Microsoft Forefront TMG - Forefront TMG SDK
In this article, I will show you how to use the Forefront TMG SDK tools to expand Forefront TMG functions and some information that the SDK provides about Forefront TMG work. .
Forefront TMG 2010 SDK includes libraries, tools, templates, and documents to help developers and system administrators deploy, configure, customize, and expand their Forefront TMG environment . You can download Forefront TMG SDK for free from here.
There are many tools that you can download but we will look through some important tools. Let's start with ADAM Sites for Forefront TMG Enterprise.
ADAM Sites tool for Forefront TMG Enterprise
The ADAM Sites tool is used to define AD-LDS (Active Directory Lightweight Directory Service) sites for the purpose of controlling traffic between Forefront TMG Enterprise Management Server (EMS). The Enterprise Management Server is the server used to manage the TMG Enterprise Array or it can even be a standalone server. The Forefront TMG uses EMS will receive the configuration from this EMS server. By default, the EMS server is not aware of the site, so if you have multiple EMS servers in multiple locations, there is no way to control the replication interval and the costs used by the federation. This link. The ADAM Sites tool allows you to define AD-LDS site links, combining costs and replication time intervals between these links. Before you can use the ADAM Sites tool, you need to copy the ADAMSITES.EXE file to the Forefront TMG installation directory. The following figure shows the command line options of ADAM Sites.
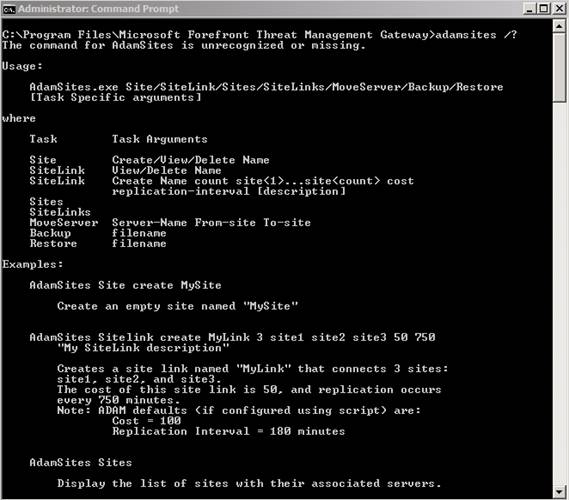
Figure 1: ADAMSITES tool
Auto Discovery Configuration
Auto-Discovery Configuration can be used to configure Active Directory with a marker key that points to your Forefront TMG server. This marker key is used by the TMG client (formerly the Firewall client) to locate the Forefront TMG server and connect to it. This is a completely different and safer method than using DHCP / DNS in finding Forefront TMG servers. If no marker for the Active Directory key is found, the Forefront TMG client will return to using DHCP / DNS to find the Forefront TMG server.
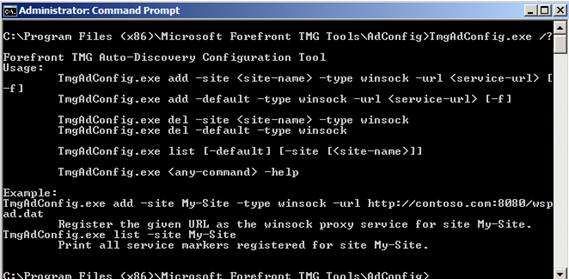
Figure 2: TMG Auto-Discover Tool
Cache Directory
Using Cache Directory can view the cache contents in real time, save the current cache information to the file and mark the obsolete items that should not be stored in the cache. Cachedir utility in our opinion is the most desirable utility from the Forefront TMG SDK and is also available in the previous ISA Server version. Before you can use this Cachedir tool, you need to copy the CACHEDIR.EXE file to the Forefront TMG installation directory.
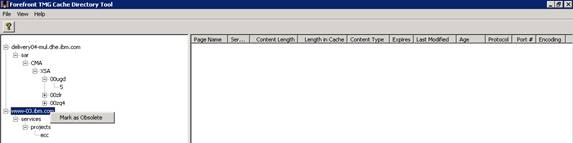
Figure 3: CacheDir Tool
CertTool
Certtool for TMG is only required when you use Forefront TMG Enterprise in a workgroup environment. In a workgroup environment, TMG servers communicate with each other using certificates. Certtool makes it easy to enforce installation or replace certificates in Forefront TMG. Before using Certtool for TMG, you need to copy the ISACERTTOOL.EXE file to the Forefront TMG installation directory.
