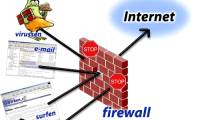
In this section, I will show you some of the factors that affect the stability and performance of the TMG firewall.

This test is our most comprehensive view of the network performance of the four carriers currently offering 4G networks (Big Four).
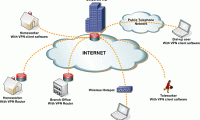
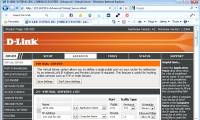
Setting up a virtual private network is a way that you don't have to buy expensive devices and still allow users to remotely access or connect offices together safely.
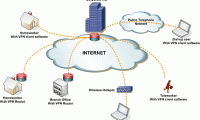
In this section, we will learn how to configure the VPN server and client, then test the whole process.

In this tutorial, we will show you how to set up Windows 7 or Vista VPN server and connect to Windows XP, Vista or Windows 7 computers.

VoIP is a new technology that uses an Internet connection to transfer data over the Internet in digital form. This is why television and telephone services have become dependent

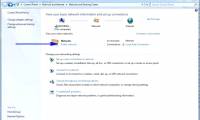
After regularly using a wireless connection on a Windows 7 system, you will have a list of saved wireless networks connected.

In this tutorial we will show you some ways to overcome the frustrating problems with a wireless network.

In the process of network connection there are indeed many problems that arise, but how to overcome them?

However, there are a lot of tools that can help some administrators to reduce this amount of hard work. Here are 10 utilities that we deem necessary for small networks.

How to provide secure guest access to your wireless network for electronic devices such as mobile phones, tablets, game interfaces, ...

Cisco Systems Cisco Connect utility helps establish a fast Wi-Fi network connection in 'wink', in just 3 simple steps.

In fact, there is a way to fake that MAC address, basically making the adapter's address look like another address.

In this article we will show you some third-party modules in case you implement a less-used EAP type that Windows itself does not support.

In the next part of this article series, I will show you some of the concepts used in the TMG firewall network - TMG firewall Network and TMG firewall Network Rule.

In this article, I will show you the network monitor tool Network Monitor 3.4 and its usefulness in troubleshooting and analyzing network traffic.

Linksys E-series is the most wireless router (router) towards the Wi-Fi 802.11n standard and many new support features.

In the next part of this series, we will discuss the considerations and strategies for implementing USV in complex environments.

In this series, I will show you some Wi-Fi network security techniques. The first part in this series will help you understand the vulnerabilities associated with wireless

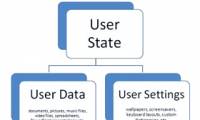
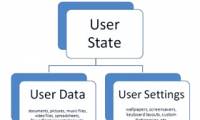
In this section, we will show you the high-level steps for implementing various Windows User State Virtualization solutions.
 In this section, I will show you some of the factors that affect the stability and performance of the TMG firewall.
In this section, I will show you some of the factors that affect the stability and performance of the TMG firewall. This test is our most comprehensive view of the network performance of the four carriers currently offering 4G networks (Big Four).
This test is our most comprehensive view of the network performance of the four carriers currently offering 4G networks (Big Four). Setting up a virtual private network is a way that you don't have to buy expensive devices and still allow users to remotely access or connect offices together safely.
Setting up a virtual private network is a way that you don't have to buy expensive devices and still allow users to remotely access or connect offices together safely. In this section, we will learn how to configure the VPN server and client, then test the whole process.
In this section, we will learn how to configure the VPN server and client, then test the whole process. In this tutorial, we will show you how to set up Windows 7 or Vista VPN server and connect to Windows XP, Vista or Windows 7 computers.
In this tutorial, we will show you how to set up Windows 7 or Vista VPN server and connect to Windows XP, Vista or Windows 7 computers. VoIP is a new technology that uses an Internet connection to transfer data over the Internet in digital form. This is why television and telephone services have become dependent
VoIP is a new technology that uses an Internet connection to transfer data over the Internet in digital form. This is why television and telephone services have become dependent After regularly using a wireless connection on a Windows 7 system, you will have a list of saved wireless networks connected.
After regularly using a wireless connection on a Windows 7 system, you will have a list of saved wireless networks connected. In this tutorial we will show you some ways to overcome the frustrating problems with a wireless network.
In this tutorial we will show you some ways to overcome the frustrating problems with a wireless network. In the process of network connection there are indeed many problems that arise, but how to overcome them?
In the process of network connection there are indeed many problems that arise, but how to overcome them? However, there are a lot of tools that can help some administrators to reduce this amount of hard work. Here are 10 utilities that we deem necessary for small networks.
However, there are a lot of tools that can help some administrators to reduce this amount of hard work. Here are 10 utilities that we deem necessary for small networks. How to provide secure guest access to your wireless network for electronic devices such as mobile phones, tablets, game interfaces, ...
How to provide secure guest access to your wireless network for electronic devices such as mobile phones, tablets, game interfaces, ... Cisco Systems Cisco Connect utility helps establish a fast Wi-Fi network connection in 'wink', in just 3 simple steps.
Cisco Systems Cisco Connect utility helps establish a fast Wi-Fi network connection in 'wink', in just 3 simple steps. In fact, there is a way to fake that MAC address, basically making the adapter's address look like another address.
In fact, there is a way to fake that MAC address, basically making the adapter's address look like another address. In this article we will show you some third-party modules in case you implement a less-used EAP type that Windows itself does not support.
In this article we will show you some third-party modules in case you implement a less-used EAP type that Windows itself does not support. In the next part of this article series, I will show you some of the concepts used in the TMG firewall network - TMG firewall Network and TMG firewall Network Rule.
In the next part of this article series, I will show you some of the concepts used in the TMG firewall network - TMG firewall Network and TMG firewall Network Rule. In this article, I will show you the network monitor tool Network Monitor 3.4 and its usefulness in troubleshooting and analyzing network traffic.
In this article, I will show you the network monitor tool Network Monitor 3.4 and its usefulness in troubleshooting and analyzing network traffic. Linksys E-series is the most wireless router (router) towards the Wi-Fi 802.11n standard and many new support features.
Linksys E-series is the most wireless router (router) towards the Wi-Fi 802.11n standard and many new support features. In the next part of this series, we will discuss the considerations and strategies for implementing USV in complex environments.
In the next part of this series, we will discuss the considerations and strategies for implementing USV in complex environments. In this series, I will show you some Wi-Fi network security techniques. The first part in this series will help you understand the vulnerabilities associated with wireless
In this series, I will show you some Wi-Fi network security techniques. The first part in this series will help you understand the vulnerabilities associated with wireless In this section, we will show you the high-level steps for implementing various Windows User State Virtualization solutions.
In this section, we will show you the high-level steps for implementing various Windows User State Virtualization solutions.