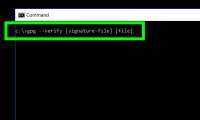
How to Verify a GPG Signature
this how-to explains a clear and step-by-step, 1-minute process to verify that a file in your possession was digitally signed by a particular gpg secret key and has been unmodified

this how-to explains a clear and step-by-step, 1-minute process to verify that a file in your possession was digitally signed by a particular gpg secret key and has been unmodified
this wikihow teaches you how to bypass web restrictions on library computers. while library computers will severely limit your ability to modify or use your computer's system
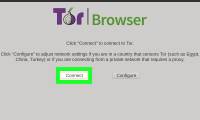
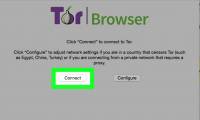
this wikihow teaches you how to download and install the tor browser on your linux computer. open the tor website. go to https://www.torproject.org/projects/torbrowser.html in your

facebook is not something that you usually associate with an anonymous browser. but, did you know that facebook operates the onion version of the website on the tor network?

the problem of anonymity and evading the control of the authorities on the internet has been known for a long time. many virtual tools and networks are designed to serve this

hackers use different ways to remain anonymous while hacking, but it must be said that anonymity is completely unthinkable, but hackers can be safe and anonymous to some degree and
with the tips in this article, you will use tor's anonymous browser in the safest way

when did you last try a new browser? read this article and choose for yourself the best web browser!

tor project has released a security patch for tor browser on mac and linux to patch the vulnerability of revealing users' true ip address.

tor project is bringing big changes to its infrastructure to increase security and privacy for users on the onion network.