What are Protocol Attacks? How to Detect and Prevent Attacks
Protocol Attacks are a form of cyberattack where attackers exploit vulnerabilities in communication protocols to disrupt or shut down a victim's service. These attacks can have serious consequences for businesses and individuals, ranging from data loss to massive financial losses. In this article, TipsMake takes a deep dive into Protocol Attacks, how they work, the different types of attacks, and how to detect and prevent them effectively.
What are Protocol Attacks?
Protocol Attacks are a type of cyber attack that exploits weaknesses in communication protocols. These protocols, commonly used in computer systems and networks, play a vital role in the transmission of data. When these protocols are exploited, attackers can generate illegal traffic, causing the system to become overloaded or to stop working completely.

What are Protocol Attacks?
How do Protocol Attacks work?
Protocol Attacks are attacks in which an attacker sends fake or excessive requests to overload or take control of a system. They are usually planned and can last for a period of time.
To perform Protocol Attacks, attackers will often use some tactics such as:
- IP address spoofing: Attackers hide their identities by spoofing IP addresses, making it difficult for the system to determine the origin of the request.
- Increase data complexity: Send large data packets or complex requests to overload the system.
- Exploiting security vulnerabilities: Attacking vulnerabilities in protocols to disrupt the system.
How many types of Protocol Attacks are there?
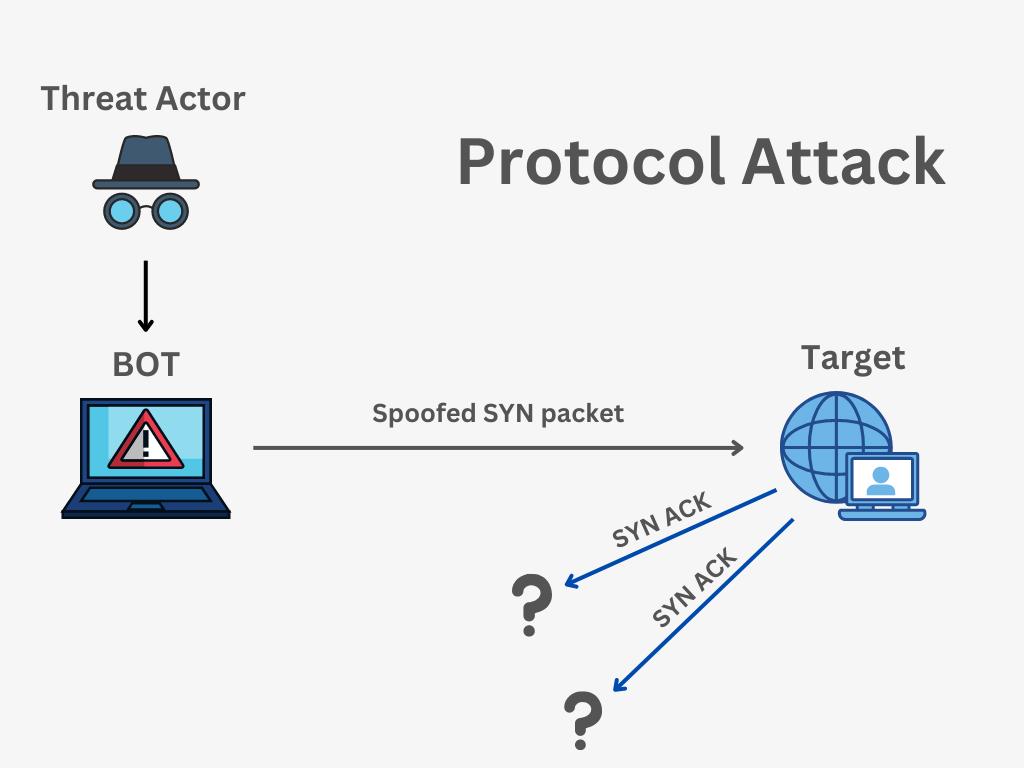
SYN Flood
SYN Flood is one of the most common types of protocol attacks. In this attack, an attacker sends a large number of SYN connection requests to a server without completing the connection process, causing the server to hold these connections in a waiting state. This can lead to exhaustion of the server's resources, making it unable to process valid requests from other users.
