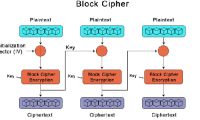
Block Cipher is a data encryption method in which data is divided into fixed-sized blocks, usually 64 or 128 bits.

Session hijacking is the act of intentionally taking control of a user's web session.

Acunetix is an effective website vulnerability scanner, designed to detect and fix security vulnerabilities in web applications.
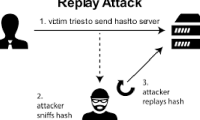
Replay Attack is also known as replay attack. This is a network attack method in which the attacker records and reuses valid communications between two parties to perform

UPnP (Universal Plug and Play) is a set of networking protocols that allow different devices on the same local network to discover and interact with each other without requiring

mTLS stands for Mutual Transport Layer Security, which is a network security method that allows mutual authentication between a client and a server during data transmission.

Database security refers to the measures taken to protect a business's data from unauthorized access, disclosure, alteration, or theft.

Có nhiều cách khôi phục mật khẩu máy tính Windows nhanh chóng mà không lo mất dữ liệu. Hướng dẫn này sẽ giúp bạn mở khóa laptop, PC dễ dàng bằng CMD, USB boot hoặc phần mềm chuyên

Shortcut Virus is one of the common viruses that causes files to be hidden, spreads quickly and slows down computers and USBs. If you are experiencing this situation, do not miss

USB is a compact data storage device, but can be damaged or corrupted if not used properly, especially when removing the USB from the computer.

DHCP Snooping is a layer 2 security feature, similar to a firewall, built into the operating system of a network switch or router to enhance network security.

A logic bomb is a piece of malicious code embedded in an application or software program.

OCSP (Online Certificate Status Protocol) is an Internet protocol (IP) used to determine the revocation status of X.509 digital certificates.

The W32.UsbFakeDrive virus is a dangerous malware that can spread via USB and hide data. When users click on the fake shortcut, the virus will spread to the computer. To completely

Malwarebytes Anti-Malware is one of the leading antivirus and computer protection software available today. With the ability to detect and remove malware, Trojans, ransomware,

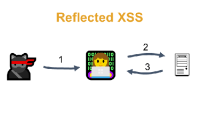
Reflected XSS is a type of cross-site scripting attack. Hackers insert malicious JavaScript code into a web page and then trick visitors into clicking on a link containing the

Smurf Attack is a type of DDOS attack, hackers will attack the victim's server by sending fake IP requests using Internet Control Message Protocol to create fake accesses that

Ransomware is becoming one of the biggest threats to internet users. This type of malware can encrypt data and force victims to pay a ransom to recover it. Understanding how it

Hyperjacking is a sophisticated type of cyber attack where a bad actor takes control of the hypervisor, the component that manages the virtual environment in a computer system.

