What is UPnP? How to Protect Your Devices from UPnP
Universal Plug and Play (UPnP) is a networking protocol that allows devices on a LAN to automatically discover and connect to each other without manual configuration. This article from TipsMake will help you explore UPnP, as well as its benefits and risks.
What is UPnP?
UPnP (Universal Plug and Play) is a set of networking protocols that allows different devices on the same local network to discover and interact with each other without user intervention. With UPnP, users can easily connect and share information between different devices such as computers, printers, routers, security cameras, and many other devices.
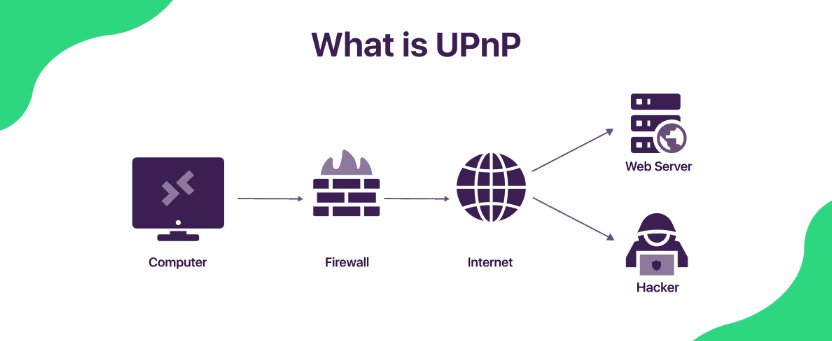
What is UPnP?
The protocol uses a client-server model, in which "client" devices can request services from "server" devices. Devices using UPnP typically rely on data transfer over HTTP and XML to make requests.
What is UPnP used for?
UPnP serves many different purposes in a network environment. Below are some common applications of UPnP that users may encounter in their daily lives.
Sharing and transmitting data
One of the main uses of UPnP is sharing and transferring data between devices. For example, if you have a computer with a lot of music or video files, you can use UPnP to share these files with other devices on the same network, such as a smart TV or Bluetooth speaker.
Support online gaming
UPnP simplifies the process of connecting game consoles to game servers, allowing players to easily join online matches without complicated configuration. Simply enable UPnP on your router and your device will automatically handle the necessary port opening to connect to the game. This not only saves time but also enhances the user's gaming experience.
Integrating IoT in Home Devices
With the explosion of IoT devices, UPnP has become the bridge between smart devices. You can control lights, door locks or air conditioners remotely via your smartphone with just a few taps.
Does UPnP help with gaming?
For gamers, UPnP can bring significant benefits. Using UPnP eliminates cumbersome configuration steps, allowing players to enjoy a smoother and more enjoyable gaming experience.

Does UPnP help with gaming?
- Increased connection speed: UPnP automatically opens ports on the router, reducing latency and increasing connection speeds to game servers. This means players can connect more quickly and stably, improving their chances of winning competitive matches.
- Reduced Lag: One of the biggest problems gamers face is lag. Lag can disrupt the gaming experience, making players feel frustrated and lose interest. Thanks to UPnP's automatic port opening and configuration, lag can be significantly reduced.
- Connect with Friends Easily: UPnP simplifies the process of connecting with friends by allowing devices to automatically discover each other on the network. Players can simply select friends from the list and start chatting or joining a match without having to go through many complicated steps. This not only saves time but also enhances social connection within the gaming community.
Why is UPnP insecure?
Although UPnP brings many benefits, it also has many potential security risks that users need to pay attention to as follows:
Lack of access control
One of the biggest problems with UPnP is the lack of access control. When UPnP is enabled on a router, any device on the network can request to open a port without authentication. This means that if a malicious device enters the network, it can easily exploit UPnP to open a port and gain access to the internal network.
This risk becomes more serious when many IoT devices are connected to the network, as they often have a low level of security. Once one device is compromised, an attacker can easily access other devices on the same network.
