What is Session Hijacking? Common Session Hijacking Attacks
One of the top concerns of Internet users or businesses is having their data and sensitive information stolen. Many users have also lost money in their bank accounts. And that could be a sign that the user is being attacked by Session Hijacking. So what is a Session Hijacking attack? Let's find out with TipsMake in the following article.
What is Session Hijacking?
Session hijacking is the act of intentionally taking control of a user's web session. It is an attack in which a bad actor steals or manipulates a session token to gain unauthorized access to information or services. The attacker intercepts this token, which is like a secret handshake between the user and the website, and can impersonate a legitimate user, causing chaos. Interception methods can range from network eavesdropping to sophisticated phishing.

What is Session Hijacking?
How Session Hijacking Works
Session hijacking occurs when an attacker uses a captured, brute-forced, or reverse-engineered session ID to take control of a legitimate user's session while it is in progress. When successful, the attacker has complete access to the user's data and the ability to perform actions on behalf of the user whose session was hijacked.
There are three main techniques for session hijacking:
- Brute Force Attack: Attacker tries multiple session IDs until success is achieved.
- Computation: In many cases, session IDs are generated in a non-random and computationally-independent manner.
- Theft: Attackers use different techniques to obtain session IDs.
In a brute force attack, the attacker can try many different session IDs. For example, the attacker can try to guess the session ID through URLs like:
- http://www.somesite.com/view/VW30422101518909
- http://www.somesite.com/view/VW30422101520803
- http://www.somesite.com/view/VW30422101522507
Session IDs can be stolen through a variety of techniques: monitoring network traffic, using trojans on the user's computer, or through parameters in the HTTP request string. In a 'referral' attack, the attacker tricks the user into clicking a link to a malicious website (like www.hostile.com). The browser then sends the referral URL containing the session ID to the attacker's site, and the attacker now has the user's session ID.
Additionally, session IDs can also be stolen through script injection techniques, such as Cross-Site Scripting. In this case, a malicious script can be executed, resulting in the user's personal information being redirected to the attacker.
Types of Session Hijacking Attacks
Cookie Stealing Attack
Session Hijacking is a form of cyber attack in which an attacker takes control of a user's session, allowing them to perform illegal actions such as stealing personal or financial information. Here are some common types of attacks in Session Hijacking:
- Brute Force: The attacker attempts to guess the session ID by trying different values until he finds the correct one. This attack is often effective on systems with weak security and using short, easy-to-guess session keys.
- Cross-Site Scripting (XSS): An attacker exploits a security vulnerability on a web server to inject malicious code into a web page. When a user visits the page, the malicious code captures their session cookie and sends it to the attacker.
- Malware: An attacker tricks a user into clicking on a link that contains malware. This software can perform "session sniffing" to search for and steal session cookies.
- Session Side Jacking: When a user connects to an unsecured Wi-Fi network, an attacker can use a "packet sniffing" technique to monitor network traffic and capture the user's session cookie.
- Session Fixation: The attacker deliberately creates a valid session ID and forces the victim to use that ID. Once the victim logs in, the attacker can hijack the session.
Common Session Hijacking Exploits
Here are some popular tools used to exploit Session Hijacking:
- CookieCadger: An open source tool that helps identify information leaks from web applications. It is capable of monitoring both wired and unsecured Wi-Fi networks for unencrypted session cookies.
- DroidSheep: This is an open source Android application that allows users to perform packet sniffing, in order to retrieve session cookies and other unprotected information from unsecured Wifi browsing sessions.
- FireSheep: An extension for the Firefox browser, FireSheep allowed attackers to use packet sniffing to find and copy unencrypted session cookies. However, this tool no longer works with newer versions of Firefox due to a security vulnerability that has been fixed.
- Paros Proxy: A web application analysis and security testing tool, Paros helps detect session hijacking related security vulnerabilities.
Consequences of Session Hijacking
When Session Hijacking attacks are effective, the attacker will have access to all servers, causing serious dangers such as:
- Data breach: Attackers may gain access to personal or sensitive company information, potentially leading to identity theft, financial fraud, or corporate espionage.
- Financial loss: Attackers can initiate unauthorized financial transactions, transfer money, or make purchases using the victim's account information.
