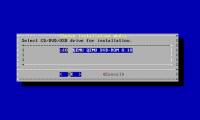
In the previous lesson, we created the Hyper-V task sequence. Now is the time to make this task sequence change so that we can use them to create Hyper-V servers that manage

The previous article showed users how to create executable image files and assign image files to Windows Deployment services. Although the image file that we created can start

The series has focused primarily on creating executable image files that can be used to create new virtual machines on it. However, these executable files won't work unless we

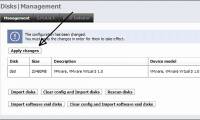
In the previous articles, we have created some image files for the virtual machine and also successfully installed SCVMM but still have a missing piece. At this time, users do not

The previous article showed you how to turn on and off the virtual machine with the command line. This article will introduce two methods of validating that virtual machines are

Most people who own a modern Internet connection today must use NAT (Network Address Translation) technology. NAT has been an integral part of deploying a wide area IP network

Among the hardware resources that are usually assigned to virtual machines, perhaps the memory is most fixed. This tutorial will show you how to manage virtual machine memory

Windows Server 2012 has been officially released since September 9 and many IT experts and system administrators are conducting reviews before deploying the software. The

Today, in parallel with the increasing quality of the Internet and the cost of gigabytes of storage, the need to download and store digital data, especially audio and video data.

After we have finished preparing the NAS system, in this second article, we will go through the steps of installing NAS4Free (FreeNAS 7) on our old system.

After you have completed the OS installation on the NAS box and finished configuring the IP according to your needs, we usually won't need to touch this machine again unless there

Yahoo! has just confirmed that their server was hacked earlier this week but user data is still safe.

Not long after the 'Back up & Restore' application was hacked, the Sony Pictures server system was also attacked by hackers.

If you are using a domain account, GoDaddy hosting is best, you should enable this 2-layer security feature, to be safer when administering the system.

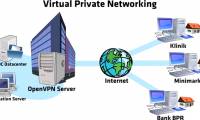
Windows integrates functionality as a VPN server even if this option is hidden. This trick applies to both Windows 7 and Windows 8. This server uses tunneling protocols from point

In the previous article, TipsMake.com mentioned 1 definition, knowledge can be called classics since the time of Internet appearance, it is PROXY. And in this article, we will

DNS servers are an important component for a better web experience, but very few people understand what problems their work or security will cause. Specifically, change DNS to do?

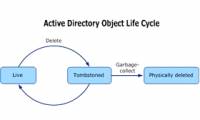
It can be said that one of the most 'problematic' issues in managing and working with Active Directory is mistakenly deleting data or objects accidentally or incorrectly handled by

In the previous article, I showed you how to recover deleted components in Active Directory, which are related to the lifecycle properties of tombstone objects. Technically this

