Binder and Malware (Part 2)
 Binder and Malware (Part 1)
Binder and Malware (Part 1)
Don Parker
In Part 1, we learned how to configure the Optix Pro server to be a piece of malware. This is the trojan server that we will join the official Pong.exe game program using a binder program called YAB. Binder is a program that will need two executable files and combine them simultaneously. By combining it does not mean mixing them together like components inside a cake, Binder YAB will need trojan servers and Pong.exe, then combine them into another component. Thinking about it is like a 12 cm ruler that is divided into 2 6 cm pieces but even after that it makes a 12 cm ruler. This will be shown quite clearly later, so you don't need to worry if it still feels a little confusing.
binder YAB
There are many different types of binders that we can find on the Internet. One of the most simple and featured binder is YAB. It is the abbreviation for ' Yet Another Binder '. When you find and download a program on the Internet, be careful before waking it up. Notice the following dialog box:

Figure 1
You will see that a small dialog box called ' Icon Preview ' is not shown in the image above. This is because the software program we use cannot capture it (you can detect this through the outline of the icon). Now we need to go to the Pong.exe program, which is the means to distribute malware, we will link trojan server with Pong.exe file. You can click here to get this file. Once you find this file on that page, quickly download it to your computer. Now we have the tools to get ready to go, start our process of linking malware to the Pong.exe file. The first step is to click on the ' Command ' menu, then ' Add Command '.

Figure 2
We will only comment on the information to fill in here or change to use the correct YAB. We do not comment directly on the default settings, but the first step is to click on ' Browse ' under the ' Bind File ' box in the image above. You need to find the file you want to combine. In this case, we went to the Optix Pro trojan server configured in Part 1. Notice the following figure, we found the directory with all the parts of Optix Pro trojan and selected the server that was built. in part 1.
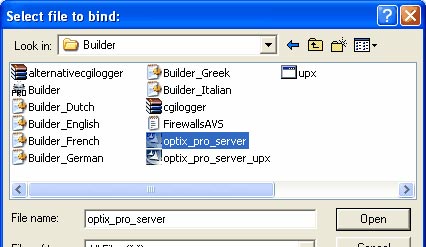
Figure 3
There are many options available here, so that you can see more details about them, you can click the ' Show Advanced ' tab in Figure 2. Once you have enabled this option, you will see a screen appear.

Figure 4
You will see that the default ' Execution Method ' is set to ' Execute asynchronously '. This means that when a disguised malware is clicked, it will automatically install silently without the user knowing. While the official Pong.exe file installs itself with regular dialog boxes that appear to users. The effects of malware will not be noticed by the naked eye so users are not suspicious but just think they are installing a file playing Pong.exe game. We don't want to get bogged down with YAB's features. With the information entered as described, we are ready to move on to the next step, click ' OK '.
Figure 5
Now we will go straight to the problem and do the same, but for now we will do it for Pong.exe file. Press ' Command ' then ' Add Command '. Similar to the steps above: click ' Browse ' and navigate to the place where the Pong.exe file is located, then click on it. When you have done this, click ' OK '.
Figure 6
Now we have both programs waiting to be combined via YAB. The next step is to select an icon for our malware. The best way is to choose the old icon of the Pong.exe file. You need to click on the Change Icon button. If you hover over it, it will appear from ' Change icon (F8) '.
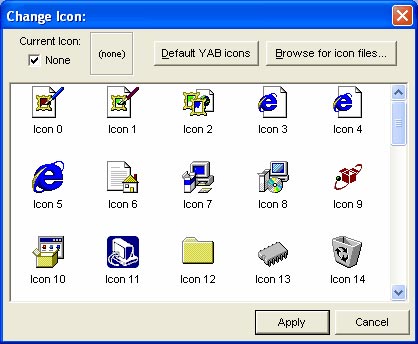
Figure 7
From the window after clicking Change Icon you find the place to store Pong.exe through ' Browse for icon files . ' as shown in Figure 7. Once you have found it, click on its icon.
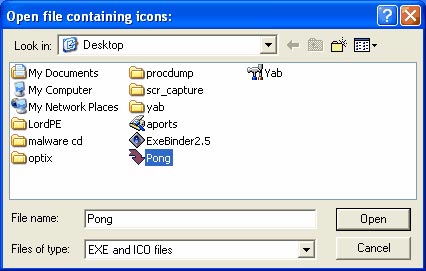
Figure 8
When you have made your selection, click ' Open ', then click ' Apply '. From here you need to click on the ' Tools ' menu in the YAB window. From that menu, click the ' Build ' button. A window will appear as shown below.
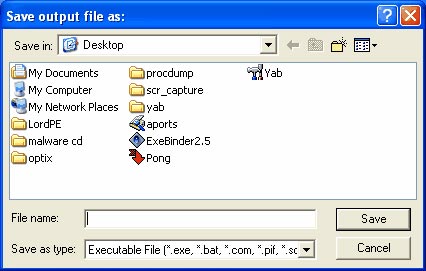
Figure 9
Now name it. In our case, the best way is to choose Pong.exe to match the meaning of the job. Once you have entered the name, press ' Save '. YAB will do the work of combining Optix Pro trojan with Pong.exe game.
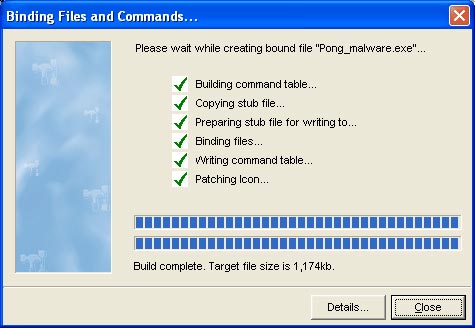
Figure 10
Conclude
We have succeeded in putting a malware into the media that distributes them: Pong.exe . This is how malware is built when trying to control settings on a user's home or company computer. What we've just done seems to be the things that conventional malware creators do. So what will need to be mentioned later in this section, is that we need to dissect to find out what happens when the malware is executed and from there can stop their harm.
 Binder and Malware (Part 3)
Binder and Malware (Part 3)