Use BitLocker to encrypt removable drives - Part 4
Network Administration - This is the final part of the article series using BitLocker, in this article, which will take you through the process of restoring BitLocker keys from Active Directory.
>> Using BitLocker to encrypt external storage drives - Part 1
>> Using BitLocker to encrypt external storage drives - Part 2
>> Using BitLocker to encrypt external storage drives - Part 3
In the previous article of this series, we explained that Windows Server 2008 R2 is capable of saving BitLocker keys for external storage devices in the Active Directory database. Since I showed you how to enable the group policy settings needed to allow BitLocker keys to be stored in Active Directory, in this section we will conclude the series by introducing you to the process. How does lock recovery work?
To help illustrate, allow us to assume that one of the most important characters in your organization has copied some important files to BitLocker encrypted USB drive and now he has forgotten his password. password What you need to do?
The first step in the recovery process is to insert a BitLocker encrypted USB drive into a computer running Windows 7. When you do, the dialog box shown in Figure A will appear, you will be asked to enter the password that was used. used to unlock the USB drive. Since the password has been forgotten, we must perform the recovery process.

Figure A: Windows prompts you to enter a password to increase encryption drive access
If you look at the picture above, you will see there is a link I Forgot My Password . Clicking on this link will take you to the screen as shown in Figure B.
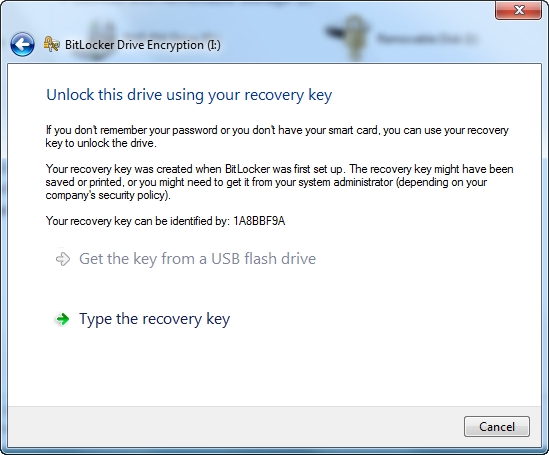
Figure B: Windows provides a number of recovery options that can be used in case of a forgotten password
As you can see in the image above, what really stands out is the option to enter the recovery key. However, we will use this option later because we are not ready to use it yet. If you look closely at the image above, you will see a text saying: Key Can Be Identified By Your Recovery: 1A8BBF9A . (Your recovery key may be: 1A8BBF9A). The hexadecimal number that appears at the end of the text is unique to the USB and can be used to identify the USB during recovery. So you need to record this number to use it later.
Determining the unique identity of USB is only the first step in the recovery process. Now we really have to retrieve the recovery key from Active Directory. There is an obstacle to our implementation. Although the recovery key for USB is stored in Active Directory, we need a way to recover them. However, no administrative interface installed on our server provides this capability.
Install the BitLocker Recovery Password Viewer
Before you can restore BitLocker recovery keys from Active Directory, you need to install the utility called the BitLocker Recovery Password Viewer. Although there is no complication in installing this utility, the option to enable it is hidden inside Server Manager.
To install the BitLocker Recovery Password Viewer, open Server Manager , select the Features section. Next, click the Add Features link, and you will see Windows open the Add Features Wizard. The Add Features Wizard contains a series of checkboxes that correspond to the various features you can install. There is a BitLocker checkbox on the list but this is not the option we need. Instead, scroll down and look in the list of Remote Server Administration Tools options . Expand this option, then find the small option called Feature Administration Tools . Expand the Feature Administration Tools and select the BitLocker Drive Encryption Administration Utilities checkbox. Verify that the checkboxes below this option are also selected, as shown in Figure C, and then click Next .
