Learn about Permission and Role Based Access Control - RBAC (part 1)
TipsMake.com - In essence, Microsoft Exchange Server 2010 has been improved and integrates more functions to assign Role Based Access Control - RBAC , and this model has provided users with more ways to monitor , initialize and assign rights to different admin accounts . And these assigned roles will reflect the job of the administrator in the actual operating model.
Before Exchange Server 2010, Microsoft Exchange administrators took care of creating new admin accounts, assigning permissions to existing accounts, which were often quite difficult while deciding which Administrator group to apply. Each group of Administrators contains many different permissions levels, and older Exchange versions only have very few Admin groups to choose from. And so, the only solution is to assign those accounts with decentralized levels that are not really relevant in the system.
Role Group and Role:
To continue, we need to understand and grasp the basic concept in RBAC as an association between the group role, role, cmdlet (commandlet) and parameter.
First, the role can be considered a combination of tasks that an administrator account can perform. For example, the Mail Recipients role allows the Administrator account to manage mailboxes, mail users and mail contacts . When an administrator account is assigned a role, it means the corresponding authorization level of that role . And the act of assigning permissions to perform certain tasks we can understand is by giving access to the cmdlet or parameter associated with those tasks.
In some special cases, an Admin account can be assigned with different roles. And technically, we can put the roles together, sort them into groups - aka the role group , then instead of assigning multiple roles to some account, we just need to replace with the appropriate role group respectively.
By contrast, users can assign multiple members of Administrator group to a role group . This means that all accounts in that Admin group will perform all the same roles , and will have access to the cmdlets and parameters in that role .
Predefined Role Groups and Roles:
There is also a Predefined Role Group in Exchange 2010 that we can use instead of RBAC without understanding the specific features and how RBAC works.
If you include all the Predefined Role Groups (or called Predefined Universal Security Groups ) then there will be 16 components in total. However, only 11 of them are actually used for RBAC , and the rest is used directly by Exchange . In this article, we will mainly focus on the RBAC role groups.
The Predefined Role Group used in Exchange Server 2010 Role Based Access Control:
- Delegated Setup : for administrators who need to deploy Exchange 2010 server model provided by the Organization Management role group.
- Discovery Management : for Admin accounts that want to search data in the mailbox system based on priority information as well as mailbox configuration settings.
- Help Desk : is used to check general information and change options of Microsoft Office Outlook Web App.
- Hygiene Management: changing security regime in Exchange.
- Organization Management: for admin accounts that want to have full access to all Exchange 2010 systems.
- Public Folder Management: used to manage public folders and databases on servers using Exchange 2010.
- Recipient Management: manage and monitor the recipient of Exchange 2010.
- Records Management : is often applied to configure and set up features such as policy classification, notifications and data transfer rules.
- Server Management : for administrators who want to set up server transport mode in a separate way, Unified Messaging - UM, access from client and mailbox.
- UM Management : used to manage server configuration steps related to UM, mailbox properties, warning information .
- View-Only Organization Management : to view and check the properties of any object in Exchange.
Predefined Role:
First, open Exchange Management Console , in the left pane, select Toolbox , scroll down and click Role Based Access Control (RBAC) as shown below:
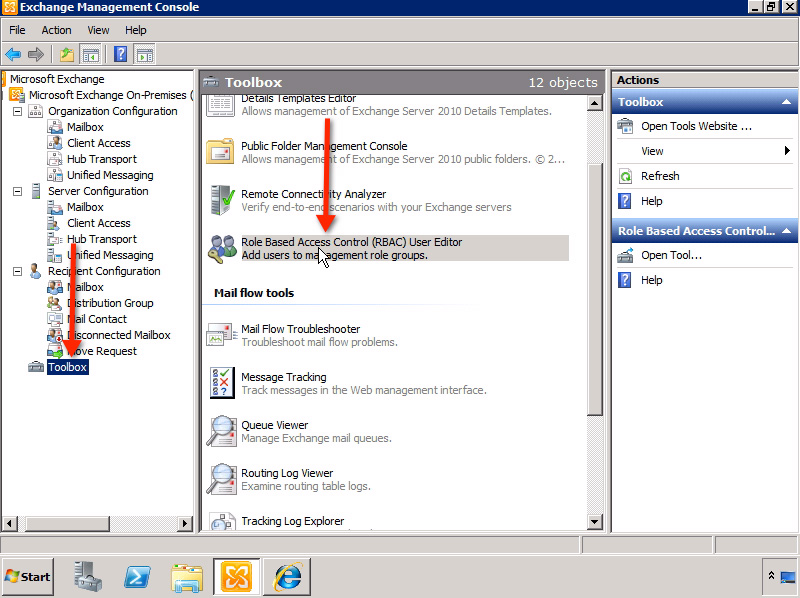
You will be taken to the next Exchange Control Panel , where the system will ask the user to login. Then, open Administrator Roles:
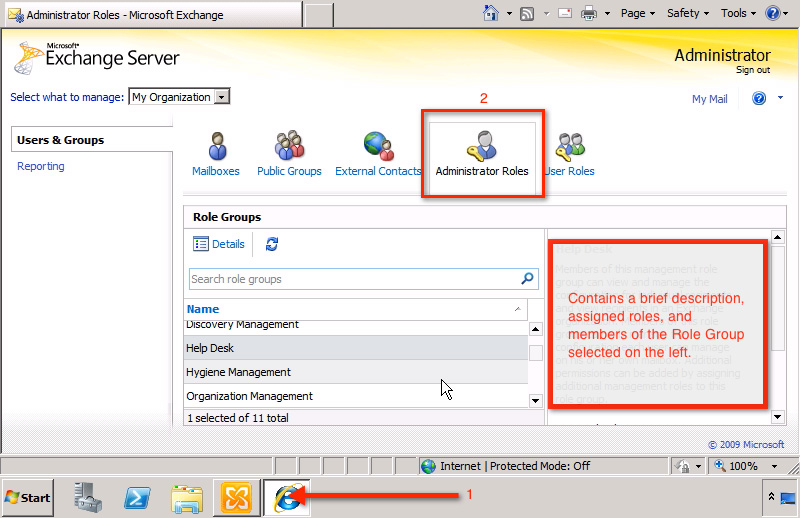
Under Role Groups , you'll see the full 11 Predefined Role Groups mentioned above. And each time you select any role, the system displays the Description information of the assigned role (also called Assigned Roles ), the administrative accounts assigned to those roles (called Members ) will be displayed at right window part.