DDoS attack
A distributed denial of service (DDoS) attack is a common form of cyber attack in which an attacker attempts to disable a service by sending a large number of requests to a server. UPnP can be exploited to perform DDoS attacks by opening ports to spoofed IP addresses.
Can be hacked into personal devices
Another risk of UPnP is the potential for compromise of personal devices. If a hacker can exploit UPnP to open ports, they can gain access to devices on the network, including personal computers, security cameras, and other IoT devices. This can lead to the theft of personal information, tracking of user activity, or even complete control of devices.
How common are UPnP attacks?
Attacks via UPnP are not an uncommon phenomenon. In recent years, there have been many reports of cyber attacks that exploit UPnP to penetrate internal networks.
Notable attacks
There have been several high-profile attacks that security experts have documented. One of them is the Mirai attack, where a network of IoT devices was hijacked and used to launch large-scale DDoS attacks. This attack clearly shows that UPnP can become a major security vulnerability if not configured properly.
Attack frequency
Although it is impossible to accurately quantify the rate of UPnP attacks, many experts believe that the number of these attacks is increasing. This may be due to the increasing number of IoT devices being used, enriching the diversity of attack channels.
Precautions
Users can take precautions to reduce the risk of attacks via UPnP. One of the most effective measures is to disable UPnP when not needed. Setting up a virtual private network (VPN) can also help protect your device from outside attacks.
What are the consequences of turning off UPnP?
When users decide to disable UPnP, there are several consequences they need to consider:
- Difficulty in connecting: Applications, games or services that require opening ports will not be able to do this automatically, leading to users having to manually configure the network.
- Reduced Flexibility: Disabling UPnP can cause users to lose flexibility in using their smart devices. If you have multiple smart devices in your home, disabling UPnP can make managing and controlling them more complicated.
How to protect devices against UPnP?
To ensure the safety of your devices and networks, users need to take specific measures to protect against UPnP-related risks. Here are some useful ways you can apply.
Disable UPnP on router
The easiest way to protect your devices is to disable UPnP directly on the router. Router manufacturers usually provide this option in the settings. Disabling UPnP will help limit the ability to open ports automatically and reduce the risk of attack.
Update Firmware Regularly
Device manufacturers regularly release firmware updates to fix security vulnerabilities and improve performance. Make sure you regularly check and update the firmware on your router and other devices on your network.
Use a firewall
A firewall is an important layer of defense for any network. It helps filter traffic and block unwanted requests from the outside. By enabling and configuring a firewall on your router, you can protect your network from attacks.
Use VPN
Using a virtual private network (VPN) is one of the most effective ways to protect your personal information and network connection. VPNs encrypt your data, so even if an attacker manages to break into your network, they won't be able to read your information.
Conclude
Universal Plug and Play (UPnP) brings many conveniences to users in connecting and sharing data between devices. However, it also has many potential security risks that users need to pay attention to.
To protect your devices from UPnP attacks, disabling UPnP on your router, regularly updating your firmware, using a firewall and VPN are all good practices you should take.
You should read it
- What is the password hint? The effect of Password hint when you forget a password on Windows
- How to fix Explorer.exe error with warning yellow triangle on Windows 10
- PS2 emulator for Android, runs God of War II smoothly at 60 fps
- Things to know when using a digital camera
- Features of Digital Crown on Apple Watch you may not know
- DeepSeek 'lied' about the cost of developing AI chatbot?
 What is mTLS? Benefits of mTLS in Data Security
What is mTLS? Benefits of mTLS in Data Security What is Database Security and how to secure the database effectively?
What is Database Security and how to secure the database effectively? Cách xóa mật khẩu Windows không mất dữ liệu
Cách xóa mật khẩu Windows không mất dữ liệu How to effectively remove Shortcut Virus on computer and USB
How to effectively remove Shortcut Virus on computer and USB How to safely remove USB from computer
How to safely remove USB from computer What is DHCP Snooping? How to configure DHCP Snooping effectively
What is DHCP Snooping? How to configure DHCP Snooping effectively