In the previous sections of the article, we introduced you to some points in the process of configuring Incoming Email with SharePoint 2010, and this time we will continue with the
 In the previous lesson, we created the Hyper-V task sequence. Now is the time to make this task sequence change so that we can use them to create Hyper-V servers that manage
In the previous lesson, we created the Hyper-V task sequence. Now is the time to make this task sequence change so that we can use them to create Hyper-V servers that manage The previous article showed users how to create executable image files and assign image files to Windows Deployment services. Although the image file that we created can start
The previous article showed users how to create executable image files and assign image files to Windows Deployment services. Although the image file that we created can start The series has focused primarily on creating executable image files that can be used to create new virtual machines on it. However, these executable files won't work unless we
The series has focused primarily on creating executable image files that can be used to create new virtual machines on it. However, these executable files won't work unless we In the previous articles, we have created some image files for the virtual machine and also successfully installed SCVMM but still have a missing piece. At this time, users do not
In the previous articles, we have created some image files for the virtual machine and also successfully installed SCVMM but still have a missing piece. At this time, users do not The previous article showed you how to turn on and off the virtual machine with the command line. This article will introduce two methods of validating that virtual machines are
The previous article showed you how to turn on and off the virtual machine with the command line. This article will introduce two methods of validating that virtual machines are Most people who own a modern Internet connection today must use NAT (Network Address Translation) technology. NAT has been an integral part of deploying a wide area IP network
Most people who own a modern Internet connection today must use NAT (Network Address Translation) technology. NAT has been an integral part of deploying a wide area IP network Among the hardware resources that are usually assigned to virtual machines, perhaps the memory is most fixed. This tutorial will show you how to manage virtual machine memory
Among the hardware resources that are usually assigned to virtual machines, perhaps the memory is most fixed. This tutorial will show you how to manage virtual machine memory Windows Server 2012 has been officially released since September 9 and many IT experts and system administrators are conducting reviews before deploying the software. The
Windows Server 2012 has been officially released since September 9 and many IT experts and system administrators are conducting reviews before deploying the software. The Today, in parallel with the increasing quality of the Internet and the cost of gigabytes of storage, the need to download and store digital data, especially audio and video data.
Today, in parallel with the increasing quality of the Internet and the cost of gigabytes of storage, the need to download and store digital data, especially audio and video data. After we have finished preparing the NAS system, in this second article, we will go through the steps of installing NAS4Free (FreeNAS 7) on our old system.
After we have finished preparing the NAS system, in this second article, we will go through the steps of installing NAS4Free (FreeNAS 7) on our old system. After you have completed the OS installation on the NAS box and finished configuring the IP according to your needs, we usually won't need to touch this machine again unless there
After you have completed the OS installation on the NAS box and finished configuring the IP according to your needs, we usually won't need to touch this machine again unless there Yahoo! has just confirmed that their server was hacked earlier this week but user data is still safe.
Yahoo! has just confirmed that their server was hacked earlier this week but user data is still safe. Not long after the 'Back up & Restore' application was hacked, the Sony Pictures server system was also attacked by hackers.
Not long after the 'Back up & Restore' application was hacked, the Sony Pictures server system was also attacked by hackers. If you are using a domain account, GoDaddy hosting is best, you should enable this 2-layer security feature, to be safer when administering the system.
If you are using a domain account, GoDaddy hosting is best, you should enable this 2-layer security feature, to be safer when administering the system. Windows integrates functionality as a VPN server even if this option is hidden. This trick applies to both Windows 7 and Windows 8. This server uses tunneling protocols from point
Windows integrates functionality as a VPN server even if this option is hidden. This trick applies to both Windows 7 and Windows 8. This server uses tunneling protocols from point In the previous article, TipsMake.com mentioned 1 definition, knowledge can be called classics since the time of Internet appearance, it is PROXY. And in this article, we will
In the previous article, TipsMake.com mentioned 1 definition, knowledge can be called classics since the time of Internet appearance, it is PROXY. And in this article, we will DNS servers are an important component for a better web experience, but very few people understand what problems their work or security will cause. Specifically, change DNS to do?
DNS servers are an important component for a better web experience, but very few people understand what problems their work or security will cause. Specifically, change DNS to do? It can be said that one of the most 'problematic' issues in managing and working with Active Directory is mistakenly deleting data or objects accidentally or incorrectly handled by
It can be said that one of the most 'problematic' issues in managing and working with Active Directory is mistakenly deleting data or objects accidentally or incorrectly handled by In the previous article, I showed you how to recover deleted components in Active Directory, which are related to the lifecycle properties of tombstone objects. Technically this
In the previous article, I showed you how to recover deleted components in Active Directory, which are related to the lifecycle properties of tombstone objects. Technically this In the previous sections of the article, we introduced you to some points in the process of configuring Incoming Email with SharePoint 2010, and this time we will continue with the
In the previous sections of the article, we introduced you to some points in the process of configuring Incoming Email with SharePoint 2010, and this time we will continue with the