How to Change the Icon for an Exe File
this wikihow teaches you how to change an exe file's icon on a windows computer. while you can't normally change the icon of an exe file itself, you can create a shortcut for the
this wikihow teaches you how to change an exe file's icon on a windows computer. while you can't normally change the icon of an exe file itself, you can create a shortcut for the
the exe project is developing a freely available open source authoring application to assist teachers and academics in the publishing of web content without the need to become
this wikihow will teach you you how to create a basic exe file on a windows computer, as well as how to create a container for that file that will install it on another computer.
computer files with an '.exe' extension are called executables, or exe files. this type of file is one of the most ubiquitous in the windows operating system, where it is used to

service applications on windows can run in the background and not interfere with the user interface, making them ideal for anyone who wants programs that work in the background.

bored of your start menu in windows xp? wish you could have it say and do something a little more interesting? follow these easy steps and you'll have a personalized start button

in the previous articles, we have been introduced to some concepts and issues around remote windows scripting. in this section, i will continue the discussion by showing you two

suppose we have windows xp professional operating system with the password set for the administrator account. when we turn on the computer and enter the login screen. then the

svchost viewer is a small application that lists all running svchost.exe processes, how much memory each process is using ..
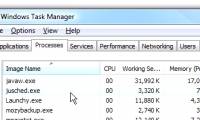
this process is actually a java update timetable, which actually consumes a lot of memory just to check once a month for java updates.