Although devices such as iPhone and Android dominate the market, however, the BlackBerry phone

Yesterday, Microsoft officially fixed 5 errors on Windows Office, mainly hackers errors discovered in previous months.

Setting up centralized servers allows you to take advantage of groups, policies and other traditional methods to protect file access on the network.

Do you want your website to be automatically encrypted and increase security? List the pages with the ability to create coding rules with HTTPS Everywhere Extension

On July 15, the 'Check Point Security Tour 2010' security conference was organized by Check Point Software Technologies, a security firm, in Hanoi.

An unpatched vulnerability in Windows has been confirmed by Microsoft that could be exploited by hackers to take control of the new 'favored' trojan system.

In this article we will show you the importance of encryption and go deep into Intel AES-NI research.

rssh, can be used to solve the situation of providing services that require shell access but does not actually allow users to gain access.

In this article we will learn what this new version of Microsoft Security Essentials 2.0 Beta has.

How do you avoid Scam? And what do you do when you're unfortunately the victim of these applications?

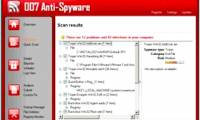
007 Anti-Spwyare (or otherwise called 007 Anti-Spyware AKA 007 Antispyware) is a fake security program that only displays the results of a system review.

Millions of computers have lost control of malicious hackers known as Cracker.

SQL Injection is a hacker 's attack tool to steal vital, vital information of vulnerable organizations and companies.

Viruses have caused a lot of damage or taken away businesses and government agencies billions of dollars in time as well as expensive in recovering from every virus attack.

Today, TipsMake.com will introduce to you the free tool provided by Kaspersky itself, that is Kaspersky Rescue Disk 10

In this article, we will give you 5 websites that can check and evaluate weaknesses and determine how your personal information is downloaded.

Although you can't immediately take advantage of all the new features of Windows 7, you can still plan to use and know more about them right now.

Samba has fixed security holes including two denial of service errors - DoS, so that hackers can easily attack directly on Smbd service.

This is the final part of the article series using BitLocker, in this article, which will take you through the process of restoring BitLocker keys from Active Directory.

Google is occupying a huge search market share on the Internet. According to Symantec, this is urging attackers to target Google's search results
 Although devices such as iPhone and Android dominate the market, however, the BlackBerry phone
Although devices such as iPhone and Android dominate the market, however, the BlackBerry phone Yesterday, Microsoft officially fixed 5 errors on Windows Office, mainly hackers errors discovered in previous months.
Yesterday, Microsoft officially fixed 5 errors on Windows Office, mainly hackers errors discovered in previous months. Setting up centralized servers allows you to take advantage of groups, policies and other traditional methods to protect file access on the network.
Setting up centralized servers allows you to take advantage of groups, policies and other traditional methods to protect file access on the network. Do you want your website to be automatically encrypted and increase security? List the pages with the ability to create coding rules with HTTPS Everywhere Extension
Do you want your website to be automatically encrypted and increase security? List the pages with the ability to create coding rules with HTTPS Everywhere Extension On July 15, the 'Check Point Security Tour 2010' security conference was organized by Check Point Software Technologies, a security firm, in Hanoi.
On July 15, the 'Check Point Security Tour 2010' security conference was organized by Check Point Software Technologies, a security firm, in Hanoi. An unpatched vulnerability in Windows has been confirmed by Microsoft that could be exploited by hackers to take control of the new 'favored' trojan system.
An unpatched vulnerability in Windows has been confirmed by Microsoft that could be exploited by hackers to take control of the new 'favored' trojan system. In this article we will show you the importance of encryption and go deep into Intel AES-NI research.
In this article we will show you the importance of encryption and go deep into Intel AES-NI research. rssh, can be used to solve the situation of providing services that require shell access but does not actually allow users to gain access.
rssh, can be used to solve the situation of providing services that require shell access but does not actually allow users to gain access. In this article we will learn what this new version of Microsoft Security Essentials 2.0 Beta has.
In this article we will learn what this new version of Microsoft Security Essentials 2.0 Beta has. How do you avoid Scam? And what do you do when you're unfortunately the victim of these applications?
How do you avoid Scam? And what do you do when you're unfortunately the victim of these applications? 007 Anti-Spwyare (or otherwise called 007 Anti-Spyware AKA 007 Antispyware) is a fake security program that only displays the results of a system review.
007 Anti-Spwyare (or otherwise called 007 Anti-Spyware AKA 007 Antispyware) is a fake security program that only displays the results of a system review. Millions of computers have lost control of malicious hackers known as Cracker.
Millions of computers have lost control of malicious hackers known as Cracker. SQL Injection is a hacker 's attack tool to steal vital, vital information of vulnerable organizations and companies.
SQL Injection is a hacker 's attack tool to steal vital, vital information of vulnerable organizations and companies. Viruses have caused a lot of damage or taken away businesses and government agencies billions of dollars in time as well as expensive in recovering from every virus attack.
Viruses have caused a lot of damage or taken away businesses and government agencies billions of dollars in time as well as expensive in recovering from every virus attack. Today, TipsMake.com will introduce to you the free tool provided by Kaspersky itself, that is Kaspersky Rescue Disk 10
Today, TipsMake.com will introduce to you the free tool provided by Kaspersky itself, that is Kaspersky Rescue Disk 10 In this article, we will give you 5 websites that can check and evaluate weaknesses and determine how your personal information is downloaded.
In this article, we will give you 5 websites that can check and evaluate weaknesses and determine how your personal information is downloaded. Although you can't immediately take advantage of all the new features of Windows 7, you can still plan to use and know more about them right now.
Although you can't immediately take advantage of all the new features of Windows 7, you can still plan to use and know more about them right now. Samba has fixed security holes including two denial of service errors - DoS, so that hackers can easily attack directly on Smbd service.
Samba has fixed security holes including two denial of service errors - DoS, so that hackers can easily attack directly on Smbd service. This is the final part of the article series using BitLocker, in this article, which will take you through the process of restoring BitLocker keys from Active Directory.
This is the final part of the article series using BitLocker, in this article, which will take you through the process of restoring BitLocker keys from Active Directory. Google is occupying a huge search market share on the Internet. According to Symantec, this is urging attackers to target Google's search results
Google is occupying a huge search market share on the Internet. According to Symantec, this is urging attackers to target Google's search results