Web12: Session Fixation hacking technique
1. Introduction
Session Fixation is a technique that allows hackers to hijack a user's session. This technique takes advantage of the fact that the server does not change the session ID value every time the user logs in, instead it uses a pre-existing session ID. The attack process includes obtaining a valid session ID (possibly by accessing the website), then finding a way for the victim to log in to the website with this session ID, and finally, when the victim successfully logs in. , the hacker will browse the website with his account. The specific scenario is as follows:
Mallory finds a website, such as http://unsafe.example.com, that accepts any session ID from the request without authentication.
Mallory will send Alice an e-mail, which contains the link http://unsafe.example.com/?SID=1234.
Alice goes to http://unsafe.example.com/?SID=1234. Then log in to the website.
Mallory simply goes to http://unsafe.example.com/?SID=1234, and uses the website with Alice's account.
Mallory can use the following methods to set cookies for Alice:
Enclose a script to set cookies
Send HTTP Response packet with Mallory cookie valueSend HTTP Response packet with Mallory cookie value
Use HTML meta tags:

2. Examples
Example 1 – Client-side scripting
Similar to the scenario mentioned above, however, in this case, the Session ID is not passed in the URL but in the cookie. To edit the value of the Session ID in the victim's cookie, the hacker will insert a piece of Javascript:
http://website.kom/document.cookie='sessionid=abcd';
Example 2 - tag
Similar to client-side scripting, but this time the hacker will insert additional tags:
http://website.kon/
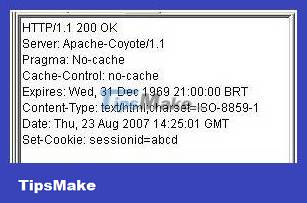
Example 3 – HTTP header response
Session ID insertion can also be done by intercepting packets exchanged between the client and the Web application, then inserting the Set-Cookie field into the header.
3. How to prevent
The cause of this error is because the server does not regenerate the session ID after each successful login. Therefore, fixing this error is not difficult, we just need to change the value of Session ID and that's it. In PHP, we use the session_regenerate_id() function to regenerate the session.