- Reputational Damage: Businesses that fall victim to session hijacking can suffer significant damage to their reputation, resulting in loss of customer trust and potential revenue.
- Unauthorized System Access: In the case of single sign-on (SSO) implementations, a hijacked session can give an attacker access to multiple systems, multiplying the potential for damage.
- Compliance Violations: Depending on the industry and type of data compromised, session hijacking incidents can result in violations of data protection regulations, resulting in legal consequences and significant fines or sanctions.
How to Detect Session Hijacking
Recognizing signs of a compromised session is challenging, as attackers often operate inconspicuously. However, there are indicators, such as unusual account activity, that can indicate a breach. Tools and techniques, such as intrusion detection systems (IDSs), can monitor network traffic to detect misuse of session tokens. Anomaly-based detection mechanisms can also alert administrators to unusual session activity.
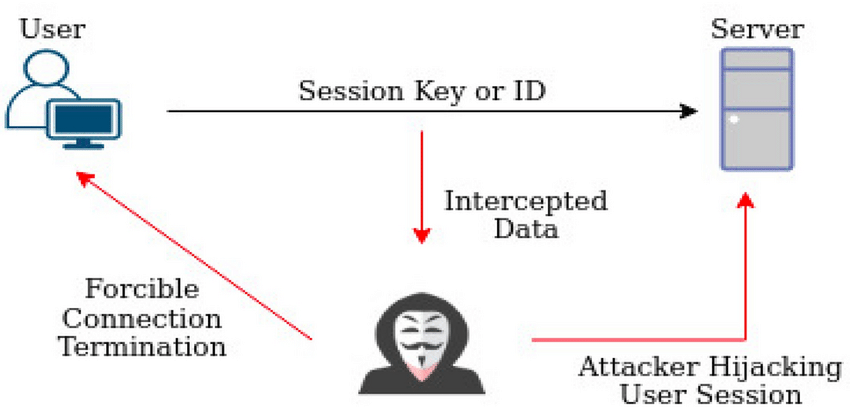
How to Detect Session Hijacking
However, implementing a detection system is only part of the solution. Continuous monitoring and regular security assessments are necessary to detect and address vulnerabilities before they are exploited. Security teams need to pay attention to unexpected changes in session duration or location, multiple concurrent sessions from different IP addresses, and suspicious patterns of session activity.
By combining advanced detection tools with proactive monitoring, businesses can more effectively mitigate the risk of session hijacking.
How to Prevent Session Hijacking
Use HTTPS and HSTS
Implementing HTTPS across your entire website encrypts all traffic between the user and the server, making it difficult for attackers to intercept session IDs. HTTP Strict Transport Security (HSTS) forces browsers to always use HTTPS connections, preventing downgrade attacks. This encryption protects against packet sniffing and man-in-the-browser attacks, greatly reducing the risk of session hijacking.
Implement powerful session management
Generate long, random, and complex session ID tokens using cryptographically secure methods. Pair these IDs with appropriate session expiration times and regenerate session IDs after important events such as successful authentication.
Validating the IP address of incoming requests against the session's associated IP, terminating sessions, or requiring additional authentication if there is a sudden change adds another layer of protection. These practices make it harder for attackers to break into the system by guessing or brute-forcing the session ID.
Enable HTTP and secure cookies
The 'HTTP-only' setting prevents client-side scripts from accessing session cookies and protects against cross-site scripting attacks. The 'secure' flag ensures cookies are only transmitted over HTTPS connections. These measures significantly reduce the risk of session cookies being stolen via common attack vectors.
Implement multi-factor authentication (MFA)
MFA adds an extra layer of security by requiring additional authentication methods beyond a password. Even if an attacker gains access to a session, they still need a second factor of authentication to gain full access. This significantly increases security, especially for sensitive activities or important data.
Session Hijacking Summary
Overall, Session Hijacking is a major threat to information security in today's digital world. Understanding how it works, common attack types, and how to detect and prevent it will help users and businesses better protect themselves against this threat.
By taking appropriate security measures and raising cybersecurity awareness, people can reduce their risk of being hacked and protect their personal information.
Conclude
Session Hijacking is a sophisticated form of attack, and understanding it is key to protecting yourself from potential threats. Hopefully, the information provided in this article will help you become more aware of this threat and take steps to prevent Session Hijacking attacks.