Information about Gpcode.ak virus
Detection date: July 4, 2008
Danger: virus
Specifications
This Gpcode.ak malicious program will encrypt the files on the infected computer. This is a Windows PE EXE file with size 8030 bytes.
How it works
When launched, this virus will create the following mutex in memory to mark its presence in the system: _G_P_C_. (Mutex is a programming flag still used to retrieve and issue an object).
Then it will start scanning all logical disks to encrypt files in it. Encrypting all user files with extensions is listed in the following table:
abk
abd
acad
arh
arj
ace
arx
asm
bz
bz2
bak
bcb
c
cc
cdb
cdw
cdr
cer
cgi
chm
cnt
cpp
css
csv
db
db1
db2
db3
db4
dba
dbb
dbc
dbd
dbe
dbf
dbt
dbm
dbo
dbq
dbx
Djvu
doc
dok
dpr
dwg
dxf
ebd
eml
eni
ert
fax
flb
frm
frt
frx
frg
gtd
gz
gzip
gfa
gfr
gfd
hour
inc
igs
iges
jar
jad
Java
jpg
jpeg
Jfif
jpe
js
jsp
hpp
htm
html
key
kwm
Ldif
lst
lsp
lzh
lzw
ldr
man
mdb
mht
mmf
mns
mnb
mnu
mo
msb
msg
mxl
old
p12
pak
pas
pem
pfx
php
php3
php4
pl
prf
pgp
prx
pst
pw
pwa
pwl
pwm
pm3
pm4
pm5
pm6
rar
rmr
rnd
rtf
Safe
sar
sig
sql
tar
tbb
tbk
tdf
tgz
txt
uue
vb
vcf
wab
xls
xml
This virus uses Microsoft Enhanced Cryptographic Provider v1.0 (included in Windows) to encrypt files. Files are encrypted using RC4 algorithm. The encryption key is then encrypted using an RSA public key with a 1024-bit length in the body of the virus.
RSA encryption algorithm divides the encryption keys into two types public and private. Only public keys are needed to encrypt messages. An encrypted message can only be decrypted with the private key.
The virus will create an encrypted copy for each original file. The encrypted copy will retain the original file name with the _CRYPT section added to the end of the file name. For example:
WaterLilles.jpg —file original
WaterLilles.jpg._CRYPT —file encrypted
The original file will then be deleted.
The virus leaves a file named "! _READ_ME _ !. txt" in each folder containing encrypted files. This file contains the following:
Your files are encrypted with RSA-1024 algorithm.
Để phục hồi tập tin bạn cần phải làm việc our decryptor.
To buy decrypting tool contact us at: [censored] @ yahoo.com
=== BEGIN ===
[key]
=== END ===
Files located in the Program Files folder and the following files will not be encrypted:
There are "system" and "hidden" properties;
Less than 10 bytes
Greater than 734003200 bytes
Once the virus has been activated, it will create a VBS file to delete the main body of the virus itself in the victim computer and create a MessageBox shown below on the screen:
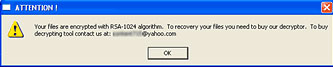
The virus does not register itself in the system registry.
Instructions to overcome
File recovery
At this point, it is not possible to decrypt files encrypted by Gpcode. However, you can still use PhotoRec to recover the original files deleted by Gpcode after the virus has created an encrypted version of the files.
This utility is used to recover Microsoft Office documents, executable files, PDF and TXT documents, . This is a list of supported file formats.
PhotoRec is part of TestDisk. The latest version of TestDisk, like PhotoRec, can be found here.
Below are detailed instructions on how to recover deleted files with PhotoRec:
- Use another clean computer to download TestDisk, including PhotoRec.
- Save PhotoRec to an external drive and connect this drive to the infected computer (Gpcode.ak cannot infect and delete itself after launching).
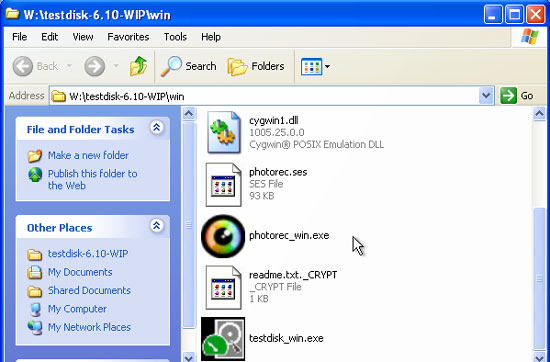
- Run PhotoRec ( photorec_win.exe file and located in the win folder of TestDisk):
- Select the target drive for PhotoRec to search for files and press ENTER to continue:
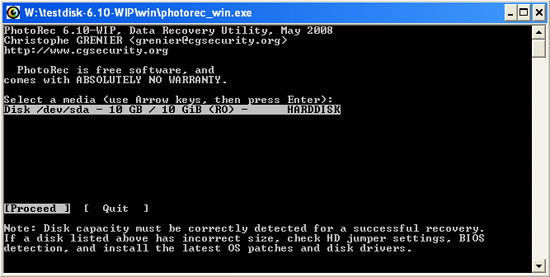
If you have multiple drives in the system, perform this step for each drive (ie when recovering files from a drive, you must repeat the same process for the next drive).
