If you are struggling to figure out why a file refuses to be deleted, then File Locksmith might be the utility you need. This new addition to the PowerToys toolkit can help you

WARP is a VPN that helps you connect to the Internet using Cloudflare's DNS 1.1.1.1 and optimizes and secures (i.e. encrypts) your connection. 1.1.1.1 is one of the fastest and

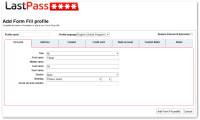
Passwords keep valuable data safe from malicious actors, so it's important to make their safe storage an absolute priority.

In cybersecurity, nothing is more important than keeping sensitive information private and safe. Everyone should make an effort to do so, from individuals to large organizations.

WebRTC (Web Real-Time Communication) is an open source technology that enables peer-to-peer communication in web browsers and similar applications.

The BitLocker feature on Windows 11 (Professional, Enterprise and Education editions) is designed to encrypt the hard drive to better secure user data. However, for many reasons,

In order to avoid having to remember long passwords and be considered safe, many people use online password management software, to be able to generate the most diverse passwords

Researchers from security firm Trellix have discovered an unauthenticated remote code execution (RCE) vulnerability affecting 29 models of DrayTek routers.

Proxy sites are often used by people who want to access blocked sites but don't want to spend money to buy a separate VPN connection.

Finally 7-zip also adds support for the long-requested Windows Mark-of-the-Web security feature.

The newly discovered vulnerability is called Follina and currently there is no official patch from Microsoft.

A new Windows Search vulnerability can be exploited to automatically open a search window containing remotely hosted malicious executable files just by launching a Word document.

ChromeLoader malicious code can attack victims on many levels, mildly annoying, but heavy can cheat or install more malicious code, ransomware.

Password managers aren't perfect. And not everyone likes the idea of storing all of their passwords in a single location.

If you have one of the apps installed below, remove it from your phone right away to protect your Facebook account and cryptocurrencies.

Ransomware is a worrisome online threat. If it's installed on your computer, you not only risk paying a ransom to get your files back, but you also potentially won't get them back

Users who are using affected laptop models should update to the latest firmware to be on the safe side.

Microsoft's internal antivirus program mainly implements protection of cloud-based systems that connect to the internet.

Windows' default firewall and anti-virus program should be more than enough for most people. However, there is one thing these programs lack, and that is customizability. And

Many reliable VPN providers offer free options that, while limited in features, are effective at keeping you safe online and hiding your physical location.
 If you are struggling to figure out why a file refuses to be deleted, then File Locksmith might be the utility you need. This new addition to the PowerToys toolkit can help you
If you are struggling to figure out why a file refuses to be deleted, then File Locksmith might be the utility you need. This new addition to the PowerToys toolkit can help you WARP is a VPN that helps you connect to the Internet using Cloudflare's DNS 1.1.1.1 and optimizes and secures (i.e. encrypts) your connection. 1.1.1.1 is one of the fastest and
WARP is a VPN that helps you connect to the Internet using Cloudflare's DNS 1.1.1.1 and optimizes and secures (i.e. encrypts) your connection. 1.1.1.1 is one of the fastest and Passwords keep valuable data safe from malicious actors, so it's important to make their safe storage an absolute priority.
Passwords keep valuable data safe from malicious actors, so it's important to make their safe storage an absolute priority. In cybersecurity, nothing is more important than keeping sensitive information private and safe. Everyone should make an effort to do so, from individuals to large organizations.
In cybersecurity, nothing is more important than keeping sensitive information private and safe. Everyone should make an effort to do so, from individuals to large organizations. WebRTC (Web Real-Time Communication) is an open source technology that enables peer-to-peer communication in web browsers and similar applications.
WebRTC (Web Real-Time Communication) is an open source technology that enables peer-to-peer communication in web browsers and similar applications. The BitLocker feature on Windows 11 (Professional, Enterprise and Education editions) is designed to encrypt the hard drive to better secure user data. However, for many reasons,
The BitLocker feature on Windows 11 (Professional, Enterprise and Education editions) is designed to encrypt the hard drive to better secure user data. However, for many reasons, In order to avoid having to remember long passwords and be considered safe, many people use online password management software, to be able to generate the most diverse passwords
In order to avoid having to remember long passwords and be considered safe, many people use online password management software, to be able to generate the most diverse passwords Researchers from security firm Trellix have discovered an unauthenticated remote code execution (RCE) vulnerability affecting 29 models of DrayTek routers.
Researchers from security firm Trellix have discovered an unauthenticated remote code execution (RCE) vulnerability affecting 29 models of DrayTek routers. Proxy sites are often used by people who want to access blocked sites but don't want to spend money to buy a separate VPN connection.
Proxy sites are often used by people who want to access blocked sites but don't want to spend money to buy a separate VPN connection. Finally 7-zip also adds support for the long-requested Windows Mark-of-the-Web security feature.
Finally 7-zip also adds support for the long-requested Windows Mark-of-the-Web security feature. The newly discovered vulnerability is called Follina and currently there is no official patch from Microsoft.
The newly discovered vulnerability is called Follina and currently there is no official patch from Microsoft. A new Windows Search vulnerability can be exploited to automatically open a search window containing remotely hosted malicious executable files just by launching a Word document.
A new Windows Search vulnerability can be exploited to automatically open a search window containing remotely hosted malicious executable files just by launching a Word document. ChromeLoader malicious code can attack victims on many levels, mildly annoying, but heavy can cheat or install more malicious code, ransomware.
ChromeLoader malicious code can attack victims on many levels, mildly annoying, but heavy can cheat or install more malicious code, ransomware. Password managers aren't perfect. And not everyone likes the idea of storing all of their passwords in a single location.
Password managers aren't perfect. And not everyone likes the idea of storing all of their passwords in a single location. If you have one of the apps installed below, remove it from your phone right away to protect your Facebook account and cryptocurrencies.
If you have one of the apps installed below, remove it from your phone right away to protect your Facebook account and cryptocurrencies. Ransomware is a worrisome online threat. If it's installed on your computer, you not only risk paying a ransom to get your files back, but you also potentially won't get them back
Ransomware is a worrisome online threat. If it's installed on your computer, you not only risk paying a ransom to get your files back, but you also potentially won't get them back Users who are using affected laptop models should update to the latest firmware to be on the safe side.
Users who are using affected laptop models should update to the latest firmware to be on the safe side. Microsoft's internal antivirus program mainly implements protection of cloud-based systems that connect to the internet.
Microsoft's internal antivirus program mainly implements protection of cloud-based systems that connect to the internet. Windows' default firewall and anti-virus program should be more than enough for most people. However, there is one thing these programs lack, and that is customizability. And
Windows' default firewall and anti-virus program should be more than enough for most people. However, there is one thing these programs lack, and that is customizability. And Many reliable VPN providers offer free options that, while limited in features, are effective at keeping you safe online and hiding your physical location.
Many reliable VPN providers offer free options that, while limited in features, are effective at keeping you safe online and hiding your physical location.