Web10: Some forms of fake http headers
In web programming, many programmers use fields in http headers to check and control user access. This inspection and control may seem safe, but in reality all fields in the http headers can be tampered with, leading to the risk of unauthorized access to those websites.
Below, TipsMake.com will help you learn about some cases of forging http headers to achieve unauthorized access.
In some cases, some websites only allow access from certain pages. When you request from another page, access will be denied.
For example, try visiting the following page:
URL: http://natas4.natas.labs.overthewire.org/
Username: natas4
Password: Z9tkRkWmpt9Qr7XrR5jWRkgOU901swEZ
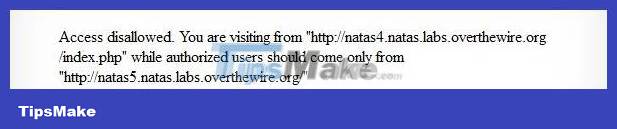
In this case, the programmer used the variable $_SERVER['HTTP_REFERER'] to control access. The field corresponding to this variable in the header is Referer.
Therefore, you can change the header to access that site. Use Tamper data (firefox addon) to change the referer field in the header to the following:

And we can access that site

Another case:
A site stores the logged in state in a cookie, because cookies are also sent in the http header so we can change:
URL: http://natas5.natas.labs.overthewire.org/
Username: natas5
Password: iX6IOfmpN7AYOQGPwtn3fXpbaJVJcHfq

When using Tamper data to analyze the header sent, we see the parameter loggedin=0 in the cookie field. Change it to 1 then submit to see the difference.

An example follows:
A site has a segment that handles the ip of incoming visitors. This site only allows access from a fixed ip address, and access from other ip addresses is not allowed. However, it uses the information sent in the http headers to check the user's IP.
X-Forwarded-For and Client-Ip are two corresponding fields of two server variables $_SERVER['HTTP_X_FORWARDED_FOR'] and $_SERVER['HTTP_CLIENT_IP'] in the HTTP header. Therefore, we can spoof the access IP address by changing one of these two fields.
For upload form
Some programmers use code to check the extension of the uploaded file as follows:
if($_FILES['file']['type'] == 'image/gif') { //cho phép upload } else { //không cho phép upload }Hackers can easily bypass it by using Tamper software to edit the Content-Type field in the header before sending it to the server.
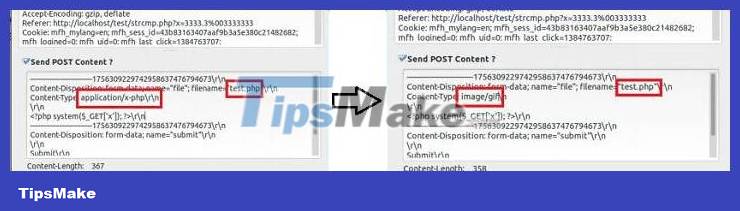
And hackers can upload a file with an unauthorized .php extension.
Using fields in http headers to check and control access is not safe, so programmers need to understand it to ensure website security.
Below is a video describing some cases of fake http headers performed by WhiteHat.vn forum members:
Good luck!