Ping of death is a form of denial of service (DoS) attack in which an attacker sends large or abnormally fragmented ICMP (Internet Control Message Protocol) packets to a target
 Block Cipher is a data encryption method in which data is divided into fixed-sized blocks, usually 64 or 128 bits.
Block Cipher is a data encryption method in which data is divided into fixed-sized blocks, usually 64 or 128 bits. Session hijacking is the act of intentionally taking control of a user's web session.
Session hijacking is the act of intentionally taking control of a user's web session. Acunetix is an effective website vulnerability scanner, designed to detect and fix security vulnerabilities in web applications.
Acunetix is an effective website vulnerability scanner, designed to detect and fix security vulnerabilities in web applications. Replay Attack is also known as replay attack. This is a network attack method in which the attacker records and reuses valid communications between two parties to perform
Replay Attack is also known as replay attack. This is a network attack method in which the attacker records and reuses valid communications between two parties to perform UPnP (Universal Plug and Play) is a set of networking protocols that allow different devices on the same local network to discover and interact with each other without requiring
UPnP (Universal Plug and Play) is a set of networking protocols that allow different devices on the same local network to discover and interact with each other without requiring mTLS stands for Mutual Transport Layer Security, which is a network security method that allows mutual authentication between a client and a server during data transmission.
mTLS stands for Mutual Transport Layer Security, which is a network security method that allows mutual authentication between a client and a server during data transmission. Database security refers to the measures taken to protect a business's data from unauthorized access, disclosure, alteration, or theft.
Database security refers to the measures taken to protect a business's data from unauthorized access, disclosure, alteration, or theft. Có nhiều cách khôi phục mật khẩu máy tính Windows nhanh chóng mà không lo mất dữ liệu. Hướng dẫn này sẽ giúp bạn mở khóa laptop, PC dễ dàng bằng CMD, USB boot hoặc phần mềm chuyên
Có nhiều cách khôi phục mật khẩu máy tính Windows nhanh chóng mà không lo mất dữ liệu. Hướng dẫn này sẽ giúp bạn mở khóa laptop, PC dễ dàng bằng CMD, USB boot hoặc phần mềm chuyên Shortcut Virus is one of the common viruses that causes files to be hidden, spreads quickly and slows down computers and USBs. If you are experiencing this situation, do not miss
Shortcut Virus is one of the common viruses that causes files to be hidden, spreads quickly and slows down computers and USBs. If you are experiencing this situation, do not miss USB is a compact data storage device, but can be damaged or corrupted if not used properly, especially when removing the USB from the computer.
USB is a compact data storage device, but can be damaged or corrupted if not used properly, especially when removing the USB from the computer. DHCP Snooping is a layer 2 security feature, similar to a firewall, built into the operating system of a network switch or router to enhance network security.
DHCP Snooping is a layer 2 security feature, similar to a firewall, built into the operating system of a network switch or router to enhance network security. A logic bomb is a piece of malicious code embedded in an application or software program.
A logic bomb is a piece of malicious code embedded in an application or software program. OCSP (Online Certificate Status Protocol) is an Internet protocol (IP) used to determine the revocation status of X.509 digital certificates.
OCSP (Online Certificate Status Protocol) is an Internet protocol (IP) used to determine the revocation status of X.509 digital certificates. The W32.UsbFakeDrive virus is a dangerous malware that can spread via USB and hide data. When users click on the fake shortcut, the virus will spread to the computer. To completely
The W32.UsbFakeDrive virus is a dangerous malware that can spread via USB and hide data. When users click on the fake shortcut, the virus will spread to the computer. To completely Malwarebytes Anti-Malware is one of the leading antivirus and computer protection software available today. With the ability to detect and remove malware, Trojans, ransomware,
Malwarebytes Anti-Malware is one of the leading antivirus and computer protection software available today. With the ability to detect and remove malware, Trojans, ransomware, Reflected XSS is a type of cross-site scripting attack. Hackers insert malicious JavaScript code into a web page and then trick visitors into clicking on a link containing the
Reflected XSS is a type of cross-site scripting attack. Hackers insert malicious JavaScript code into a web page and then trick visitors into clicking on a link containing the Smurf Attack is a type of DDOS attack, hackers will attack the victim's server by sending fake IP requests using Internet Control Message Protocol to create fake accesses that
Smurf Attack is a type of DDOS attack, hackers will attack the victim's server by sending fake IP requests using Internet Control Message Protocol to create fake accesses that Ransomware is becoming one of the biggest threats to internet users. This type of malware can encrypt data and force victims to pay a ransom to recover it. Understanding how it
Ransomware is becoming one of the biggest threats to internet users. This type of malware can encrypt data and force victims to pay a ransom to recover it. Understanding how it Hyperjacking is a sophisticated type of cyber attack where a bad actor takes control of the hypervisor, the component that manages the virtual environment in a computer system.
Hyperjacking is a sophisticated type of cyber attack where a bad actor takes control of the hypervisor, the component that manages the virtual environment in a computer system. Ping of death is a form of denial of service (DoS) attack in which an attacker sends large or abnormally fragmented ICMP (Internet Control Message Protocol) packets to a target
Ping of death is a form of denial of service (DoS) attack in which an attacker sends large or abnormally fragmented ICMP (Internet Control Message Protocol) packets to a target