
7 basic questions about firewalls everyone needs to know
besides the anti-virus software and communication ports in the system, you also need to pay attention to another important factor in a security system, firewall - firewall.

besides the anti-virus software and communication ports in the system, you also need to pay attention to another important factor in a security system, firewall - firewall.
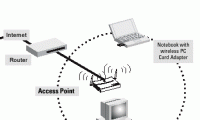
in the next part of this series, i will show you some of the security mechanisms available in wireless hardware.

in the next part of this article series, i will show you some of the wireless network security options in windows server 2008 operating system.

in this next article, i will show you how to deploy policy servers and how to enroll certificates and register active directory for that server.

in this series, i will show you some wi-fi network security techniques. the first part in this series will help you understand the vulnerabilities associated with wireless

in part 2 of this series, we will continue the discussion about wireless network traffic security by examining rumors surrounding the use of passwords.

in this article, i will show you the pros and cons of promoting ssid and mac address filtering.

the problem of anonymity and evading the control of the authorities on the internet has been known for a long time. many virtual tools and networks are designed to serve this
hackers can use sniffer to eavesdrop on unencrypted data and see the information exchanged between the two. to better understand packet sniffer, as well as packet sniffer's
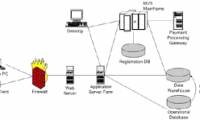
netcap is a command line utility that checks network traffic, which we will show you in this article.