What are Volumetric Attacks? How to Detect and Prevent Them Effectively
Volumetric Attacks are one of the most common forms of cyber attacks today, causing a lot of damage to computer systems as well as information networks. These attacks occur by overloading the bandwidth of a service or a server, resulting in the inability to access that service. In this article, TipsMake will explore Volumetric Attacks in detail along with how to detect and prevent them effectively.
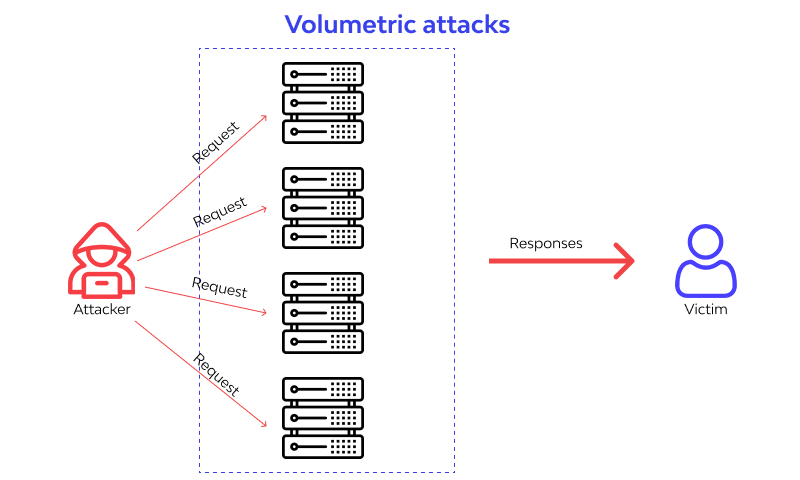
What are Volumetric Attacks?
Volumetric Attacks are a type of DDoS (Distributed Denial of Service) cyber attack. An attacker sends a large amount of unwanted data to a specific target in order to overload that system. The main goal of this type of attack is to make the system unable to process valid requests from users, resulting in service disruption and damage to real users.

How do Volumetric Attacks work?
In Volumetric Attacks, the attacker exhausts the bandwidth of the target network by overloading it to the point where it can no longer handle the incoming traffic. When overloaded, the system is disrupted and stops working, resulting in business losses. In this type of attack, the cumulative traffic sent to the target often exceeds the processing capacity of the internet connection, making it impossible for the connection to continue operating.
To perform Volumetric Attacks, attackers will use spoofing and reflection amplification tactics to increase the impact of the attack. Spoofing involves manipulating IP addresses so that responses are redirected to the victim's network. Reflection amplification effectively increases the volume of data in the network by requesting a higher than normal number of responses from unsuspecting intermediate servers.
How many types of Volumetric Attacks are there?
ICMP Floods
ICMP Flood is one of the simple but effective forms of Volumetric Attack. The attacker sends a large number of ICMP Echo Request packets (commonly known as pings) to the target server. When the server receives these packets, it sends back an ICMP Echo Reply packet. If the server receives too many ping requests, it will not be able to process valid requests from users, causing a service outage.
DNS Reflection Floods
DNS Reflection Floods are a type of attack that exploits a DNS server to flood traffic to a target. The attacker sends DNS requests to a DNS server with the target's IP address. The DNS server then replies to the request with the target's IP address, causing a sudden increase in network traffic to the server.
UDP Floods
UDP Floods are a type of Volumetric Attack similar to ICMP Floods, but using the UDP protocol instead of ICMP. The attacker sends a large number of UDP packets to random ports on the server. When the server receives these packets, it tries to respond but there is no service running on that port. As a result, the server becomes overloaded trying to handle all these requests.
TCP Out-of-State Floods
TCP Out-of-State Floods are a more complex attack in which an attacker sends a large number of TCP SYN requests to a server without completing the three-step TCP process. This causes the server to open many "half-baked" connections, wasting resources and resulting in the server being unable to process legitimate connections.
Reflection Amplification Attacks
Reflection Amplification Attacks are a sophisticated attack that combines elements of DNS Reflection Floods and ICMP Floods. The attacker sends a request to a server (usually a DNS or NTP server) with the target's IP address. These servers respond more aggressively than the original request, generating a large amount of traffic to the target.
How dangerous are Volumetric Attacks?
While Volumetric Attacks are primarily focused on causing congestion, in some cases they can be a sign of more sophisticated DDoS attacks. Attackers will prolong the disruption for hours to days in an attempt to gain access and steal information.
How dangerous are Volumetric Attacks?
In addition to causing disruptions in operations, Volumetric Attacks also cause consequences such as:
- Financial Loss: The downtime and resources required to mitigate a volumetric attack can result in significant financial loss. Businesses may face lost revenue, increased operating costs, and potential penalties.
- Reputational Damage: Frequent or prolonged service outages can erode customer confidence and damage a company's reputation. Customers and users may lose confidence in the reliability of the services provided.
- Increased operational costs: Implementing and maintaining robust security measures to combat volumetric attacks can be expensive. Continuous monitoring and updating of security protocols adds to these costs.
- Legal and compliance issues: Failure to protect against volume attacks can result in non-compliance with data protection laws and regulations, resulting in legal consequences and fines.
How to Prevent and Stop Volumetric Attacks?
To mitigate volumetric DDoS attacks, the following measures can be taken:
- DDoS Mitigation Services: Use professional services to filter and block malicious traffic before it reaches the target network.
- Use Blackhole Filtering: Redirect malicious traffic into a "black hole" to protect the main server, but be careful because it can block legitimate traffic as well.
- Rate Limiting: Controls the number of requests the server can handle in a given period of time.
- Set up a Web Application Firewall (WAF): Use a WAF to filter access requests based on certain rules to block malicious traffic.
- Telemetry Traffic Analytics: Apply telemetry analytics to detect traffic anomalies and automatically trigger mitigations.
- Use CDN: Use CDN to distribute traffic and reduce load on main server.
- Increase bandwidth and servers: Invest in bandwidth and upgrade servers to better handle large attacks.
Conclude
Volumetric Attacks are one of the most common and dangerous forms of cyber attacks today. However, with proper preparation and precautions, organizations can minimize the risk and protect their infrastructure from these threats. Hopefully, the above article from TipsMake has helped you understand more about this form of DDoS attack.
You should read it
- ★ The 4 most popular network attacks towards older people in 2018
- ★ DNS attacks are costing governments worldwide huge amounts
- ★ Microsoft warns of an increasing trend of attacks targeting firmware and worrying public indifference
- ★ Learn about DoS and DDoS denial of service attacks
- ★ What are Protocol Attacks? How to Detect and Prevent Attacks