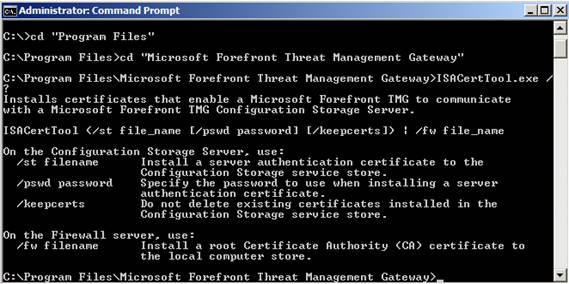
Figure 4: ISACerttool
DNS Cache
Using the DNS Cache on the Forefront TMG server can display the contents of the Domain Name System (DNS) cache and delete entries in the DNS cache. For example, Forefront TMG clients use Forefront TMG DNS settings for name resolution, and Secure NAT clients use local DNS settings to resolve names. In some cases it may be necessary to delete the DNS Cache settings on Forefront TMG.
Note : Deleting the DNS cache on the TMG server with the IPCONFIG / FLUSHDNS command will only delete the DNS Cache from the DNS client resolver.
To be able to use the DNS Cache tool, copy the DNSTOOLS.EXE file to the Forefront TMG installation directory.
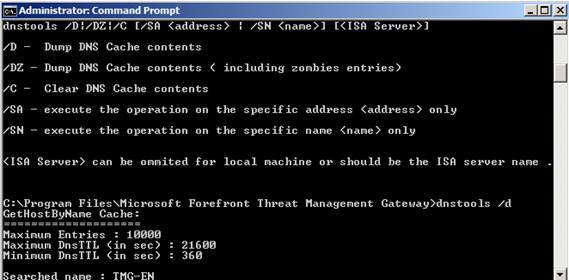
Figure 5: TMG DNSCache Tool
EE Single Server Conversion
Using this tool (EESingleServerConversion.exe) can help you switch from an independent server running ISA Server 2004 Enterprise Edition or ISA Server 2006 Enterprise Edition to Forefront TMG also in standalone mode. Before importing the configuration of ISA Server Enterprise into Forefront TMG Enterprise in standalone mode, Standalone Mode, you must convert other XML settings from the export format of the ISA Server into a readable format for importing the configuration into Forefront TMG Enterprise. After installing this converter and copying the ISA Enterprise configuration file to the Forefront TMG server, open the command prompt and enter the command with the source and target XML file as shown in the figure below.
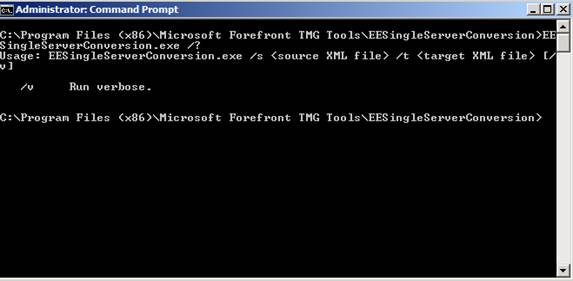
Figure 6: ISA to TMG Single Server conversion tool
This command will convert the ISA Server Enterprise configuration file to the supported format on Forefront TMG Enterprise independently.
MSDEToText
The MSDEtoText tool can be used to convert Forefront TMG SQL Express Server logs into a text file, or to display their contents so the screen. You can use the MSDEtoText utility with ISA Server 200x and Forefront TMG. The following figure shows the syntax of the MSDEtoText tool.
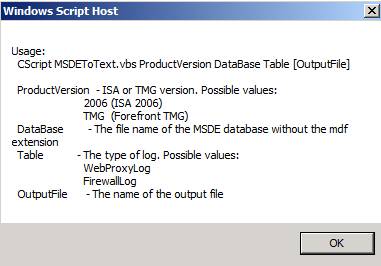
Figure 7: MSDE to Text conversion tool
The figure below shows an example of exporting the Firewall log file.
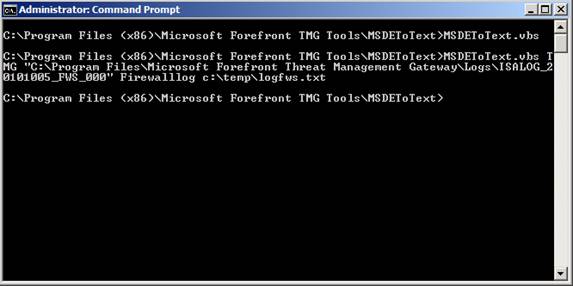
Figure 8: An example of an MSDE to Text converter
Remote Access Quarantine
Forefront TMG also supports the Remote Access Quarantine service, the service used in ISA Server 200x, to quarantine VPN clients connected to ISA Server. You should use NAP (Network Access Protection) of Windows Server 2008 in combination with Forefront TMG, which allows you to more easily and flexibly configure RQS components from the TMG SDK.
Figure 9: RQS tool
RSA Test Authentication
The RSA Test Authentication utility can be used to verify that a computer running Forefront TMG can authenticate to a computer running RSA Authentication Manager. To use the RSA Test Authentication utility, copy the SDTEST.EXE and SDUI.DLL files to the Forefront TMG installation directory.
