In fact, there are a lot of Windows Server 2008 tasks that we can do a lot faster with PowerShell than the GUI-based application or tool. In the following article, we will

When it is necessary to deploy a system to ensure safety, stability and flexibility to meet the requirements of businesses and organizations, one of the most selected and applied

In the previous article, I have shown you some of the basic functions and tricks that can be done with PowerShell in Windows Server 2008. And this time, we will continue with part
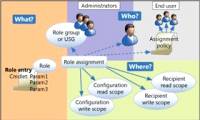
In essence, Microsoft Exchange Server 2010 has been improved and integrated with new Role Based Access Control - RBAC, and this model has provided users with more ways to monitor

In the previous section of the article, we showed you how to set up and configure the level of authorization with RBAC - Role Based Access by deploying Predefined Role Groups via

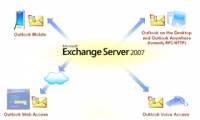
In the following article, we will introduce you some basic characteristics of Security Configuration Wizard - SCW of Exchange Server 2007, with the main purpose of minimizing the

For many of us, using the command line - Command Line to control and use some of the functions in the Windows system will cause them to have headaches and problems. However, if

In the following article, we will introduce and guide you a few basic steps to install and deploy the technology platform that supports virtualization of Hyper-V on Windows Server

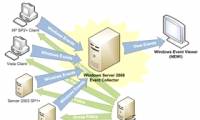
In the following article, I will show you how to use PowerShell to create log records on the system, namely the Write-EventLog cmdlet command. The basic syntax of this command

In the following article, we will introduce you some characteristics, how to implement and apply the Intel Platform Administration Technology platform - IPAT.

After installing Windows Home Server 2011 you need to start configuring it. Part of the configuration work is adding users on the network. This article will show you how to

XenServer is virtualization software launched by Citrix, a company specializing in virtualization technology. Developed on Xen platforms, XenServer supports both Linux and Window

One of the obvious shortcomings of Hyper-V is the ability to monitor virtual machines from Windows PowerShell. Although Microsoft intends to provide this capability on Windows

In this article, we will learn how to access the virtual machine list and see general information about virtual machines with simple PowerShell statements. We will also look at

Cloud computing has emerged in the last few years. The cloud provides infrastructure services (IaaS) that offer unprecedented flexibility as they enable the provision and

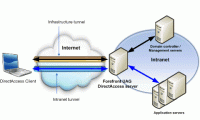
In this section, I will show you some of the key techniques in deploying DirectAccess in that there is no need to upgrade the network infrastructure to IPv6.

Users can install the Hyper-V for Windows Server 8 management tool on the fully installed Windows Server 2008 operating system and on supported versions of Windows Vista Service

In this article, I will show you how to install the basic Service Desk services as well as the data warehouse components of this product.

In Part 3 of this series, I will show you how to use and configure Service Manager.

