpler and more efficient way to access content that is not available locally. From phishing to database breaches, protecting yourself online is becoming more and more difficult these days. Hardware security keys are a viable solution to add an extra layer of
From phishing to database breaches, protecting yourself online is becoming more and more difficult these days. Hardware security keys are a viable solution to add an extra layer of Backing up your data is essential, but encrypting your files prevents unauthorized access. Encryption converts files into unreadable data, ensuring that even if your backup is
Backing up your data is essential, but encrypting your files prevents unauthorized access. Encryption converts files into unreadable data, ensuring that even if your backup is The number of DDoS attacks has increased significantly in scale and complexity, causing business disruption, financial loss and reputational damage. Effective anti-ddos software
The number of DDoS attacks has increased significantly in scale and complexity, causing business disruption, financial loss and reputational damage. Effective anti-ddos software Application Layer Attacks are a type of Distributed Denial of Service (DDoS) attack that is a type of cyber attack that targets the top layer in the OSI model, where protocols like
Application Layer Attacks are a type of Distributed Denial of Service (DDoS) attack that is a type of cyber attack that targets the top layer in the OSI model, where protocols like Protocol Attacks are a type of cyber attack that is carried out by exploiting weaknesses in communication protocols.
Protocol Attacks are a type of cyber attack that is carried out by exploiting weaknesses in communication protocols. Volumetric Attacks are a type of cyber attack that falls under the category of DDoS (Distributed Denial of Service). Attackers will send large amounts of unwanted data to a
Volumetric Attacks are a type of cyber attack that falls under the category of DDoS (Distributed Denial of Service). Attackers will send large amounts of unwanted data to a A Trojan or Trojan horse is a type of malicious code or software that can take control of a user's computer remotely.
A Trojan or Trojan horse is a type of malicious code or software that can take control of a user's computer remotely. APT is a broad term used to describe an attack campaign, usually carried out by a group of attackers. How does APT attack work? Let's find out in the following article.
APT is a broad term used to describe an attack campaign, usually carried out by a group of attackers. How does APT attack work? Let's find out in the following article. Cyber Kill Chain is a cybersecurity model developed by Lockheed Martin that consists of eight stages from information gathering to the attacker stealing data.
Cyber Kill Chain is a cybersecurity model developed by Lockheed Martin that consists of eight stages from information gathering to the attacker stealing data. Joker malware is a sophisticated malware that targets mobile devices, especially on Android and iOS operating systems.
Joker malware is a sophisticated malware that targets mobile devices, especially on Android and iOS operating systems. DLP (Data Loss Prevention) is a set of solutions, strategies, processes, and technologies to protect sensitive data from being lost, stolen, accessed without authorization, or
DLP (Data Loss Prevention) is a set of solutions, strategies, processes, and technologies to protect sensitive data from being lost, stolen, accessed without authorization, or