Figure 10: RSA SecurID Authentication tool
Upgrade the Security Configuration Wizard (SCW) for Forefront TMG Standard and Enterprise versions
Windows Server 2008 and Windows Server 2008R2 have integrated a tool called the Security Configuration Wizard (SCW). This tool can be used to simplify the task of "hardening" the underlying operating system during preparation of deploying Forefront TMG. The SCW will create a policy to configure services, registry settings, authentication policies, and . based on the roles and features installed. By default, SCW does not know that Forefront TMG is installed. The Forefront TMG SDK comes with an extension of SCW.
There are two files to be copied into the WindowsSecurityMsscwkbs folder:
- SCW_TMG_W2K8R2_SP0.XML
- SCW_TMGEMS_W2K8R2_SP0.XML
Then open the command prompt and enter the following command: scwcmd register / kbname: TMG /kbfile:SCW_TMG_W2K8R2_SP0.xml
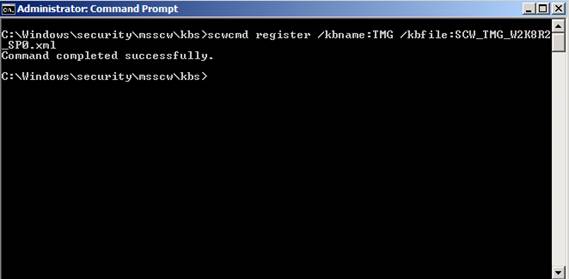
Figure 11: TMG SCW tool
Then create a new Security policy and the SCW will see the roles installed on the Forefront TMG server.
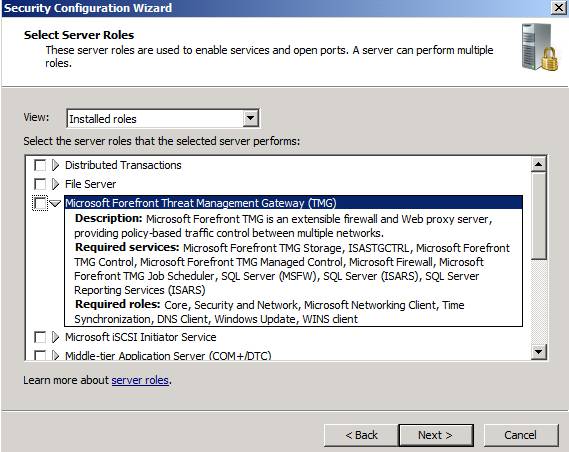
Figure 12: SCW with the TMG role
Forefront TMG 2010 SDK
Forefront TMG SDK has a useful ISASDK.CHM file, which contains a lot of technical information about Forefront TMG and some examples to develop Application and Web filters in Forefront TMG.
ISASDK.CHM
The ISASADK.CHM file contains information about the Forefront TMG architecture and its subsystems, as well as some example code that helps configure and extend programming capabilities for Forefront TMG.
Figure 13: Support documentation of TMG SDK
Samples / Admin directory
There are many useful VBS scripts in the samples / Admin directory installed by the Forefront TMG SDK installation routine. In this article, we will show you two examples. The first scenario is HTTPFilteconfig.vbs, the script can be used to import or export HTTP filter settings from a firewall policy policy.
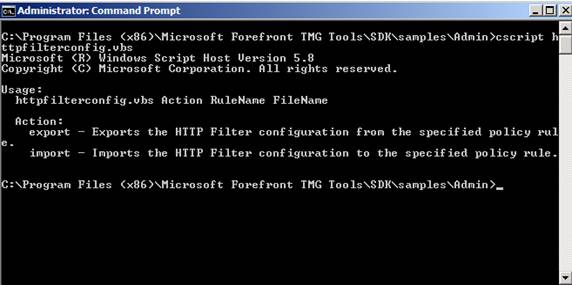
Figure 14: TMG SDK sample script to export HTTP Filter
Another script is called ActiveSession.vbs, which gives you an overview of the current connection sessions on Forefront TMG.
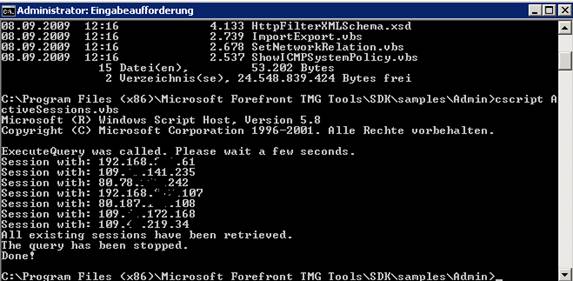
Figure 15: TMG SDK sample script to display Active Session