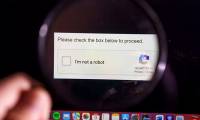
Organizations and businesses are increasingly focusing on ensuring digital security by regularly reviewing their systems and early detecting vulnerabilities that could expose them

It may come as a surprise to some Mac fans, but cybercriminals are still actively looking for ways to attack macOS.

1Password users, beware! Attackers are trying to steal your master password using sneaky phishing emails designed to trick you.

Often distributed in a malware-as-a-service model, infostealer malware is often used to steal data, remaining hidden for as long as possible.

The ESP32 is an extremely popular low-cost chip from Chinese manufacturer Espressif, which is estimated to be used in over 1 billion devices worldwide by 2023, and contains an

Clickjacking tricks unsuspecting people into clicking on links they think are harmless — but then downloads malware, harvests login credentials, and takes over online accounts.

Hackers are using Generative AI to target people more efficiently and cheaply than ever before.

Immediately after clicking on the phishing link in the email, the user's system is immediately compromised.

How to detect SSH brute force attacks and how to protect against them is an important topic in the cybersecurity field today. As more and more people use SSH to manage their

New Golang malware is using Telegram as a 'lever' to spread itself everywhere.

Network intrusion, data loss, downtime, etc. are all nightmares for network administrators and security staff. That is why IDS systems were born. Let's understand what IDS is

There have been many lessons learned from scams using deepfake technology.

The issue is common on new iPhone models like iPhone 15, 16, and iPhones running iOS 18.

Google warns users to be careful of 'disguised' VPN applications that spread malware.

After Telegram's policy changes, scam and hacker groups have massively moved to Discord and Signal platforms.

The scammer intentionally entered the wrong password, causing the user's account to be locked, then pretended to be a bank employee and tricked them into installing malware on the

New security vulnerability discovered on USB-C controller of iPhone 15 and 16, should users worry?

A video with the content 'losing hundreds of millions of dong after 5 seconds of scanning a QR code to transfer money' is causing concern, but experts say this is fake news.

Even experienced cybersecurity professionals fall victim to sophisticated phishing attacks.

The 'AIDS' floppy disk is credited as the world's first ransomware attack.
 Organizations and businesses are increasingly focusing on ensuring digital security by regularly reviewing their systems and early detecting vulnerabilities that could expose them
Organizations and businesses are increasingly focusing on ensuring digital security by regularly reviewing their systems and early detecting vulnerabilities that could expose them It may come as a surprise to some Mac fans, but cybercriminals are still actively looking for ways to attack macOS.
It may come as a surprise to some Mac fans, but cybercriminals are still actively looking for ways to attack macOS. 1Password users, beware! Attackers are trying to steal your master password using sneaky phishing emails designed to trick you.
1Password users, beware! Attackers are trying to steal your master password using sneaky phishing emails designed to trick you. Often distributed in a malware-as-a-service model, infostealer malware is often used to steal data, remaining hidden for as long as possible.
Often distributed in a malware-as-a-service model, infostealer malware is often used to steal data, remaining hidden for as long as possible. The ESP32 is an extremely popular low-cost chip from Chinese manufacturer Espressif, which is estimated to be used in over 1 billion devices worldwide by 2023, and contains an
The ESP32 is an extremely popular low-cost chip from Chinese manufacturer Espressif, which is estimated to be used in over 1 billion devices worldwide by 2023, and contains an Clickjacking tricks unsuspecting people into clicking on links they think are harmless — but then downloads malware, harvests login credentials, and takes over online accounts.
Clickjacking tricks unsuspecting people into clicking on links they think are harmless — but then downloads malware, harvests login credentials, and takes over online accounts. Hackers are using Generative AI to target people more efficiently and cheaply than ever before.
Hackers are using Generative AI to target people more efficiently and cheaply than ever before. Immediately after clicking on the phishing link in the email, the user's system is immediately compromised.
Immediately after clicking on the phishing link in the email, the user's system is immediately compromised. How to detect SSH brute force attacks and how to protect against them is an important topic in the cybersecurity field today. As more and more people use SSH to manage their
How to detect SSH brute force attacks and how to protect against them is an important topic in the cybersecurity field today. As more and more people use SSH to manage their New Golang malware is using Telegram as a 'lever' to spread itself everywhere.
New Golang malware is using Telegram as a 'lever' to spread itself everywhere. Network intrusion, data loss, downtime, etc. are all nightmares for network administrators and security staff. That is why IDS systems were born. Let's understand what IDS is
Network intrusion, data loss, downtime, etc. are all nightmares for network administrators and security staff. That is why IDS systems were born. Let's understand what IDS is There have been many lessons learned from scams using deepfake technology.
There have been many lessons learned from scams using deepfake technology. The issue is common on new iPhone models like iPhone 15, 16, and iPhones running iOS 18.
The issue is common on new iPhone models like iPhone 15, 16, and iPhones running iOS 18. Google warns users to be careful of 'disguised' VPN applications that spread malware.
Google warns users to be careful of 'disguised' VPN applications that spread malware. After Telegram's policy changes, scam and hacker groups have massively moved to Discord and Signal platforms.
After Telegram's policy changes, scam and hacker groups have massively moved to Discord and Signal platforms. The scammer intentionally entered the wrong password, causing the user's account to be locked, then pretended to be a bank employee and tricked them into installing malware on the
The scammer intentionally entered the wrong password, causing the user's account to be locked, then pretended to be a bank employee and tricked them into installing malware on the New security vulnerability discovered on USB-C controller of iPhone 15 and 16, should users worry?
New security vulnerability discovered on USB-C controller of iPhone 15 and 16, should users worry? A video with the content 'losing hundreds of millions of dong after 5 seconds of scanning a QR code to transfer money' is causing concern, but experts say this is fake news.
A video with the content 'losing hundreds of millions of dong after 5 seconds of scanning a QR code to transfer money' is causing concern, but experts say this is fake news. Even experienced cybersecurity professionals fall victim to sophisticated phishing attacks.
Even experienced cybersecurity professionals fall victim to sophisticated phishing attacks. The 'AIDS' floppy disk is credited as the world's first ransomware attack.
The 'AIDS' floppy disk is credited as the world's first ransomware attack.