New zero-day vulnerability warning in Windows Search, Windows protocol nightmare getting worse
This security issue can be abused by hackers because Windows supports a URI protocol handler called "search-ms" that allows apps and HTML links to launch custom searches on the device.
We can force Windows Search to query file shares on remote servers and use a custom title for the search window, although most Windows searches will be based on the device's local index.
For example, the Sysinternals Toolkit allows you to remotely mount live.sysinternals.com as a network share to launch their utilities. To search this remote share and list only files that match a specific name, you can use the following "search-ms" URI:
search-ms:query=proc&crumb=location:%5C%5Clive.sysinternals.com&displayname=Searching%20Sysinternals
As you can see in the above command, the search-ms variable "crumb" specifies the location to search and the variable "displayname" specifies the search title.
A custom search window will appear when this command is executed from Run or the web browser address bar on Windows 7, Windows 10 and Windows 11 like the image below:

Notice how the window title is set to the "Searching Sysinternals" display name we specified in the search-ms URI.
Hackers can use this same method for cyber attacks. In it, they can attach malicious documents masquerading as security updates or patches that need to be installed in the email and then send it.
Alternatively, they can set up a remote Windows share to save malicious code disguised as updates and then include the search-ms URI in their phishing emails.
However, it won't be easy to trick users into clicking on such a URL, especially when a warning pops up every click like this:
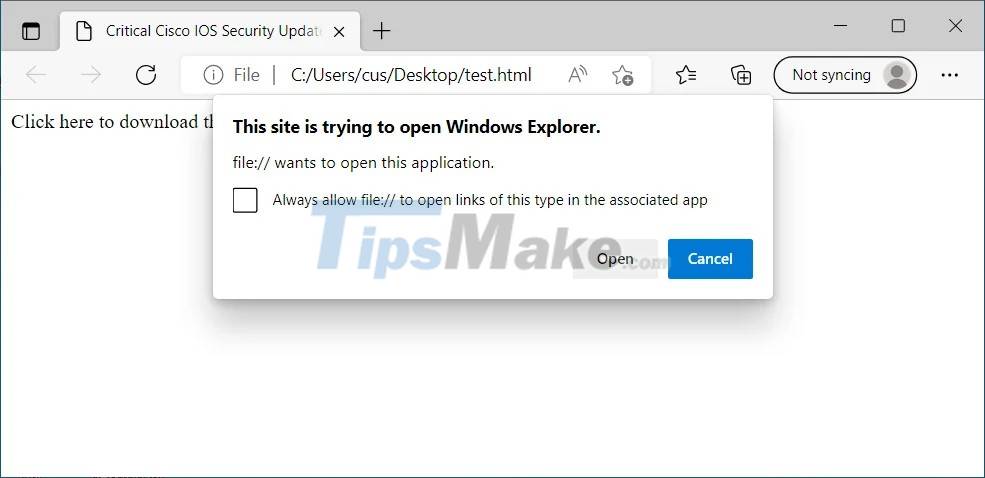
But Hacker House co-founder and security researcher, Matthew Hickey, has found a more effective attack. By combining the newly discovered Microsoft Office OLEObject vulnerability with the search-ms protocol handler, an attacker could open a remote search window just by launching a Word document.
Microsoft Office takes the search-ms vulnerability to the next level
This week, researchers discovered that hackers are exploiting a new Windows zero-day vulnerability in the Microsoft Windows Support Diagnostic Tool (MSDT). To exploit it, the hacker created malicious Word documents that launch the "ms-msdt" URI protocol handler to execute PowerShell commands simply by opening the document.
Codenamed CVE-2022-30190, the vulnerability allows an attacker to modify a Microsoft Office document to bypass Protected View and launch a URI protocol handler without user interaction. This leads to a higher degree of protocol handler abuse.
Hickey succeeded in converting existing Microsoft Word MSDT exploits to use the search-ms protocol handler mentioned above.
With these new exploits, when a user opens a Word document, it automatically launches the "search-ms" command to open a Windows Search window listing the remote shared SMB executables. This share can be named anything the hacker wants, such as "Important Update" to trick users into installing malicious software.
Like the MSDT exploit, Hickey also showed that you can create RTF instances that automatically open the Windows Search window when a document is displayed in the Explorer preview pane.
Using this method of using malicious Word documents, hackers can create complex phishing campaigns, manually launching Windows Search windows on victims' machines to trick them into running malware.
Although this exploit is not as severe as the MS-MSDT remote code execution vulnerability, it can lead to abuse by amateur hackers who want to create sophisticated phishing campaigns.
Although we have found a way that hackers can exploit the new vulnerability, for safety reasons experts will not share details.
To mitigate this vulnerability, Hickey says you can use the same mitigations for the ms-msdt vulnerability. That is, you need to remove the search-ms protocol handler from the Windows Registry. How to do this:
- Open Command Prompt with admin rights.
- Backup the Registry with the following command: "reg export HKEY_CLASSES_ROOT/search-ms search-ms.reg".
- Run this command to delete search-ms: "reg delete HKEY_CLASSES_ROOT/search-ms /f".
- If you need to restore search-ms, enter the following command: "reg import search-ms.reg".
Windows Protocol Nightmare
Both examples of MSDT and search-ms abuse are nothing new. In 2020, in his thesis on Electron application security, Benjamin Altpeter revealed about these issues.
However, it was not until recently that they were weaponized in malicious Word documents for phishing attacks that require no user interaction. This has turned them into zero-day vulnerabilities.
Based on Microsoft's security guidance for CVE-2022-30190, it seems that the company is only addressing bugs in their protocol handlers and basic Windows features, not focusing on agents. Threats can abuse Microsoft Office to launch these URIs without user interaction.
Like Will Dormann, CERT/CC vulnerability analyst, said these exploits use two different vulnerabilities. If the Microsoft Office URI issue is not fixed, other protocol handlers will be abused.
Hickey also shared that this is not necessarily a vulnerability in the protocol handler, but rather a combination that leads to a Microsoft Office OLEObject search-ms Path Spoofing Vulnerability.
Only when Microsoft is set up to not be able to run the URI handler in Microsoft Office without user interaction will the problem be resolved.
You should read it
- ★ Microsoft urgently patched zero-day vulnerability after 2 years of refusing to acknowledge it
- ★ Steps to fix PrintNightmare vulnerability on Windows 10
- ★ Detecting zero-day vulnerability in the Dropbox 10 Windows app, users pay attention!
- ★ AMD CPUs also have security vulnerabilities that have existed for many years now!
- ★ Critical Vulnerability Discovered in 3 WordPress Plugins, Affects 84,000 Websites