Let's take a look at the major threats to personal information on social networks as well as in the advertising content on the Internet.

What do you do when you have to send sensitive information to someone, while snailmail is not fast enough for your request?

In this article we will introduce you some basic knowledge needed to secure Windows 7 properly, help you achieve basic security ...

There are many ways to protect your data in case you need to access public Wi-Fi networks

NetBackup 7 is a data duplication solution that protects new virtual servers and integrates backup replication capabilities to help recover from disaster faster ..,

In Part 2 of this series, I will continue the discussion by showing you how to secure Windows 7 and introduce some less-known security features.

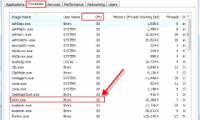
In Windows operating system there are many strange applications and processes that most people don't know what it is. What does it function, how does it work, how much system

In the next part of this series, we will introduce you to SSL spoofing attacks, besides some theories under SSL connections and what is safe.

If you are using Windows XP or Windows Server 2003, you must upgrade your registry - or someone can run software or commands on your computer as if they were friends.

Have you ever forgotten your WEP or WPA key or password for your Wi-Fi network? In this tutorial we will show you how to fix it

In this tutorial we will introduce some simple ways for you to choose what information you should distribute when using different Googl products.

In this tutorial we will show you how to set up some restrictions to protect young children safely when they are online.

AT & T's recent data flaw has emphasized the need for iPad security precautions. Some simple steps can help protect data confidentially.

To address future privacy issues, Facebook has launched the 'Facebook and Privacy' page, which will regularly upgrade changes to privacy options.

In this tutorial we will introduce general knowledge about DNSSEC and the reasons why securing DNS infrastructure is important to your organization.

Protecting a networked computer is a challenge that never has an end - even in Linux.

If you don't set up wireless network protection from hackers, you may have to stop using the network. This also affects some other wireless networks.

Normally, under the hands of well-trained users, a properly configured Mac computer will not have many security risks.

In this article we will show you how to use BitLocker-to-go to avoid exposing important data by encrypting an external storage drive.

On April 20, Google received a letter from 10 countries around the world asking the firm to search for this giant to enhance security services for users.
 Let's take a look at the major threats to personal information on social networks as well as in the advertising content on the Internet.
Let's take a look at the major threats to personal information on social networks as well as in the advertising content on the Internet. What do you do when you have to send sensitive information to someone, while snailmail is not fast enough for your request?
What do you do when you have to send sensitive information to someone, while snailmail is not fast enough for your request? In this article we will introduce you some basic knowledge needed to secure Windows 7 properly, help you achieve basic security ...
In this article we will introduce you some basic knowledge needed to secure Windows 7 properly, help you achieve basic security ... There are many ways to protect your data in case you need to access public Wi-Fi networks
There are many ways to protect your data in case you need to access public Wi-Fi networks NetBackup 7 is a data duplication solution that protects new virtual servers and integrates backup replication capabilities to help recover from disaster faster ..,
NetBackup 7 is a data duplication solution that protects new virtual servers and integrates backup replication capabilities to help recover from disaster faster .., In Part 2 of this series, I will continue the discussion by showing you how to secure Windows 7 and introduce some less-known security features.
In Part 2 of this series, I will continue the discussion by showing you how to secure Windows 7 and introduce some less-known security features. In Windows operating system there are many strange applications and processes that most people don't know what it is. What does it function, how does it work, how much system
In Windows operating system there are many strange applications and processes that most people don't know what it is. What does it function, how does it work, how much system In the next part of this series, we will introduce you to SSL spoofing attacks, besides some theories under SSL connections and what is safe.
In the next part of this series, we will introduce you to SSL spoofing attacks, besides some theories under SSL connections and what is safe. If you are using Windows XP or Windows Server 2003, you must upgrade your registry - or someone can run software or commands on your computer as if they were friends.
If you are using Windows XP or Windows Server 2003, you must upgrade your registry - or someone can run software or commands on your computer as if they were friends. Have you ever forgotten your WEP or WPA key or password for your Wi-Fi network? In this tutorial we will show you how to fix it
Have you ever forgotten your WEP or WPA key or password for your Wi-Fi network? In this tutorial we will show you how to fix it In this tutorial we will introduce some simple ways for you to choose what information you should distribute when using different Googl products.
In this tutorial we will introduce some simple ways for you to choose what information you should distribute when using different Googl products. In this tutorial we will show you how to set up some restrictions to protect young children safely when they are online.
In this tutorial we will show you how to set up some restrictions to protect young children safely when they are online. AT & T's recent data flaw has emphasized the need for iPad security precautions. Some simple steps can help protect data confidentially.
AT & T's recent data flaw has emphasized the need for iPad security precautions. Some simple steps can help protect data confidentially. To address future privacy issues, Facebook has launched the 'Facebook and Privacy' page, which will regularly upgrade changes to privacy options.
To address future privacy issues, Facebook has launched the 'Facebook and Privacy' page, which will regularly upgrade changes to privacy options. In this tutorial we will introduce general knowledge about DNSSEC and the reasons why securing DNS infrastructure is important to your organization.
In this tutorial we will introduce general knowledge about DNSSEC and the reasons why securing DNS infrastructure is important to your organization. Protecting a networked computer is a challenge that never has an end - even in Linux.
Protecting a networked computer is a challenge that never has an end - even in Linux. If you don't set up wireless network protection from hackers, you may have to stop using the network. This also affects some other wireless networks.
If you don't set up wireless network protection from hackers, you may have to stop using the network. This also affects some other wireless networks. Normally, under the hands of well-trained users, a properly configured Mac computer will not have many security risks.
Normally, under the hands of well-trained users, a properly configured Mac computer will not have many security risks. In this article we will show you how to use BitLocker-to-go to avoid exposing important data by encrypting an external storage drive.
In this article we will show you how to use BitLocker-to-go to avoid exposing important data by encrypting an external storage drive. On April 20, Google received a letter from 10 countries around the world asking the firm to search for this giant to enhance security services for users.
On April 20, Google received a letter from 10 countries around the world asking the firm to search for this giant to enhance security services for users.