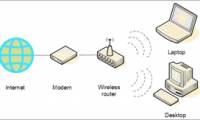
4 steps to set up your home wireless network
you can use the wireless network to share internet access, files, printers ... or you can use it to surf the web even when you're sitting in bed or in the garden.

you can use the wireless network to share internet access, files, printers ... or you can use it to surf the web even when you're sitting in bed or in the garden.

the article introduces you to some of the tools used in wi-fi networks: search engines and roaming security (roaming security) ...

in this article, i will show you some useful techniques for troubleshooting wireless network security issues at the packet level.
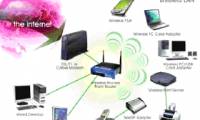
in this article we have introduced some ways to prevent, or in other words, restrict wireless access, to secure some wi-fi networks.

in this article we will show you the process of connecting bluetooth devices in windows 7 as well as giving you precautions for unexpected problems that may occur.

in the following article, we will explore and discuss the features and uses of some familiar network devices such as switches, hubs, routers ... what is the main function of the

in this article, i will show you a list of 10 trends predicted about what will happen to the internet in this decade.

intel is partnering with asustek computer and acer on plans to produce new netbooks that cost less than $ 199 for the middle east, latin america and eastern europe markets.
in the twentieth century, the lack of network was almost like blocking all information about life, and all the need to communicate about the work of a diligent employee.