Activate the mechanism to automatically encrypt websites into Firefox
TipsMake.com - Do you want your website to be automatically encrypted and increase security? List the pages with the ability to create rules that encode Firefox's HTTPS Everywhere Extension .
Path HTTPS Extension Everywhere
How to write Rule HTTPS Everywhere
Before installing the extension
In this test, we use Twitter and the search page Duck Duck Go :
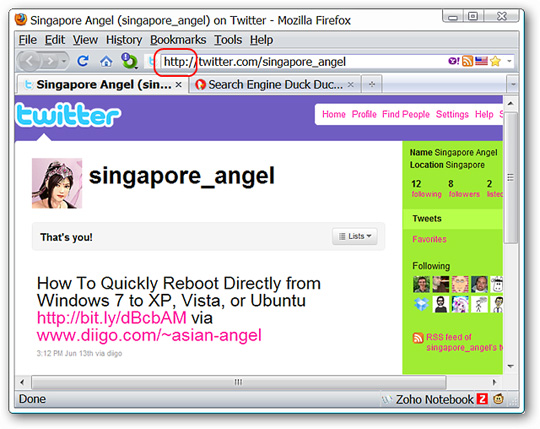

After installing the extension
Install Extension from EFF Deeplinks Blog from the link above:

Just to check how fast the extension will work (refresh the web page frequently), we will open both sites simultaneously while installing the extension. After restarting the browser, you will see that both are encrypted as follows:


Your own customizations and rules
Check the entire custom mode after installation, will display a list of all supported websites in the default mode. Choose Disable which websites you don't need:
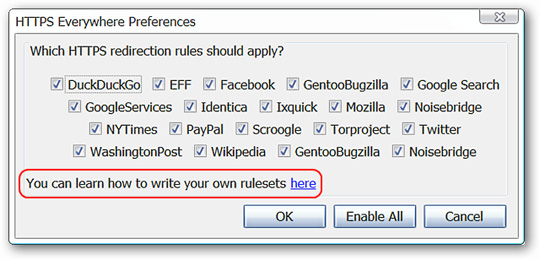
Click on the link above to go to the website, where you can set up rules and get a strict explanation of these rules. After creating a rule of thumb, save it as an xml file at HTTPSEverywhereUserRules folder inside Firefox Profile. EFF also has an email address attached, you can post these rules and share them with everyone:

Good luck!