Sharing folders between two Windows 7 computers is quite simple, you can use the HomeGroup feature. However, the HomeGroup feature is not compatible on Windows XP and Windows

Did you know that every day we are using a whole range of Google services: search engines, Gmail services, Play Store, and many other services. Therefore protecting your Google

When searching for information about Akamai on Google or many other Search Engine, we will get the answer, information about Akamai Technologies, Inc. is the CDN network system -

Nobody likes to surf the web but the network jerks or loads an unfinished page. This will greatly affect the work you are doing. The solution is to redirect connectivity to

On NTFS-formatted hard drive partitions, you can set security permissions for files and folders. This permission allows you to access or deny access to files and folders. To set

FAT32 and NTFS are two familiar formats of a partition, hard drive, or any storage device connected to a Windows computer. And NTFS format is chosen for more use because of some

Since the Internet has grown, many services have blossomed with different features to support users. However, along with that, each person's personal information becomes more and

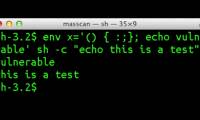
Microsoft has released an official security warning regarding zero-day vulnerabilities in IE10 last week and said IE 9 is also vulnerable.

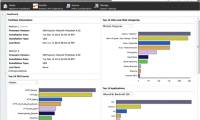
In the context of many experts warning about the explosion of cyberattacks and the increasing complexity of current cyber threats, IBM has partnered with FPT Trading Company (FPT

Security experts offer advice to help users protect themselves safe from the security hole Heartbleed is spreading terror to the web world.

The rate of malware infection in growing organizations suggests that anti-virus software has become obsolete, needs technological innovation and has different ways for this tough

Unfortunately for fans of popular encryption software, TrueCrypt on the program's official website has a red text warning that TrueCrypt is no longer safe to continue using. The

Many users sometimes get confused when using BlackBerry 10, maybe you still have difficulties in changing and setting ID password on BlackBerry 10. Here I would like to guide how

Menus The account settings (Account Settings) of Google have not changed, but the interface of the installer has new things. That is adding 5 important security settings to your

The main advice for computer users is to always check for the latest software updates as soon as possible.

Almost every recent study of security vulnerabilities has come to the same conclusion: people are more risky factors for a business than technology gaps.

Protect your ATM card from damage by keeping it in a safe place. Keep the card from being bent or scratched. Remember your personal identification number (PIN). When choosing a

Using management tools is the best way to generate random passwords and is highly secure for logging in to many different websites. However, the problem is that password

According to McAfee, in the third quarter of 2014, the number of infected mobile devices exceeded 5 million. Another statistic of security firm Symantec in 2014 also found that 1

