SQL Injection is one of the types of web hacking by injecting SQL query / command codes into input before transferring to the web application, you can login without a username and
DNS is an abbreviated Domain Name System for Domain Name Servers. Currently, in addition to DNS Google is chosen by many people, and many different DNS services also stabilize and

Keylogger can be a software or a small hardware device used to capture and collect information about keystrokes typed on the keyboard.

SCAM is an English term, meaning scam. By definition, SCAM is used to describe any business or individual who makes money or other bargains from victims without suspicion. In the

Many users do not have the habit of setting passwords for their computers, especially when working in the office. However, this also causes some problems because strangers can

CyRadar Internet Security Check Tool is a tool to assess your computer's ability to prevent network attacks, completely free of charge.

Some of the best security practices have appeared with the development of multicloud environments and there are several important steps that all organizations should take when they

The problem of anonymity and evading the control of the authorities on the Internet has been known for a long time. Many virtual tools and networks are designed to serve this

QR code is a matrix code (or two-dimensional barcode) developed by the company Denso Wave (Japan) in 1994. The word QR comes from Quick Response, in English means quick response,

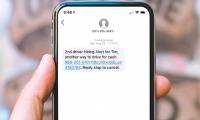
Smishing, a Phishing form, is when someone tries to trick you into giving them private information via text messages or SMS messages. Smishing is becoming a new and increasingly

However, not all cookies are the same. In fact, there are many different types of cookies. Some types are good cookies, others are bad cookies. Let's take a closer look through

NetFlow is a protocol developed by Cisco used to gather information about traffic through devices on the network.

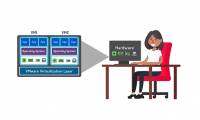
Virtualization offers a lot of great benefits such as cost savings, improved performance, reduced workloads and increased business performance. This is why it is an integral part

The growing popularity of VPN technology has led to a series of scams in a variety of ways, different ways and levels of daring.

Hackers can use Sniffer to eavesdrop on unencrypted data and see the information exchanged between the two. To better understand Packet Sniffer, as well as Packet Sniffer's

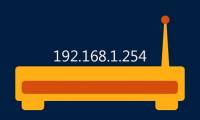
IP address 192.168.1.254 is the default Private IP address for some home broadband routers and modems.

Every device connected to the internet has an IP address or Internet Protocol address. There are 2 types of Public and Private IP addresses. The 192.168.0.1 IP address is a

In the following article, we will explore and discuss some more details about KeePass application - a popular password management tool today.

AxCrypt is file and folder encryption software, securing important data especially when sharing computers with many people.

Wireshark, also known as Ethereal, this tool is probably not so strange to most of our users, which is considered one of the network data analysis applications, with monitoring and
 SQL Injection is one of the types of web hacking by injecting SQL query / command codes into input before transferring to the web application, you can login without a username and
SQL Injection is one of the types of web hacking by injecting SQL query / command codes into input before transferring to the web application, you can login without a username and DNS is an abbreviated Domain Name System for Domain Name Servers. Currently, in addition to DNS Google is chosen by many people, and many different DNS services also stabilize and
DNS is an abbreviated Domain Name System for Domain Name Servers. Currently, in addition to DNS Google is chosen by many people, and many different DNS services also stabilize and Keylogger can be a software or a small hardware device used to capture and collect information about keystrokes typed on the keyboard.
Keylogger can be a software or a small hardware device used to capture and collect information about keystrokes typed on the keyboard. SCAM is an English term, meaning scam. By definition, SCAM is used to describe any business or individual who makes money or other bargains from victims without suspicion. In the
SCAM is an English term, meaning scam. By definition, SCAM is used to describe any business or individual who makes money or other bargains from victims without suspicion. In the Many users do not have the habit of setting passwords for their computers, especially when working in the office. However, this also causes some problems because strangers can
Many users do not have the habit of setting passwords for their computers, especially when working in the office. However, this also causes some problems because strangers can CyRadar Internet Security Check Tool is a tool to assess your computer's ability to prevent network attacks, completely free of charge.
CyRadar Internet Security Check Tool is a tool to assess your computer's ability to prevent network attacks, completely free of charge. Some of the best security practices have appeared with the development of multicloud environments and there are several important steps that all organizations should take when they
Some of the best security practices have appeared with the development of multicloud environments and there are several important steps that all organizations should take when they The problem of anonymity and evading the control of the authorities on the Internet has been known for a long time. Many virtual tools and networks are designed to serve this
The problem of anonymity and evading the control of the authorities on the Internet has been known for a long time. Many virtual tools and networks are designed to serve this QR code is a matrix code (or two-dimensional barcode) developed by the company Denso Wave (Japan) in 1994. The word QR comes from Quick Response, in English means quick response,
QR code is a matrix code (or two-dimensional barcode) developed by the company Denso Wave (Japan) in 1994. The word QR comes from Quick Response, in English means quick response, Smishing, a Phishing form, is when someone tries to trick you into giving them private information via text messages or SMS messages. Smishing is becoming a new and increasingly
Smishing, a Phishing form, is when someone tries to trick you into giving them private information via text messages or SMS messages. Smishing is becoming a new and increasingly However, not all cookies are the same. In fact, there are many different types of cookies. Some types are good cookies, others are bad cookies. Let's take a closer look through
However, not all cookies are the same. In fact, there are many different types of cookies. Some types are good cookies, others are bad cookies. Let's take a closer look through NetFlow is a protocol developed by Cisco used to gather information about traffic through devices on the network.
NetFlow is a protocol developed by Cisco used to gather information about traffic through devices on the network. Virtualization offers a lot of great benefits such as cost savings, improved performance, reduced workloads and increased business performance. This is why it is an integral part
Virtualization offers a lot of great benefits such as cost savings, improved performance, reduced workloads and increased business performance. This is why it is an integral part The growing popularity of VPN technology has led to a series of scams in a variety of ways, different ways and levels of daring.
The growing popularity of VPN technology has led to a series of scams in a variety of ways, different ways and levels of daring. Hackers can use Sniffer to eavesdrop on unencrypted data and see the information exchanged between the two. To better understand Packet Sniffer, as well as Packet Sniffer's
Hackers can use Sniffer to eavesdrop on unencrypted data and see the information exchanged between the two. To better understand Packet Sniffer, as well as Packet Sniffer's IP address 192.168.1.254 is the default Private IP address for some home broadband routers and modems.
IP address 192.168.1.254 is the default Private IP address for some home broadband routers and modems. Every device connected to the internet has an IP address or Internet Protocol address. There are 2 types of Public and Private IP addresses. The 192.168.0.1 IP address is a
Every device connected to the internet has an IP address or Internet Protocol address. There are 2 types of Public and Private IP addresses. The 192.168.0.1 IP address is a In the following article, we will explore and discuss some more details about KeePass application - a popular password management tool today.
In the following article, we will explore and discuss some more details about KeePass application - a popular password management tool today. AxCrypt is file and folder encryption software, securing important data especially when sharing computers with many people.
AxCrypt is file and folder encryption software, securing important data especially when sharing computers with many people. Wireshark, also known as Ethereal, this tool is probably not so strange to most of our users, which is considered one of the network data analysis applications, with monitoring and
Wireshark, also known as Ethereal, this tool is probably not so strange to most of our users, which is considered one of the network data analysis applications, with monitoring and