In the process of removing the Avast antivirus program to reinstall or install another antivirus program on the computer, users often encounter the error message Setup is already

Like other programs and antivirus applications, in the process of using Kaspersky Internet Security software, Kaspersky will store temporary files in a folder hidden deep in the

What is Bloatware? Why remove Bloatware from the device? This article will provide you with the most basic knowledge about Bloatware and how to remove Bloadware from the system.

In some cases when opening Windows Defender you receive an error message: Windows Defender has been turned off, and it is not monitoring your computer.

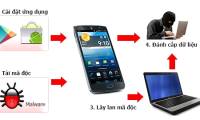
Viruses can be illegally hacked into users' computers through various ways, such as during Web browsing, or from USB devices or during the installation of applications and

URL: Mal is one of the most dangerous DNS related to advertising platform. It has the address is Http://107.170.47.181. URL: Mal is created by free software from unwanted

Why not try to troll your friends with 'viruses', try creating a fake virus then send it to your friends. Surely your friends will have to 'roar' when they know their computer is

Once the computer is compromised, the virus can cause a variety of problems such as slowing down the computer operating system, and even some viruses that can steal user data.

What should I do when I see the computer being infected? Read the article below to learn how to respond when you see the virus message being detected on your computer.

Most users have the same opinion that they have installed anti-virus programs and software on their computers, so viruses can hardly attack their computers. However this is a

Technically, PUP.Tuto4PC is not a virus, but it contains a lot of malware such as rootkits that can dig into your operating system, browser hijacking, .... The industry generally

ExtTag.exe and ExtTags.exe are malicious adware programs that are installed in addition to plugins (toolbars, extensions or add-ons) on your Web browser to redirect you to other

Malicious programs are often written to operate on a certain operating system, however, a newly discovered type of spyware (spyware) is attacking computers from mobile phones.

A new study shows that people can transfer data between non-networked laptops via the air by using high-frequency audio signals.

If Windows is infected with a virus or malware, running an antivirus program from within Windows is often not very effective. You can find and remove viruses as well as malware by

Anti-virus software company AVG has discovered a type of malware (only affects Android phones) that can trick users into thinking they have shutdown. When the user clicks on the

Security firm Bluebox has discovered a few malicious applications that have been pre-installed on Xiaomi Mi 4, they are a Google application aimed at advertising and trojans,

According to security researchers at Cisco, a new type of malware called Rombertik has just been discovered that can destroy itself important data stored in Windows system files on

The battle between cybercrime and security has entered a new phase with the emergence of Rombertik, a malware (malware) capable of capturing packets to collect personal data while

