Security for web applications
In recent years, e-commerce services (e-commerce) such as online payment, ebanking online transactions . have developed constantly. The more utilities are developed, the more enterprises (enterprises) must equip professional network infrastructure to meet the needs of continuous operation and system security.
Privacy conditions
 A secure network system must always ensure objectives such as: Allowing or prohibiting access services; Allow or prohibit services from outside access; Monitor network data flow between Internet and Intranet (intranet); Control and prohibit access address; User control and user access; Control the content of information circulating on the network.
A secure network system must always ensure objectives such as: Allowing or prohibiting access services; Allow or prohibit services from outside access; Monitor network data flow between Internet and Intranet (intranet); Control and prohibit access address; User control and user access; Control the content of information circulating on the network.
With the requirements and objectives set by enterprises, system integrators will advise and build a complete network system:
+ External connections include ADSL, Lease-line . routers and load balancing devices.
+ Secure connection: Firewall devices (Firewall), IDS / IPS attack prevention systems . and system monitoring software.
+ Server system: servers (servers) install Windows, Linux operating systems . and solutions to prevent viruses, fight spam (spam mail) .
+ Storage system: SAN data storage devices (Storage Area Network) .

Investing in security system
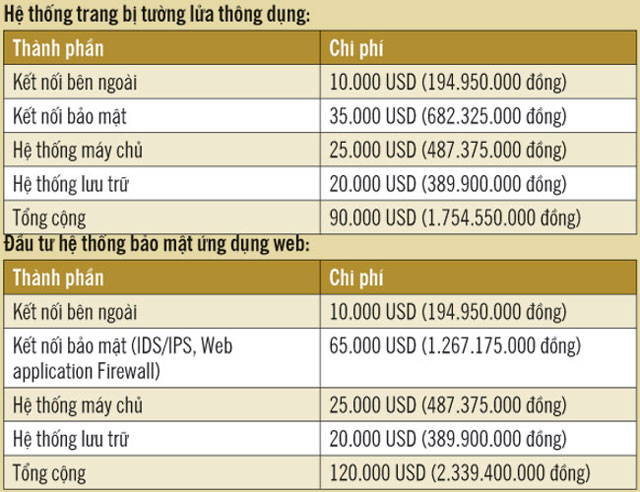
Is it really perfect to invest in a security system that meets the standards that system integrators bring to businesses? Enterprises can refer to the evaluation table of security companies:
We see some outstanding issues in information security such as: Firstly, attacks and encroachments on DN web site systems take place more and more continuously and sophisticatedly (25.48% Unidentified attack). Secondly, server systems are equipped with all advanced security solutions that are still subject to direct attack without complete blocking.
According to statistics of the current popular network attack methods, traditional attacks such as SQL Injection, Cross-Site Script, Brute Force . are still causing damage to the network despite being warned from very long.
According to the statistics of the current attack methods (Figure 1), we see the traditional attacks such as SQL Injection, Cross-Site Script, Brute Force . are still causing damage to the network even though the scene has been shot. newspaper for a long time.
These attacks mainly focus on web applications developed in e-commerce services with the web 2.0 application platform. Security issues for current applications in general and web applications in particular are still quite 'new' for Vietnamese enterprises.
An enterprise needs to implement an e-commerce application, they will perform the following steps: Building applications according to business needs and this will be designed and built by a group of programmers; Next is to equip the network infrastructure to deploy this application.
Current security devices such as firewall, IPS / IDS will not be able to monitor and evaluate all web-based applications (specifically, HTTP / HTTPS protocol). Only the web application protection devices before attacks - Web Application Firewall (WAF) are new to meet this requirement.
A dedicated firewall will do the following tasks:
+ Set policies for HTTP user connections through content selection for web service servers.
+ Protecting the system against common types of attacks on the network such as Cross-site Scripting (XSS) and SQL Injection.
+ In addition to the inspection actions of a normal firewall, WAF will examine further, will check the HTTP content in the application layer.
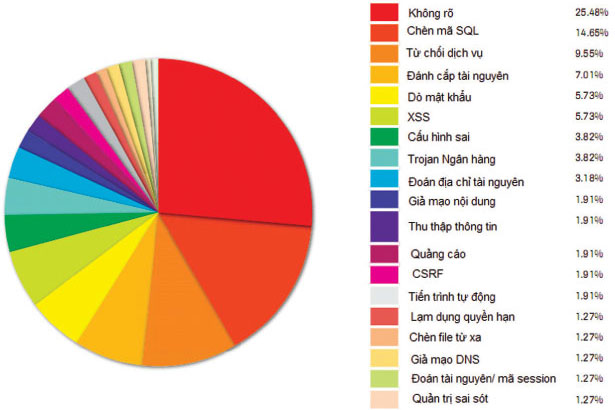
Figure 1. Report the risk of Web attacks
Web application security solutions are expressed as follows:
Web application security solutions will better support:
+ Minimize attacks and applications through the device application protection Web application (Web Application Firewall).
+ Focus on developing and building web applications in accordance with Web 2.0 standards with the highest web security criteria (PCI DSS, OWASP .)
+ The ability to monitor and prevent attacks with depth and concentration.
+ Improve the performance of the system, maximize the security features of each device in the system.
Need application security?
 Currently, in the world, the web application security projects in e-commerce have developed over 2 years and there are many solutions for this problem. Besides, there are also some organizations that regularly analyze, value and offer the latest security criteria. We can mention OWASP (Open Web Application Security Project), a non-profit organization that provides the community with risks arising in web applications.
Currently, in the world, the web application security projects in e-commerce have developed over 2 years and there are many solutions for this problem. Besides, there are also some organizations that regularly analyze, value and offer the latest security criteria. We can mention OWASP (Open Web Application Security Project), a non-profit organization that provides the community with risks arising in web applications.
In Vietnam, businesses still do not have the exact concept of potential risks in web applications. We still have not identified the risks and errors on the website to lead to the threat of network attacks.
Enterprises are aiming for e-commerce or web-based applications that need to enhance security requirements for applications. Enterprises should learn about security issues when building applications. For example: Using NoSQL language to replace traditional SQL language has been 'outdated' and has many risks. Using open source tools such as Metasploit, SQLmap, Firecat . check and evaluate vulnerabilities in the network.
Develop system risk assessment forms (refer to OWASP, WASC security standards .) to classify risks to take specific actions when incidents occur. If possible, use a professional PenTest (system safety survey) service to limit the risks of an external attack.
In addition, businesses should also organize short-term and long-term courses on information security to raise the awareness of security for employees. Actively explore security processes and standards such as ISO 27000, 27001 . Adjust applications with the support of programmers to review applications, upgrade the system and conduct a system survey ( Audit) annually to assess the status of the application.
Information security requires individuals, organizations and businesses to constantly improve and develop continuously. Web applications provide users and businesses with many utilities, but also become an environment for 'profiteering' hackers. Before deploying business applications, businesses need to pay attention to the security of web applications.