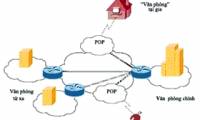
Domain Controller virtualization solutions - Part 1
in this article we will show you the advantages and disadvantages of some common domain controller settings.

in this article we will show you the advantages and disadvantages of some common domain controller settings.

today april 15, 2011, hp group announced the integration of 3par utility storage system into the product portfolio under hp's converged infrastructure solution, the integration to

in recent years, e-commerce services (e-commerce) such as online payment, ebanking online transactions ... have developed constantly.

attack surface analyzer is a tool released by microsoft that allows users to easily detect sensitive security changes of the windows operating system.

in a conference of it industry leaders in march, it managers expressed their concerns about the security of virtual infrastructure.
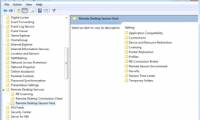
in this article we will discuss some of the security mechanisms included in rds along with how to use group policy and configuration settings.

hackers design fake websites to scare internet users to download and install fake antivirus software.

network administration - you can avoid some problems and get the most out of it by following some advice when upgrading the server.
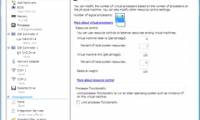
in this article, i will show you the options for controlling processor resources and how to use them.

to back up the database for wordpress, there are many plugins that can help you do this. however, if you are a longtime wordpress user, you will probably realize that the plugins