In this article, I will show you how to use the Forefront TMG SDK tools to expand Forefront TMG functionality and some of the information that the SDK provides.

In Part 2 of this series, we will continue the discussion about wireless network traffic security by examining rumors surrounding the use of passwords.

In this article, I will show you the pros and cons of promoting SSID and MAC address filtering.
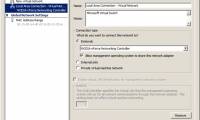
In this series, I will show you how to connect virtual networks in a Hyper-V environment and how to configure virtual networks to help you achieve your connectivity goals.

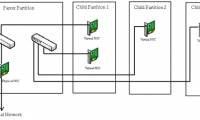
In Part 2 of this series, I will continue the discussion by talking about virtual networking on Hyper-V by studying the communication between partitions.

In Part 2 of this series, I will continue the discussion by showing you some options for domain controller virtualization.

In this third part, we will continue this idea by introducing you to the concept of using multiple virtual switches.

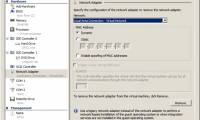
In this article, I will show you the roles and restrictions associated with physical network adapters within the host server.

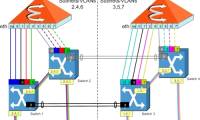
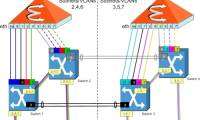
In this section, we will continue the discussion by connecting virtual networks in Hyper-V by introducing the concept of Virtual LANs (VLANs).

In this final section, I will show you some of the VLAN configuration methods.

To follow the previous two parts of this series, I will show you the options for domain controller virtualization.

Light Peak is a high-speed fiber optic technology, designed and designed by Intel to connect electronic devices. Currently, Light Peak bandwidth reaches 10Gb / s but may reach

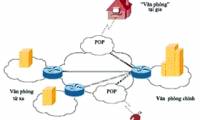
Before many new technologies such as 3G, 4G, Wimax does not seem to be the first choice for many businesses to deploy. However, there are opinions that this technology is

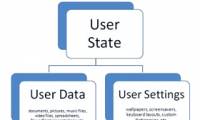
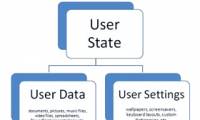
In Part 2 of this series, we will explore different business scenarios for implementing Windows User State Virtualization technologies (USV.

In this series, I will show you some of the basics of Access Rules for managing the new TMG firewall.

In the second part of this article series, I will show you the details of Access Rules after working together to create a rule using the wizard in Part 1.

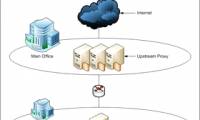
In this series, I will show you a typical deployment scenario and how to configure web proxy chaining in Forefront Threat Management Gateway (TMG) 2010.

In the third part of this series, we will show you how to manage the AppDataRoaming folder when virtualizing application settings and data.

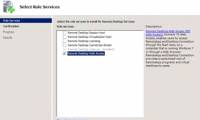
In this article we will show you how to publish Remote Desktop Web Access with the Remote Desktop Gateway on Microsoft Forefront TMG.

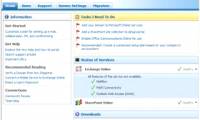
In this article, we will show you the easiest way to set up and run BPOS: configure BPOS as the primary mail server for a domain.
 In this article, I will show you how to use the Forefront TMG SDK tools to expand Forefront TMG functionality and some of the information that the SDK provides.
In this article, I will show you how to use the Forefront TMG SDK tools to expand Forefront TMG functionality and some of the information that the SDK provides. In Part 2 of this series, we will continue the discussion about wireless network traffic security by examining rumors surrounding the use of passwords.
In Part 2 of this series, we will continue the discussion about wireless network traffic security by examining rumors surrounding the use of passwords. In this article, I will show you the pros and cons of promoting SSID and MAC address filtering.
In this article, I will show you the pros and cons of promoting SSID and MAC address filtering. In this series, I will show you how to connect virtual networks in a Hyper-V environment and how to configure virtual networks to help you achieve your connectivity goals.
In this series, I will show you how to connect virtual networks in a Hyper-V environment and how to configure virtual networks to help you achieve your connectivity goals. In Part 2 of this series, I will continue the discussion by talking about virtual networking on Hyper-V by studying the communication between partitions.
In Part 2 of this series, I will continue the discussion by talking about virtual networking on Hyper-V by studying the communication between partitions. In Part 2 of this series, I will continue the discussion by showing you some options for domain controller virtualization.
In Part 2 of this series, I will continue the discussion by showing you some options for domain controller virtualization. In this third part, we will continue this idea by introducing you to the concept of using multiple virtual switches.
In this third part, we will continue this idea by introducing you to the concept of using multiple virtual switches. In this article, I will show you the roles and restrictions associated with physical network adapters within the host server.
In this article, I will show you the roles and restrictions associated with physical network adapters within the host server. In this section, we will continue the discussion by connecting virtual networks in Hyper-V by introducing the concept of Virtual LANs (VLANs).
In this section, we will continue the discussion by connecting virtual networks in Hyper-V by introducing the concept of Virtual LANs (VLANs). In this final section, I will show you some of the VLAN configuration methods.
In this final section, I will show you some of the VLAN configuration methods. To follow the previous two parts of this series, I will show you the options for domain controller virtualization.
To follow the previous two parts of this series, I will show you the options for domain controller virtualization. Light Peak is a high-speed fiber optic technology, designed and designed by Intel to connect electronic devices. Currently, Light Peak bandwidth reaches 10Gb / s but may reach
Light Peak is a high-speed fiber optic technology, designed and designed by Intel to connect electronic devices. Currently, Light Peak bandwidth reaches 10Gb / s but may reach Before many new technologies such as 3G, 4G, Wimax does not seem to be the first choice for many businesses to deploy. However, there are opinions that this technology is
Before many new technologies such as 3G, 4G, Wimax does not seem to be the first choice for many businesses to deploy. However, there are opinions that this technology is In Part 2 of this series, we will explore different business scenarios for implementing Windows User State Virtualization technologies (USV.
In Part 2 of this series, we will explore different business scenarios for implementing Windows User State Virtualization technologies (USV. In this series, I will show you some of the basics of Access Rules for managing the new TMG firewall.
In this series, I will show you some of the basics of Access Rules for managing the new TMG firewall. In the second part of this article series, I will show you the details of Access Rules after working together to create a rule using the wizard in Part 1.
In the second part of this article series, I will show you the details of Access Rules after working together to create a rule using the wizard in Part 1. In this series, I will show you a typical deployment scenario and how to configure web proxy chaining in Forefront Threat Management Gateway (TMG) 2010.
In this series, I will show you a typical deployment scenario and how to configure web proxy chaining in Forefront Threat Management Gateway (TMG) 2010. In the third part of this series, we will show you how to manage the AppDataRoaming folder when virtualizing application settings and data.
In the third part of this series, we will show you how to manage the AppDataRoaming folder when virtualizing application settings and data. In this article we will show you how to publish Remote Desktop Web Access with the Remote Desktop Gateway on Microsoft Forefront TMG.
In this article we will show you how to publish Remote Desktop Web Access with the Remote Desktop Gateway on Microsoft Forefront TMG. In this article, we will show you the easiest way to set up and run BPOS: configure BPOS as the primary mail server for a domain.
In this article, we will show you the easiest way to set up and run BPOS: configure BPOS as the primary mail server for a domain.