How to safely remove USB from computer
If you suddenly remove the USB while reading/writing data, the USB may be faulty and affect the data. The following article from TipsMake will guide you on how to safely remove the USB from the computer, follow along.
Instructions for safely removing USB from computer
Note : If you are copying data from USB to computer or vice versa, let the process complete.
Method 1:
Step 1: Click on the USB icon in the lower right corner of the screen.
Right click and select " Eject Mass Storage Device ".
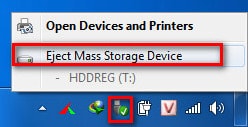
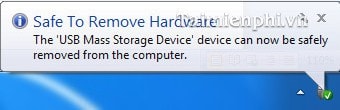
Step 2: A message will appear, saying it is safe to remove the USB. Close the message and remove the USB.
Method 2:
Go to Computer and right-click on the USB device and select Eject . Then remove the USB from the computer.

Method 3:
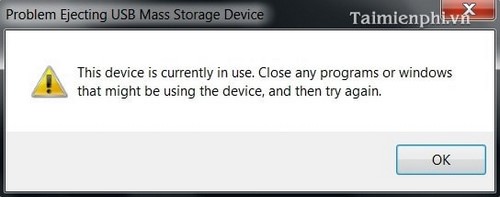
- If you have tried 2 ways to exit USB but still receive the message " This device is currently in use .", as shown below.
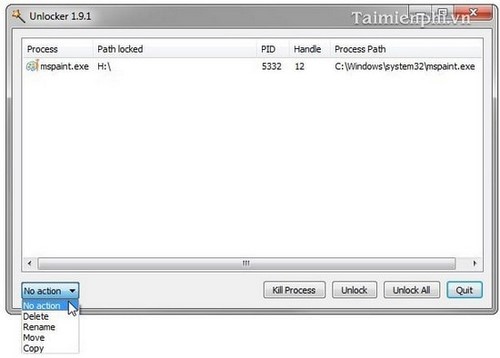
- The solution is to use Unlocker software to quickly remove the USB. Right-click on the USB drive, select Unlocker , delete running processes and select Quit .
You can download the latest version of Unlocker here.
The above article has instructed how to safely remove USB from the computer, helping to protect USB from damage and data loss when suddenly removed. In addition, you should use software to protect USB from viruses and keep data safe, available on TipsMake.
You should read it
- How will Safely Remove harm the device?
- Unplug USB safely, Fix 'Ejecting USB Mass Storage Device' error
- Instructions on how to safely remove the USB from the computer, disconnect the USB with the computer properly
- 5 simple ways to reconnect USB without 'unplugging'
- Bloatware list can be uninstalled or safely deleted from Android device synthesized by Androidsage
- How to completely remove Coc Coc?
 What is DHCP Snooping? How to configure DHCP Snooping effectively
What is DHCP Snooping? How to configure DHCP Snooping effectively What is Logic Bomb? How to Prevent Logic Bomb Effectively
What is Logic Bomb? How to Prevent Logic Bomb Effectively What is OCSP (Online Certificate Status Protocol)? Advantages and disadvantages of OCSP
What is OCSP (Online Certificate Status Protocol)? Advantages and disadvantages of OCSP How to completely remove W32.UsbFakeDrive Virus on computer and USB
How to completely remove W32.UsbFakeDrive Virus on computer and USB How to use Malwarebytes Anti-Malware to scan and remove malware
How to use Malwarebytes Anti-Malware to scan and remove malware What is Reflected XSS? How to know if you are attacked by Reflected XSS
What is Reflected XSS? How to know if you are attacked by Reflected XSS