Zeus botnet continues to spread malicious code to attack many users' systems through errors in Adobe PDF files.

In this article, we will show you two very different modes of accessing a protected Wi-Fi network.

In this article, I will show you what to do to secure the data for your company.

In the second part of this article series, I will show you how to enforce BitLocker security in a more consistent way using group policy settings.

For users of Facebook services, when initialized by default, all other Facebook users are not friends and cannot view your Facebook account information. They will receive a

A new online solution from Google for web developers, including server systems with a lot of current security security holes ...

Today, TipsMake.com will introduce you to the plug-in for popular browsers today, helping you ensure safety when surfing the web.

Security researchers say websites like eBay or Amazon are becoming targets for hackers to 'launder money' ...

Facebook is creating a lot of interesting and interesting ways to share information, links ... besides new features like Instant Personalization.

In the third part of this series, we will show you how to save BitLocker Recovery keys in the Active Directory database.

Facebook is probably the largest social network in the world, but Facebook is also suffering from security problems that customers have to pay attention to.

As announced last week, Microsoft has released two updates for two security holes that are classified as serious

What if you think your data is not important for someone to look at?

Adobe has released an update of 11.5.7.609 of the Shockwave Player application, including 18 patches, 17 of which are classified as serious by Adobe.

We often enter personal information on many different websites - and the Internet never forgets them. Here are some ways to delete your traces on the web.

Do not allow eavesdroppers to capture passwords, emails and other sensitive data. In this article, I will show you some useful applications that can encrypt wireless traffic.

Sometimes computer users forget the basics of security and create a hole in the process.

Today, networks increasingly contain many different types of computers (including many types of hardware, software and operating systems) that are no longer new.

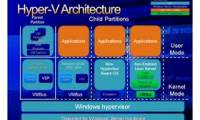
This article will show you how to configure Hyper-V security using Authorization Manager.

Null sessions, called IPC $ on a Windows platform server, are an anonymous connection to a shared network that allows users in the network to access freely.
 Zeus botnet continues to spread malicious code to attack many users' systems through errors in Adobe PDF files.
Zeus botnet continues to spread malicious code to attack many users' systems through errors in Adobe PDF files. In this article, we will show you two very different modes of accessing a protected Wi-Fi network.
In this article, we will show you two very different modes of accessing a protected Wi-Fi network. In this article, I will show you what to do to secure the data for your company.
In this article, I will show you what to do to secure the data for your company. In the second part of this article series, I will show you how to enforce BitLocker security in a more consistent way using group policy settings.
In the second part of this article series, I will show you how to enforce BitLocker security in a more consistent way using group policy settings. For users of Facebook services, when initialized by default, all other Facebook users are not friends and cannot view your Facebook account information. They will receive a
For users of Facebook services, when initialized by default, all other Facebook users are not friends and cannot view your Facebook account information. They will receive a A new online solution from Google for web developers, including server systems with a lot of current security security holes ...
A new online solution from Google for web developers, including server systems with a lot of current security security holes ... Today, TipsMake.com will introduce you to the plug-in for popular browsers today, helping you ensure safety when surfing the web.
Today, TipsMake.com will introduce you to the plug-in for popular browsers today, helping you ensure safety when surfing the web. Security researchers say websites like eBay or Amazon are becoming targets for hackers to 'launder money' ...
Security researchers say websites like eBay or Amazon are becoming targets for hackers to 'launder money' ... Facebook is creating a lot of interesting and interesting ways to share information, links ... besides new features like Instant Personalization.
Facebook is creating a lot of interesting and interesting ways to share information, links ... besides new features like Instant Personalization. In the third part of this series, we will show you how to save BitLocker Recovery keys in the Active Directory database.
In the third part of this series, we will show you how to save BitLocker Recovery keys in the Active Directory database. Facebook is probably the largest social network in the world, but Facebook is also suffering from security problems that customers have to pay attention to.
Facebook is probably the largest social network in the world, but Facebook is also suffering from security problems that customers have to pay attention to. As announced last week, Microsoft has released two updates for two security holes that are classified as serious
As announced last week, Microsoft has released two updates for two security holes that are classified as serious What if you think your data is not important for someone to look at?
What if you think your data is not important for someone to look at? Adobe has released an update of 11.5.7.609 of the Shockwave Player application, including 18 patches, 17 of which are classified as serious by Adobe.
Adobe has released an update of 11.5.7.609 of the Shockwave Player application, including 18 patches, 17 of which are classified as serious by Adobe. We often enter personal information on many different websites - and the Internet never forgets them. Here are some ways to delete your traces on the web.
We often enter personal information on many different websites - and the Internet never forgets them. Here are some ways to delete your traces on the web. Do not allow eavesdroppers to capture passwords, emails and other sensitive data. In this article, I will show you some useful applications that can encrypt wireless traffic.
Do not allow eavesdroppers to capture passwords, emails and other sensitive data. In this article, I will show you some useful applications that can encrypt wireless traffic. Sometimes computer users forget the basics of security and create a hole in the process.
Sometimes computer users forget the basics of security and create a hole in the process. Today, networks increasingly contain many different types of computers (including many types of hardware, software and operating systems) that are no longer new.
Today, networks increasingly contain many different types of computers (including many types of hardware, software and operating systems) that are no longer new. This article will show you how to configure Hyper-V security using Authorization Manager.
This article will show you how to configure Hyper-V security using Authorization Manager. Null sessions, called IPC $ on a Windows platform server, are an anonymous connection to a shared network that allows users in the network to access freely.
Null sessions, called IPC $ on a Windows platform server, are an anonymous connection to a shared network that allows users in the network to access freely.