Graphics processing chips (GPUs) are known to have much higher computing power than the main processor chips (CPUs). If used for good purposes, the GPU will be very beneficial.
 In the process of removing the Avast antivirus program to reinstall or install another antivirus program on the computer, users often encounter the error message Setup is already
In the process of removing the Avast antivirus program to reinstall or install another antivirus program on the computer, users often encounter the error message Setup is already Like other programs and antivirus applications, in the process of using Kaspersky Internet Security software, Kaspersky will store temporary files in a folder hidden deep in the
Like other programs and antivirus applications, in the process of using Kaspersky Internet Security software, Kaspersky will store temporary files in a folder hidden deep in the What is Bloatware? Why remove Bloatware from the device? This article will provide you with the most basic knowledge about Bloatware and how to remove Bloadware from the system.
What is Bloatware? Why remove Bloatware from the device? This article will provide you with the most basic knowledge about Bloatware and how to remove Bloadware from the system. In some cases when opening Windows Defender you receive an error message: Windows Defender has been turned off, and it is not monitoring your computer.
In some cases when opening Windows Defender you receive an error message: Windows Defender has been turned off, and it is not monitoring your computer. Viruses can be illegally hacked into users' computers through various ways, such as during Web browsing, or from USB devices or during the installation of applications and
Viruses can be illegally hacked into users' computers through various ways, such as during Web browsing, or from USB devices or during the installation of applications and URL: Mal is one of the most dangerous DNS related to advertising platform. It has the address is Http://107.170.47.181. URL: Mal is created by free software from unwanted
URL: Mal is one of the most dangerous DNS related to advertising platform. It has the address is Http://107.170.47.181. URL: Mal is created by free software from unwanted Why not try to troll your friends with 'viruses', try creating a fake virus then send it to your friends. Surely your friends will have to 'roar' when they know their computer is
Why not try to troll your friends with 'viruses', try creating a fake virus then send it to your friends. Surely your friends will have to 'roar' when they know their computer is Once the computer is compromised, the virus can cause a variety of problems such as slowing down the computer operating system, and even some viruses that can steal user data.
Once the computer is compromised, the virus can cause a variety of problems such as slowing down the computer operating system, and even some viruses that can steal user data. What should I do when I see the computer being infected? Read the article below to learn how to respond when you see the virus message being detected on your computer.
What should I do when I see the computer being infected? Read the article below to learn how to respond when you see the virus message being detected on your computer. Most users have the same opinion that they have installed anti-virus programs and software on their computers, so viruses can hardly attack their computers. However this is a
Most users have the same opinion that they have installed anti-virus programs and software on their computers, so viruses can hardly attack their computers. However this is a Technically, PUP.Tuto4PC is not a virus, but it contains a lot of malware such as rootkits that can dig into your operating system, browser hijacking, .... The industry generally
Technically, PUP.Tuto4PC is not a virus, but it contains a lot of malware such as rootkits that can dig into your operating system, browser hijacking, .... The industry generally ExtTag.exe and ExtTags.exe are malicious adware programs that are installed in addition to plugins (toolbars, extensions or add-ons) on your Web browser to redirect you to other
ExtTag.exe and ExtTags.exe are malicious adware programs that are installed in addition to plugins (toolbars, extensions or add-ons) on your Web browser to redirect you to other Malicious programs are often written to operate on a certain operating system, however, a newly discovered type of spyware (spyware) is attacking computers from mobile phones.
Malicious programs are often written to operate on a certain operating system, however, a newly discovered type of spyware (spyware) is attacking computers from mobile phones. A new study shows that people can transfer data between non-networked laptops via the air by using high-frequency audio signals.
A new study shows that people can transfer data between non-networked laptops via the air by using high-frequency audio signals. If Windows is infected with a virus or malware, running an antivirus program from within Windows is often not very effective. You can find and remove viruses as well as malware by
If Windows is infected with a virus or malware, running an antivirus program from within Windows is often not very effective. You can find and remove viruses as well as malware by Anti-virus software company AVG has discovered a type of malware (only affects Android phones) that can trick users into thinking they have shutdown. When the user clicks on the
Anti-virus software company AVG has discovered a type of malware (only affects Android phones) that can trick users into thinking they have shutdown. When the user clicks on the Security firm Bluebox has discovered a few malicious applications that have been pre-installed on Xiaomi Mi 4, they are a Google application aimed at advertising and trojans,
Security firm Bluebox has discovered a few malicious applications that have been pre-installed on Xiaomi Mi 4, they are a Google application aimed at advertising and trojans, According to security researchers at Cisco, a new type of malware called Rombertik has just been discovered that can destroy itself important data stored in Windows system files on
According to security researchers at Cisco, a new type of malware called Rombertik has just been discovered that can destroy itself important data stored in Windows system files on The battle between cybercrime and security has entered a new phase with the emergence of Rombertik, a malware (malware) capable of capturing packets to collect personal data while
The battle between cybercrime and security has entered a new phase with the emergence of Rombertik, a malware (malware) capable of capturing packets to collect personal data while Graphics processing chips (GPUs) are known to have much higher computing power than the main processor chips (CPUs). If used for good purposes, the GPU will be very beneficial.
Graphics processing chips (GPUs) are known to have much higher computing power than the main processor chips (CPUs). If used for good purposes, the GPU will be very beneficial.