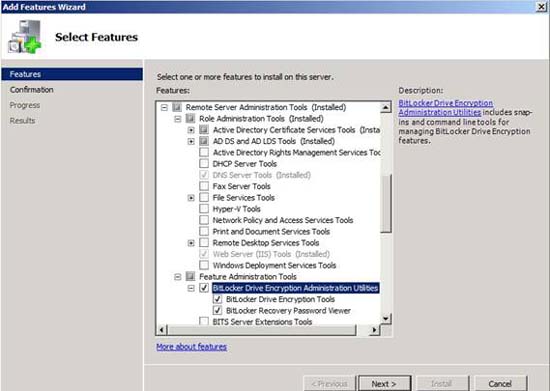
Figure C: You must enable BitLocker Drive Encryption Administration Utilities
Now, click Next , you will see a screen that provides summary information about the installed features, along with a warning message that requires a reboot after the installation process is complete. Click Install and the necessary binary binaries will be installed.
When the installation process is complete, Windows will display the Installation Results screen, shown in Figure D. As you can see, Windows tells you which components are installed, but it is not required to restart.
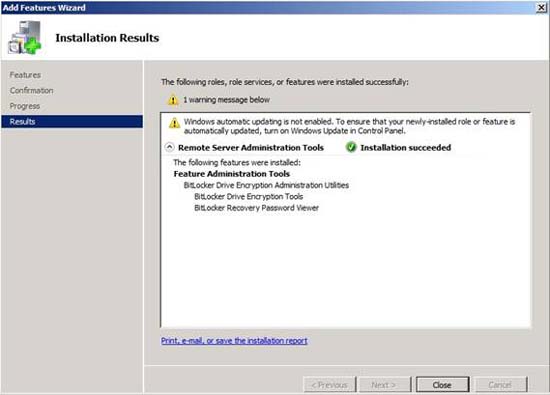
Figure D: Although Windows Server does not require a restart, you should still restart the server
See page 2
Key recovery process
We have finished installing different administrative tools, and now you can completely switch to the key recovery process. It should be noted that Windows does not provide you with a standard interface for this recovery, but instead will be performed through the Active Directory Users and Computers window.
To restore the BitLocker key, open the Active Directory Users and Computers window, then right-click the domain name list. A menu will appear with the Find BitLocker Recovery Password option , as shown in Figure E.
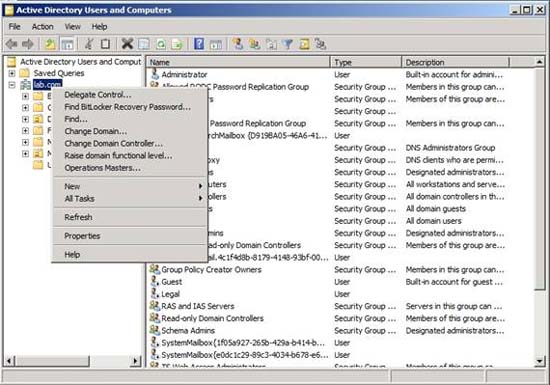
Figure F: Key recovery is done through the Active Directory Users and Computers window
When using the BitLocker Recovery Password option, you will be taken to the Find BitLocker Recovery Password dialog box, as shown in Figure F. It is important to remember 8 hexadecimal numbers that distinguish USB uniqueness. This is where you enter those numbers. After performing this action, click the Search button, then the server will query the drive's recovery password. If you look at the lower part of the dialog box, you'll see that the recovery key is not the password the user used to encrypt the USB but a 48-digit string.
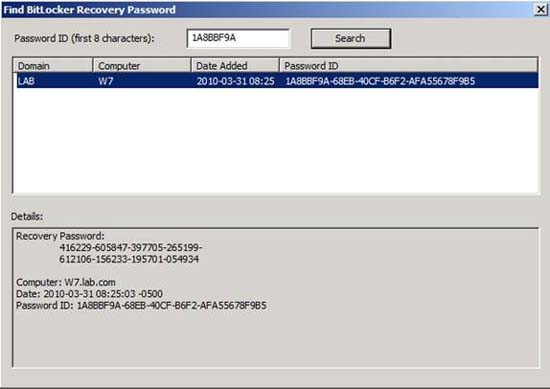
Figure F: The recovery key is displayed in the lower part of the dialog box
Now that you have the recovery key for the USB, go back to the computer where you plugged in the USB and enter the recovery key into the allocated space, as shown in Figure G.

Figure G: Enter the BitLocker recovery key in the allocated area
After entering the recovery key, you will see a screen similar to the screen shown in Figure H, indicating that you have been granted temporary access to the USB. In other words, the drive will still be encrypted and the forgotten password will still work. If you remove and reinstall the USB now, you will have to repeat the entire recovery process unless the user remembers the password.

Figure H: Entering the recovery key provides temporary access to the encrypted volume
To avoid having to enter a 48-digit recovery key every time you use USB, click the Manage BitLocker link. You are then taken to the dialog box shown in Figure I, which allows you to change the password that was used to increase disk access.

Figure I: After increasing access to the encrypted volume, you need to reset the drive's password
Conclude
In this series, I have shown you a simple way to protect data stored on external storage drives with BitLocker to Go. However, if you plan to use BitLocker to Go, you should implement Active Directory-based key recovery to avoid losing data due to a forgotten password.