What is DHCP Snooping? How to configure DHCP Snooping effectively
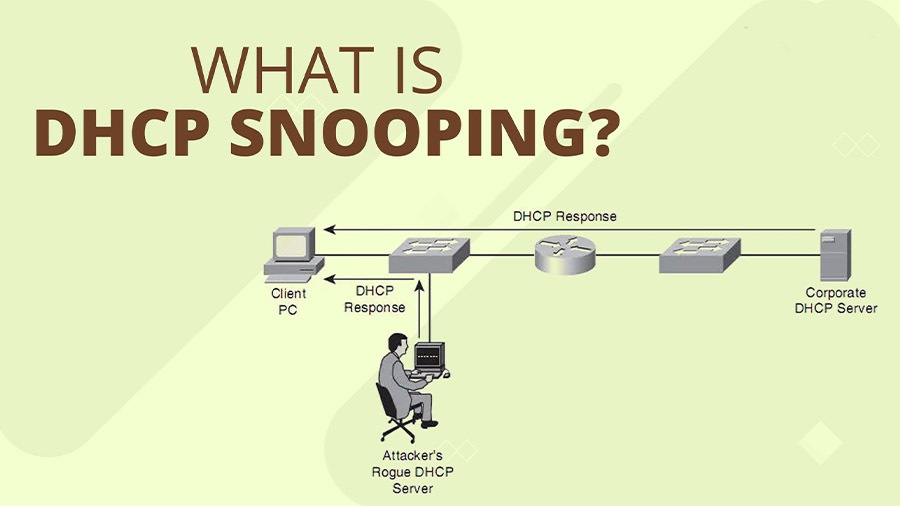
DHCP Snooping is a security technique in computer networks to prevent attacks related to the DHCP protocol. Let's learn in detail about how it works and its role in protecting your network from potential threats.
What is DHCP Snooping?
DHCP Snooping is a layer 2 security feature, similar to a firewall, built into the operating system of a network switch or router to enhance network security. It works by monitoring DHCP (Dynamic Host Configuration Protocol) traffic and classifying switch ports into trusted and untrusted ports.
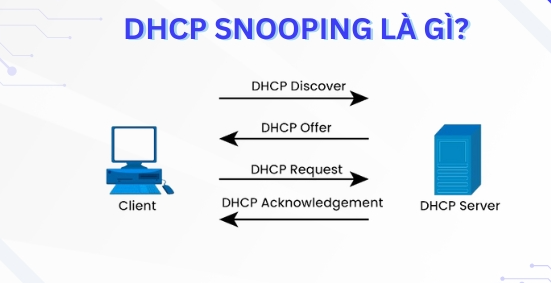
What is DHCP Snooping?
This feature logs information about DHCP packets sent and received on the network, ensuring that only trusted DHCP servers can provide IP addresses to clients.
The Role of DHCP Snooping
DHCP Snooping plays a vital role in protecting your network from attacks. The roles of DHCP Snooping include:
- Protection against rogue DHCP servers: Identifying and blocking unauthorized DHCP servers helps protect clients from receiving erroneous settings that can cause disruption in the network.
- Monitor and log network information: DHCP Snooping also plays a role in logging information about DHCP requests and responses. Administrators can view the history of IP addresses assigned, thereby easily identifying potential problems in the network.
- Enhance overall network security: Unauthorized devices will be blocked from connecting, only valid devices can access network resources.
How does DHCP Snooping work?
DHCP Snooping acts as a monitor of DHCP traffic on the network, especially broadcast packets. When a device (client) requests an IP address, DHCP Snooping collects important data such as:
- Device MAC address
- The IP address it requires
- IP address lease time
It then compares this information with the data provided by a trusted DHCP server. If any discrepancy is detected, the IP assignment request is blocked and an alert is sent to the network administrator.
Attacks Prevented by DHCP Snooping
DHCP Snooping not only protects your network from rogue DHCP servers, but it can also prevent a number of other common attacks.
DHCP Spoofing Attack
A DHCP spoofing attack occurs when an attacker sets up a fake DHCP server on a network. The goal of this attack is to cause clients to connect to the fake server instead of the legitimate server. The attacker can then control IP addresses, change network configurations, and collect sensitive information from users.
DHCP Snooping prevents these attacks by not allowing unauthorized DHCP servers to send responses to DHCP requests. Only authenticated servers can interact with clients on the network, thus minimizing the possibility of attack.
DHCP Starvation Attack
DHCP crash attacks typically occur when an attacker attempts to exhaust all available IP addresses from a DHCP server. By sending many fake DHCP requests, an attacker can leave the DHCP server with no IP addresses to allocate to valid clients, resulting in a service disruption.
DHCP Snooping is capable of monitoring and logging DHCP requests, helping to detect unusual behavior.
How to configure DHCP Snooping?
Here are the general steps to configure DHCP Snooping on Cisco switches and routers:
- Enable DHCP Snooping Globally: Enable DHCP Snooping on the Cisco switch.
SW1(config)#ip dhcp snooping
- Enable DHCP Snooping for each VLAN: Enable DHCP Snooping for specific VLANs.
SW1(config)#ip dhcp snooping vlan 10
- Configure Trusted Ports: Define which ports are trusted
SW1(config)#interface FastEthernet0/1
SW1(config-if)#ip dhcp snooping trust
- DHCP Request Rate Limit Option:
SW1(config)# interface FastEthernet0/1
SW1(config-if)# ip dhcp snooping limit rate 20
- Verify DHCP Snooping: Check the status and bindings of DHCP Snooping.
SW1(config)# show ip dhcp snooping
SW1(config)# show ip dhcp snooping binding
Conclude
DHCP Snooping is an essential security feature that helps protect your network from attacks. By preventing rogue DHCP servers, it not only enhances security but also provides a stable network environment for connected devices.
As such, it can be seen that configuring and maintaining DHCP Snooping is also an important part of an overall network security strategy, helping administrators quickly identify and respond to potential threats.
You should read it
- ★ Steps to fix 'Unable to Contact your DHCP Server' error on Windows 10
- ★ What is DHCP or dynamic host configuration protocol?
- ★ How to Install, Configure, and Test Windows Server 2012 R2 Single Subnet DHCP Server
- ★ Set up DHCP server in Windows 2003
- ★ The DHCP vulnerability in Red Hat Linux helps hackers execute remote code