In this article we will not cover the basic principles of backing up virtual machines, instead we want to focus on backup methods using Windows Server Backup.
 In fact, there are a lot of Windows Server 2008 tasks that we can do a lot faster with PowerShell than the GUI-based application or tool. In the following article, we will
In fact, there are a lot of Windows Server 2008 tasks that we can do a lot faster with PowerShell than the GUI-based application or tool. In the following article, we will When it is necessary to deploy a system to ensure safety, stability and flexibility to meet the requirements of businesses and organizations, one of the most selected and applied
When it is necessary to deploy a system to ensure safety, stability and flexibility to meet the requirements of businesses and organizations, one of the most selected and applied In the previous article, I have shown you some of the basic functions and tricks that can be done with PowerShell in Windows Server 2008. And this time, we will continue with part
In the previous article, I have shown you some of the basic functions and tricks that can be done with PowerShell in Windows Server 2008. And this time, we will continue with part In essence, Microsoft Exchange Server 2010 has been improved and integrated with new Role Based Access Control - RBAC, and this model has provided users with more ways to monitor
In essence, Microsoft Exchange Server 2010 has been improved and integrated with new Role Based Access Control - RBAC, and this model has provided users with more ways to monitor In the previous section of the article, we showed you how to set up and configure the level of authorization with RBAC - Role Based Access by deploying Predefined Role Groups via
In the previous section of the article, we showed you how to set up and configure the level of authorization with RBAC - Role Based Access by deploying Predefined Role Groups via In the following article, we will introduce you some basic characteristics of Security Configuration Wizard - SCW of Exchange Server 2007, with the main purpose of minimizing the
In the following article, we will introduce you some basic characteristics of Security Configuration Wizard - SCW of Exchange Server 2007, with the main purpose of minimizing the For many of us, using the command line - Command Line to control and use some of the functions in the Windows system will cause them to have headaches and problems. However, if
For many of us, using the command line - Command Line to control and use some of the functions in the Windows system will cause them to have headaches and problems. However, if In the following article, we will introduce and guide you a few basic steps to install and deploy the technology platform that supports virtualization of Hyper-V on Windows Server
In the following article, we will introduce and guide you a few basic steps to install and deploy the technology platform that supports virtualization of Hyper-V on Windows Server In the following article, I will show you how to use PowerShell to create log records on the system, namely the Write-EventLog cmdlet command. The basic syntax of this command
In the following article, I will show you how to use PowerShell to create log records on the system, namely the Write-EventLog cmdlet command. The basic syntax of this command In the following article, we will introduce you some characteristics, how to implement and apply the Intel Platform Administration Technology platform - IPAT.
In the following article, we will introduce you some characteristics, how to implement and apply the Intel Platform Administration Technology platform - IPAT. After installing Windows Home Server 2011 you need to start configuring it. Part of the configuration work is adding users on the network. This article will show you how to
After installing Windows Home Server 2011 you need to start configuring it. Part of the configuration work is adding users on the network. This article will show you how to XenServer is virtualization software launched by Citrix, a company specializing in virtualization technology. Developed on Xen platforms, XenServer supports both Linux and Window
XenServer is virtualization software launched by Citrix, a company specializing in virtualization technology. Developed on Xen platforms, XenServer supports both Linux and Window One of the obvious shortcomings of Hyper-V is the ability to monitor virtual machines from Windows PowerShell. Although Microsoft intends to provide this capability on Windows
One of the obvious shortcomings of Hyper-V is the ability to monitor virtual machines from Windows PowerShell. Although Microsoft intends to provide this capability on Windows In this article, we will learn how to access the virtual machine list and see general information about virtual machines with simple PowerShell statements. We will also look at
In this article, we will learn how to access the virtual machine list and see general information about virtual machines with simple PowerShell statements. We will also look at Cloud computing has emerged in the last few years. The cloud provides infrastructure services (IaaS) that offer unprecedented flexibility as they enable the provision and
Cloud computing has emerged in the last few years. The cloud provides infrastructure services (IaaS) that offer unprecedented flexibility as they enable the provision and In this section, I will show you some of the key techniques in deploying DirectAccess in that there is no need to upgrade the network infrastructure to IPv6.
In this section, I will show you some of the key techniques in deploying DirectAccess in that there is no need to upgrade the network infrastructure to IPv6. Users can install the Hyper-V for Windows Server 8 management tool on the fully installed Windows Server 2008 operating system and on supported versions of Windows Vista Service
Users can install the Hyper-V for Windows Server 8 management tool on the fully installed Windows Server 2008 operating system and on supported versions of Windows Vista Service In this article, I will show you how to install the basic Service Desk services as well as the data warehouse components of this product.
In this article, I will show you how to install the basic Service Desk services as well as the data warehouse components of this product. In Part 3 of this series, I will show you how to use and configure Service Manager.
In Part 3 of this series, I will show you how to use and configure Service Manager. In this article we will not cover the basic principles of backing up virtual machines, instead we want to focus on backup methods using Windows Server Backup.
In this article we will not cover the basic principles of backing up virtual machines, instead we want to focus on backup methods using Windows Server Backup.