Protect the terms of BitTorrent users
QuanTriMang.com - Whenever you connect to the Internet, security is always a top priority. And in fact, for those who use BitTorrent, the risk is twice higher here than usual . In the article below, TipsMake.com will introduce you how to protect yourself in this large and diverse world.
The dangers are always lurking
In order to understand the hazards mentioned below, we will conduct sorting and sorting them according to certain criteria. Viruses and other types of malware are the most common and common threats. When downloading data from unknown sources, scan the virus carefully after completing the download process. Besides, you should not be too surprised when your IP address is easily detected and tracked, if many people use it without serious problems, does not mean that you have nothing to do. worry. In case someone has an intervention and a link to your IP address, the download process will have problems. In addition, the case of bad traffic happens - that is when the peer intentionally sends corrupted data in response to signals from BitTorrent, forcing other users to reload that data.

Data encrypt
A simple way to reduce these risks is to enable encryption mode with your connection. This feature ensures that data is transferred back and forth between two peers without fear of being looked at by others, while other information such as IP address, tracker related information, and data traffic has been sent. . still can be watched.
Anyway, this is still not the best option. Because this feature must also be activated on the side of your peer. Not to mention some tracker systems do not allow data encryption, but if you still want to use it, enable preferring encrypted connections mode.
Use Encryption mode in uTorrent
Open uTorrent, in Options> Preferences> BitTorrent, select Enabled in Protocol Encryption , and check the Allow incoming legacy connections box:
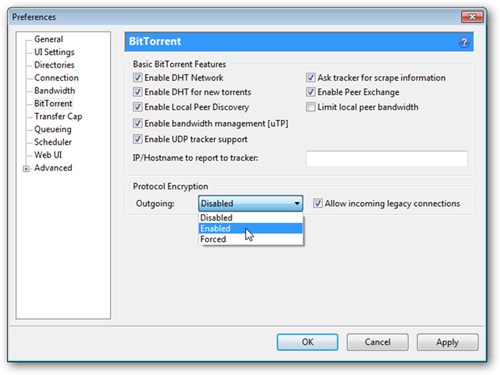
This allows you to encrypt the signals that are sent but still accept unencrypted connections when there are no longer any encrypted signals in your connection.
Encryption feature of Transmission
Same as above, open Transmission and select Edit> Preferences (in Linux) or Transmission> Preferences (with Mac OS X), select the Privacy tab:
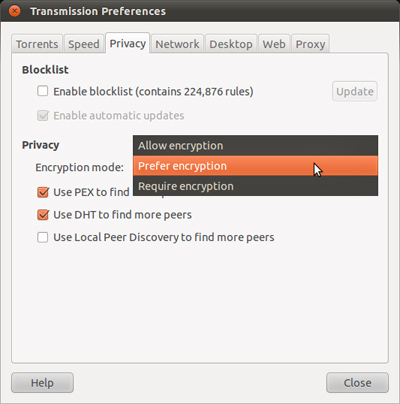
Here, select the line Prefer encryption to accept unencrypted connections.
Use IP blocking programs
Another possible way is to block IP - programs that can work with the system's Firewall, the BitTorrent client program will filter IP addresses based on the list. These lists are built by analyzing IP address ranges that are deemed to be problematic, such as tracking actions or sending out bad signal packets. If you are a cautious person, use IP blocker if necessary. The most popular applications today are PeerBlock for Windows and Moblock of Linux, or Transmission also has the ability to block IP.
Install and set up PeerBlock on Windows
Access and download the latest PeerBlock version here:
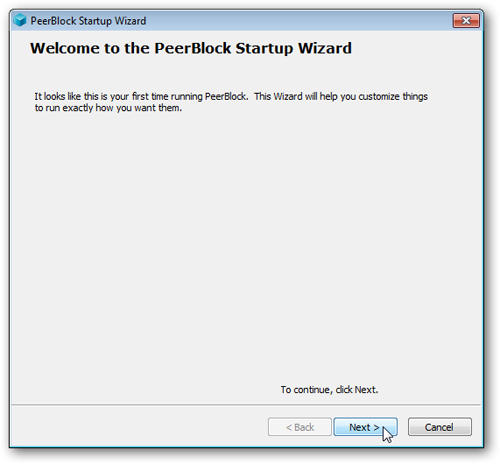
At the end of the installation process, you need to set up PeerBlock , click the Next button at the next window:
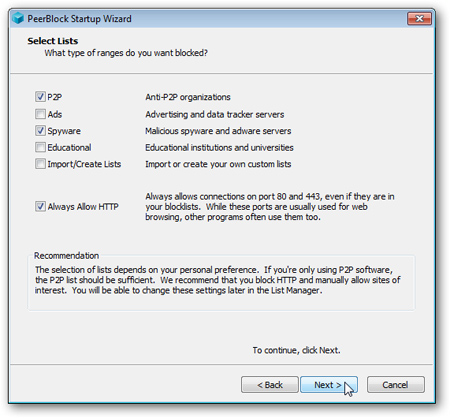
Here, you can choose the type of list to prevent, for example, P2P , select Always Allow HTTP if you are not sure about this program, then click Next:
Next is the update mode, keeping the default settings and Next:
Then, the program will display a popup window and how the list selected above. When the automatic update process ends, click Close:

Back to PeerBlock's main screen, you can review the entire list of banned addresses, manage, add and remove components, check, update .
Block IP on Linux and Mac OS X
Moblock - with many advanced and complex features for users, despite the graphical interface of Mobloquer, the installation and setup are not simple. Moreover, the program only works on Linux, with Mac OS X, there are not many software that can fulfill the above functions. But in return there was Transmission - in addition to the basic features, this application can optimize connections and block prohibitive lists quite easily.
Open Transmission> Edit> Preferences (on Linux) or Transmission> Preferences (with Mac OS X), select the Privacy tab:
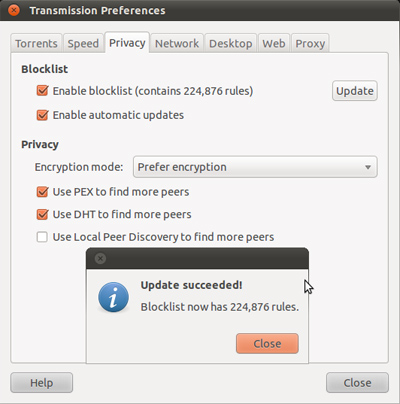
Check the checkbox Enable blocklist and Enable automatic updates, then click Update . Transmission will automatically download, update and display newly established rules.
Private Tracker
Be careful because you don't know for sure who or what is waiting for you outside! But if you have reliable data sources, everything will be different, which is why everyone chooses to use a private tracker, for the following reasons:
- The community is fully self-contained, highly confidential and reliable : want to participate and use resources here, everyone must register and strictly abide by the rules set forth. If the violation is committed, your account will be banned. In the other case, the referral will be punished. So be assured when you agree to join the tracker system privately, and be careful because no one wants to be penalized or excluded from the community.
- Strict rules : only approved and allowed certain modes of operation. This greatly reduces the percentage of fake users, while ensuring that the connection is always guaranteed and optimizing speed.
- Standards to be followed : if you want to upload data, you must achieve certain quality and size, for example for music or video, to ensure safety when scanning with popular antivirus programs.
- Rate : each participant is required to keep a certain ratio between upload and download, this unit is calculated in MB.
With the above rules, users will be more secure when participating in private tracker community, but depending on each opening phase, they can register and use. If you are a careful person, try to combine the above methods to give yourself a unique 'strategy'. Besides, it is impossible not to pay attention to security applications on operating system, usage habits and some other subjective factors.