ICMP Flood
ICMP (Internet Control Message Protocol) Flood is a form of attack similar to UDP Flood, where an attacker sends a large number of ICMP (Internet Control Message Protocol) packets to the target server. The goal of this attack is to overload the server by processing a large number of ping requests, resulting in the inability to respond to valid requests from other users.
Ping of Death
Ping of Death is a type of attack in which an attacker sends an ICMP packet larger than the maximum allowed size (65535 bytes) to a server. When the server receives this packet, it will fail and may crash or restart. This is a serious security vulnerability in older versions of operating systems and network protocols.
Fraggle Attack
Fraggle Attack is a type of DDoS attack that uses the UDP (User Datagram Protocol) protocol to send a large amount of traffic to a network broadcast address. Similar to a Smurf Attack, a Fraggle Attack uses spoofed IP addresses to make many computers on the broadcast network respond to ping requests, causing an overload on the target system.
NTP Amplification
NTP (Network Time Protocol) amplification attack is a type of attack that exploits the Network Time Protocol (NTP). The attacker spoofs the source IP address and sends NTP requests to an NTP server. When the server responds, a large amount of traffic is sent to the target system, causing an overload and service disruption.
DNS Amplification
Similar to NTP amplification, DNS amplification attack is also an attack that relies on exploiting public DNS servers. The attacker sends DNS requests with spoofed source addresses, causing the DNS server to send a larger response to the victim.
How dangerous are Protocol Attacks?
Protocol Attacks are one of the major threats to today's network systems. They not only affect the ability to provide services but can also cause serious financial and reputational damage to businesses.
How dangerous are Protocol Attacks?
Financial loss
A successful attack can cause significant financial damage to a business. When systems are down, revenue can be lost, and the cost of restoring the system can be prohibitive. Furthermore, businesses must consider the cost of compensating customers if their services are disrupted.
Loss of data and information
In some cases, Protocol Attacks can result in the loss of valuable data. Attackers can exploit vulnerabilities in the protocol to gain access to sensitive information, posing a significant risk to businesses and individuals.
Impact on reputation
In addition to financial losses, a business's reputation can also be severely affected after an attack. Customers may lose confidence in a business's security capabilities, leading them to switch to competitors.
Difficulty in recovery
After an attack, restoring systems can be difficult. IT professionals must identify the source of the attack, patch vulnerabilities, and reestablish services. This process can be time-consuming and resource-intensive, impacting overall business operations.
How to prevent Protocol Attacks?
Use firewalls and WAFs
Configuring a firewall blocks unwanted traffic from suspicious IP addresses or known attack sources, helping to protect unnecessary ports and services. Installing a WAF helps filter and block malicious traffic before it reaches the application, protecting against common attacks such as SQL injection or XSS.
Traffic monitoring and analysis
To prevent Protocol attacks, you must constantly monitor. Set up a monitoring system to detect early signs of attacks, monitor traffic and receive notifications when there are abnormalities. At the same time, monitor normal requests to recognize when an abnormal situation occurs, thereby adjusting security policies promptly.
Increase Bandwidth and System Configuration
Increasing bandwidth will ensure that the system has enough bandwidth to handle larger traffic volumes, helping to maintain service performance even when under attack. In addition, the system needs to be configured to minimize weaknesses that can be exploited in protocol attacks.
Use anti-DDoS service
Hire an anti-DDoS service to protect your system from large-scale attacks, ensuring that only legitimate traffic is allowed to access your system.
Response planning
To avoid being caught off guard by Protocol Attacks or any other cyber attack, you need to have a plan in place to deal with them. This plan includes a process for notifying relevant parties and implementing timely countermeasures.
Conclude
Protocol Attacks are one of the biggest threats to businesses in today's cyber world. Therefore, businesses need to increase preventive measures such as using firewalls, traffic monitoring, software updates and employee training can help reduce the risk.