Why ISPs Hope You Don't Know Why DNS Encryption Protocols Are Different
While we use easy-to-remember web addresses, the Internet actually runs on a system of IP addresses and remote servers. Behind the scenes, it relies on the Domain Name System (DNS), which translates those domain names into IP addresses—a format your device can understand.
The good news is that you can encrypt those DNS requests to prevent prying eyes from seeing the sites and services you use. The bad news is that it's not as simple as flipping a switch and protecting all your DNS requests. While some methods protect you from your ISP, others still expose metadata and usage patterns that make it easy to find out who you are and where you are. This is why it's important to understand the differences between DNS encryption methods! If you think encryption equals privacy, your data will end up in the wrong hands.
Internet Service Providers (ISPs) and the DNS Protocol
ISPs care about the DNS protocol you use
DNS traffic is the easiest way for your ISP to identify the website you visit. When you type a domain name into your browser, even if you are protected by HTTPS , the next DNS request can show you the website you are trying to access. It may not show the specific pages on the site you are visiting, but it will generally show you the domain you are visiting. ISPs can use this visibility for network management purposes. It can also be a source of revenue; the Federal Trade Commission has reported that ISPs inject ads and make money from DNS query data.
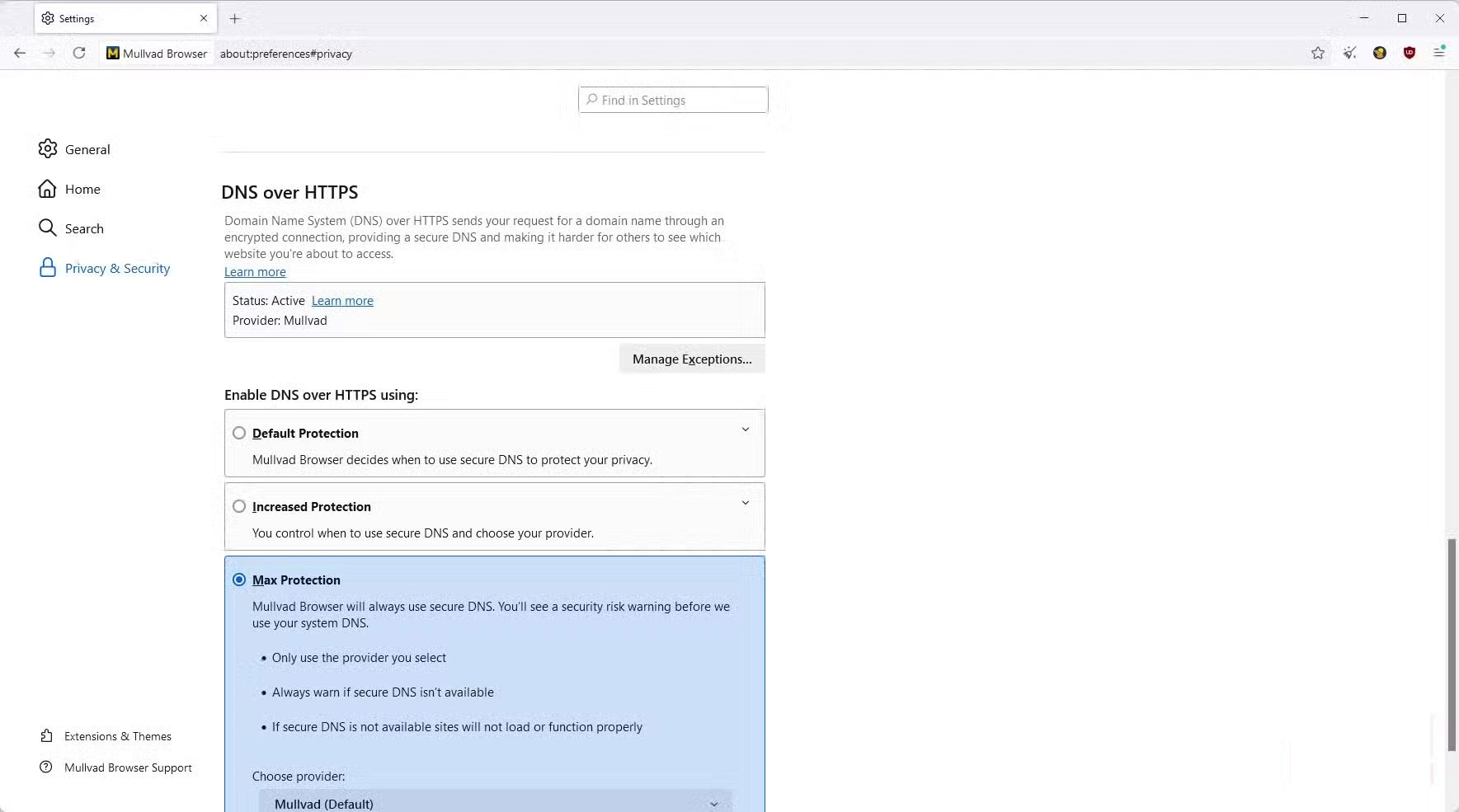
It would be harder for ISPs to continue this business model if your DNS queries were encrypted. You can use protocols like DNS over HTTPS (DoH) and DNS over TLS (DoT) to make it difficult for ISPs and anyone not on the network to see the domain names you look up. This completely eliminates the traditional revenue stream for ISPs, while also providing you with privacy benefits, although it does shift trust to a third party to resolve DoH/DoT (e.g., Cloudflare, Google ).
Main protocols
DoH, DoT vs ODoH
DNS encryption isn't always a unified standard. This means that each DNS encryption protocol can take slightly different approaches to solving the problem. DNS over HTTPS (DoH) and DNS over TLS (DoT) are popular and widely deployed encryption protocols. Both protocols aim to encrypt DNS queries so that they can't be read in plain text, but their design and implementation results in each protocol providing a different user experience.
DoH blends seamlessly into all your traffic because it runs over HTTPS. Popular browsers like Google Chrome and Mozilla Firefox can easily enable it directly, and networks can't easily block this traffic without disrupting everything. DoT is quite different. It's usually implemented at the system or router level and runs on a dedicated port (853) using TCP with TLS encryption. It's more of a network-level service, but it can be more easily blocked by a firewall or ISP if needed.
Note : DNSCrypt is another lesser-known option that provides strong authentication and encryption, predating DoH and DoT. It is not standardized by the IETF but is actively maintained through proxy implementations that can support newer protocols like ODoH.
All of these protocols offer some form of protection, but choosing one or the other ultimately means choosing between ease of deployment, where you can trust, and censorship resistance.
The intermediary problem
Encryption can still expose you
Encrypted DNS doesn't make you completely invisible online. Different protocols can make it difficult for anyone outside the network to read your queries, but the resolver can still see the domain name you visited and your IP address. So you're trading off visibility from your ISP for visibility on a large public resolver.
Your traffic patterns can also leak metadata. Even if the data content is encrypted, factors like timing, frequency, and packet size can still be analyzed to infer browsing habits. In some cases, this traffic can be used to suggest domains you visit without decrypting the requests.
Additionally, the limited number of providers raises the issue of centralization, especially since the majority of encrypted DNS traffic is routed through these limited options. While these companies build strong protections, a single subpoena, data breach, or regulatory policy could expose user activity.