In fact, there are many self-extracting software and password for compressed files, but the most simple and popular is WinRAR. Please refer to our tutorial below to learn how to
 Sharing folders between two Windows 7 computers is quite simple, you can use the HomeGroup feature. However, the HomeGroup feature is not compatible on Windows XP and Windows
Sharing folders between two Windows 7 computers is quite simple, you can use the HomeGroup feature. However, the HomeGroup feature is not compatible on Windows XP and Windows Did you know that every day we are using a whole range of Google services: search engines, Gmail services, Play Store, and many other services. Therefore protecting your Google
Did you know that every day we are using a whole range of Google services: search engines, Gmail services, Play Store, and many other services. Therefore protecting your Google When searching for information about Akamai on Google or many other Search Engine, we will get the answer, information about Akamai Technologies, Inc. is the CDN network system -
When searching for information about Akamai on Google or many other Search Engine, we will get the answer, information about Akamai Technologies, Inc. is the CDN network system - Nobody likes to surf the web but the network jerks or loads an unfinished page. This will greatly affect the work you are doing. The solution is to redirect connectivity to
Nobody likes to surf the web but the network jerks or loads an unfinished page. This will greatly affect the work you are doing. The solution is to redirect connectivity to On NTFS-formatted hard drive partitions, you can set security permissions for files and folders. This permission allows you to access or deny access to files and folders. To set
On NTFS-formatted hard drive partitions, you can set security permissions for files and folders. This permission allows you to access or deny access to files and folders. To set FAT32 and NTFS are two familiar formats of a partition, hard drive, or any storage device connected to a Windows computer. And NTFS format is chosen for more use because of some
FAT32 and NTFS are two familiar formats of a partition, hard drive, or any storage device connected to a Windows computer. And NTFS format is chosen for more use because of some Since the Internet has grown, many services have blossomed with different features to support users. However, along with that, each person's personal information becomes more and
Since the Internet has grown, many services have blossomed with different features to support users. However, along with that, each person's personal information becomes more and Microsoft has released an official security warning regarding zero-day vulnerabilities in IE10 last week and said IE 9 is also vulnerable.
Microsoft has released an official security warning regarding zero-day vulnerabilities in IE10 last week and said IE 9 is also vulnerable. In the context of many experts warning about the explosion of cyberattacks and the increasing complexity of current cyber threats, IBM has partnered with FPT Trading Company (FPT
In the context of many experts warning about the explosion of cyberattacks and the increasing complexity of current cyber threats, IBM has partnered with FPT Trading Company (FPT Security experts offer advice to help users protect themselves safe from the security hole Heartbleed is spreading terror to the web world.
Security experts offer advice to help users protect themselves safe from the security hole Heartbleed is spreading terror to the web world. The rate of malware infection in growing organizations suggests that anti-virus software has become obsolete, needs technological innovation and has different ways for this tough
The rate of malware infection in growing organizations suggests that anti-virus software has become obsolete, needs technological innovation and has different ways for this tough Unfortunately for fans of popular encryption software, TrueCrypt on the program's official website has a red text warning that TrueCrypt is no longer safe to continue using. The
Unfortunately for fans of popular encryption software, TrueCrypt on the program's official website has a red text warning that TrueCrypt is no longer safe to continue using. The Many users sometimes get confused when using BlackBerry 10, maybe you still have difficulties in changing and setting ID password on BlackBerry 10. Here I would like to guide how
Many users sometimes get confused when using BlackBerry 10, maybe you still have difficulties in changing and setting ID password on BlackBerry 10. Here I would like to guide how Menus The account settings (Account Settings) of Google have not changed, but the interface of the installer has new things. That is adding 5 important security settings to your
Menus The account settings (Account Settings) of Google have not changed, but the interface of the installer has new things. That is adding 5 important security settings to your The main advice for computer users is to always check for the latest software updates as soon as possible.
The main advice for computer users is to always check for the latest software updates as soon as possible. Almost every recent study of security vulnerabilities has come to the same conclusion: people are more risky factors for a business than technology gaps.
Almost every recent study of security vulnerabilities has come to the same conclusion: people are more risky factors for a business than technology gaps. Protect your ATM card from damage by keeping it in a safe place. Keep the card from being bent or scratched. Remember your personal identification number (PIN). When choosing a
Protect your ATM card from damage by keeping it in a safe place. Keep the card from being bent or scratched. Remember your personal identification number (PIN). When choosing a Using management tools is the best way to generate random passwords and is highly secure for logging in to many different websites. However, the problem is that password
Using management tools is the best way to generate random passwords and is highly secure for logging in to many different websites. However, the problem is that password According to McAfee, in the third quarter of 2014, the number of infected mobile devices exceeded 5 million. Another statistic of security firm Symantec in 2014 also found that 1
According to McAfee, in the third quarter of 2014, the number of infected mobile devices exceeded 5 million. Another statistic of security firm Symantec in 2014 also found that 1 In fact, there are many self-extracting software and password for compressed files, but the most simple and popular is WinRAR. Please refer to our tutorial below to learn how to
In fact, there are many self-extracting software and password for compressed files, but the most simple and popular is WinRAR. Please refer to our tutorial below to learn how to