If you want to assign 1 Member to Predefined Role Group, you just need to double-click the corresponding Predefined Role Group section in the list. For example, when selecting Discovery Management , the system will display the main control window as shown below:
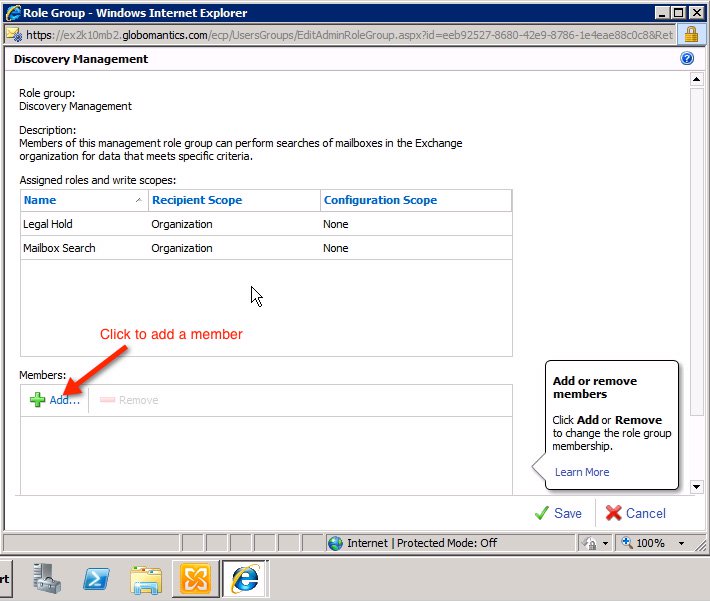
Here, we will see the name of the role group (in this example, Discovery Management ) - the brief description of the role and Assigned Roles role , as well as the member list at the bottom of the display window ( usually empty). To add a member, click the Add button as the screenshot above.
In the next window, find and select the name of the Admin account to assign, then click the OK button:
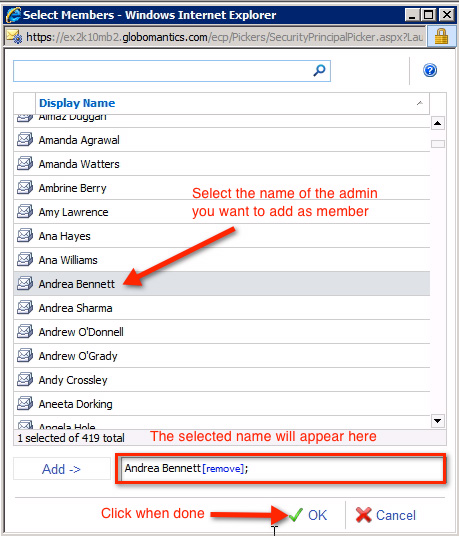
We will see the newly assigned member in the Members box as shown below:
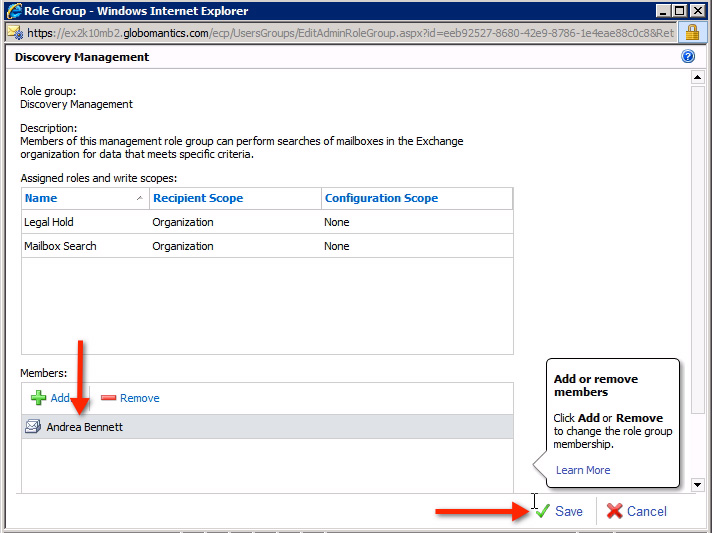
If you want to assign more accounts, do the same thing as above, click Finish when done. However, it should be noted that not only can you assign multiple role group member accounts to the role group, but also assign multiple role roles to a single Admin account. And this process will be done within Administrator Roles:
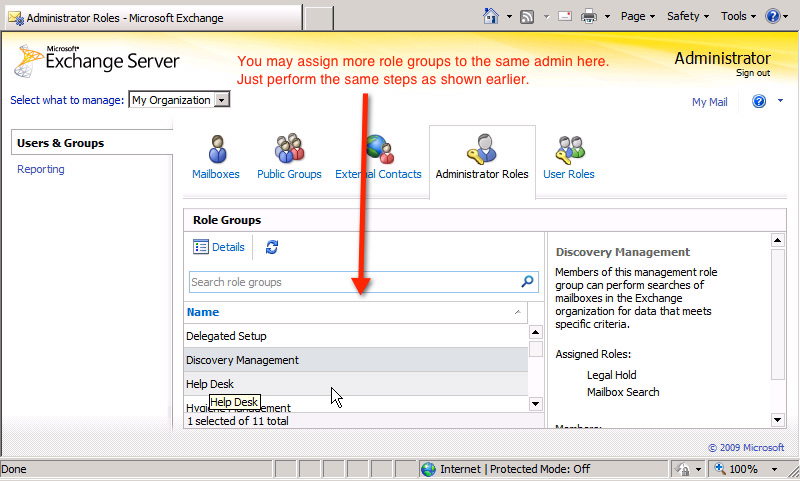
Working mechanism of RBAC:
Before concluding this article, let us review RBAC's working mechanism through an illustration - often called Triangle of Power:
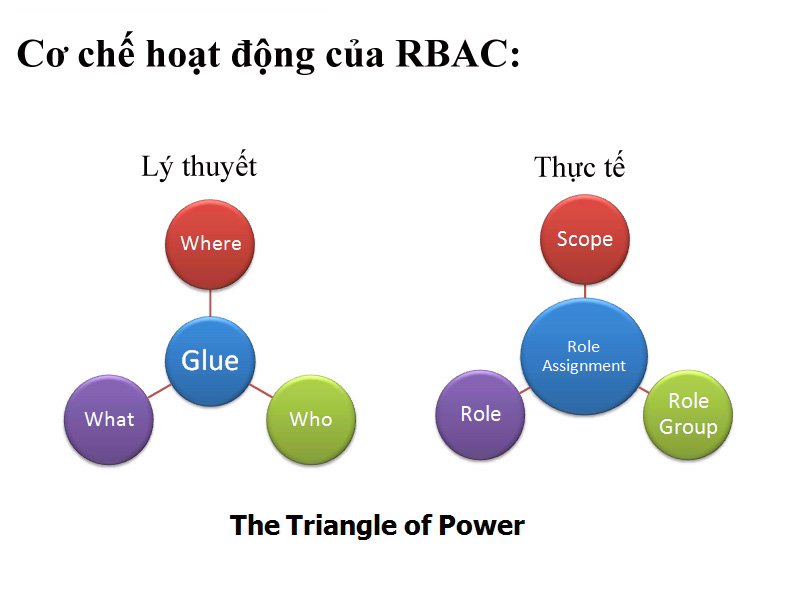
This model is built from 4 main components: Where , What , Who , and Glue . Inside:
- Where or Scope represents objects, tasks from specific roles assigned to supported objects, such as an individual user account, a user group, or the entire model, organization.
- What or Role corresponds to what the role can do. In fact, Exchange Server 2010 has a total of 65 roles for users.
- Who or Role Group as we mentioned earlier, is just a combination of multiple roles arranged together. We can combine with Scope to create a complete Role Assignment object.
As mentioned above, using predefined role groups of RBAC can simplify the process of delegating administrative rights to many different Administrator accounts. However, what we have just discussed above is just an extension of the process of decentralization through RBAC.
But what if we want the administrator account to set up the transport rule but not to affect the retention or message rule? Obviously, assigning that account to the Records Management rule group will not meet the demand because the system will assign more permissions than necessary. We will explore this issue together in Part II of this article.
Good luck!
You should read it
- ★ Additions for Exchange Server 2007 - Part 1: Introduction steps
- ★ Install Role, configure role on Windows Server 2012
- ★ Discover EMC in Exchange Server 2010 (Part 2)
- ★ Learn about Server role, Role service and Feature on Windows Server
- ★ Analysis of disaster recovery perspective and high availability of Exchange Server