- Select the partition table type (typically 'Intel') and press ENTER to continue.
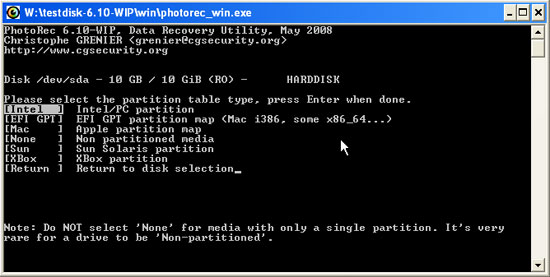
- Select the partition you want to restore files and press ENTER to continue.
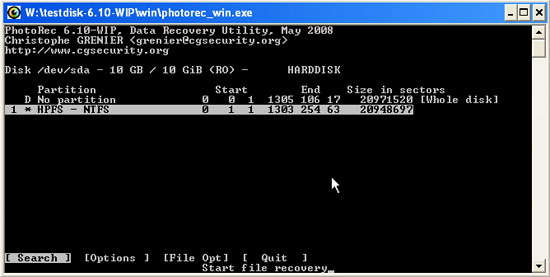
If the disk has several partitions, then you need to repeat this step for each partition.
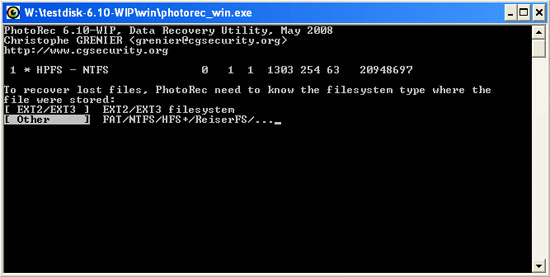
- Select the file system type (for Windows users should choose 'Other') and press ENTER to continue.
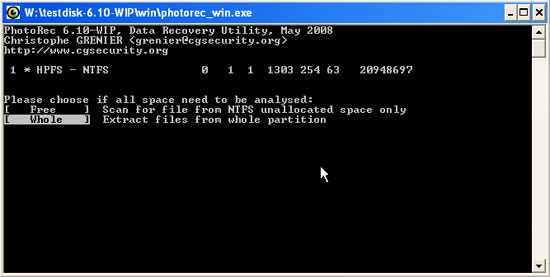
- Select the location to search for deleted files and press ENTER to continue. Select 'Whole' to search the entire drive to find deleted files.
- PhotoRec will ask you to specify a destination folder for restored files. Use PhotoRec's file browser to move the root directory (by selecting "." and pressing ENTER)
The root directory will show which drives the system has. Select the appropriate removable (or network) drive and the folder in which you want to save the restored files. Should choose an external drive, that is, do not select the drive on the infected device because the deleted files may be corrupted.
Before recovering files, create a separate folder on the drive (eg "recovered") and choose to save the restored files to this directory, to avoid errors that occur after recovery. When you have selected the folder, press "Y".
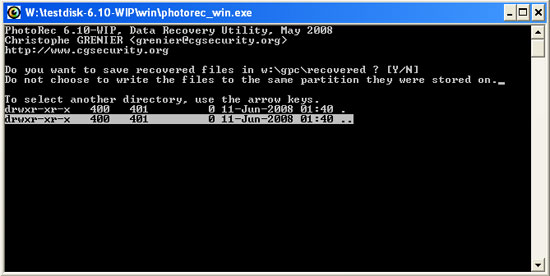
When you press "Y", you will see a file recovery process appear. This process takes a little time to implement.
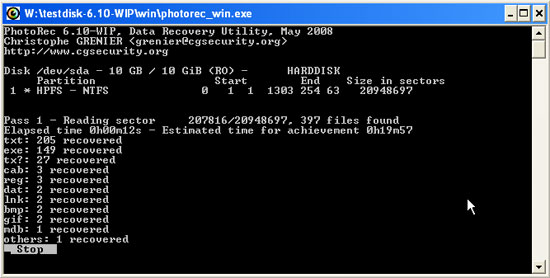
Please wait for the process to finish before proceeding to the next step.
- The recovered files are now in your external drive. When you open the folder containing the restored files, you will see the file name does not correspond to the original file name in the old hard drive.
Your file names will look like the following:
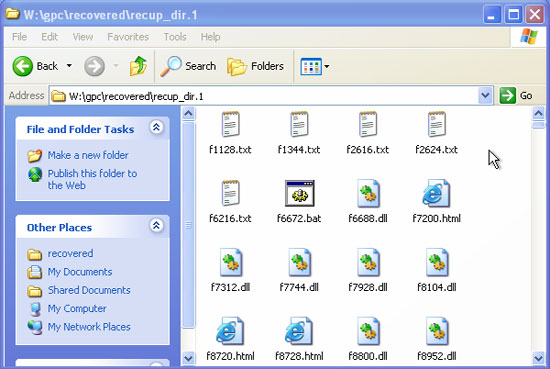
This is because of PhotoRec's way of working, you should not be alarmed when you encounter this situation. In addition, although the utility can recover the contents of the files, it still cannot establish their original location.
To complete the recovery process, we create a free utility called StopGpcode to classify and rename the restored files.
- On another computer, download the Stopgpcode utility and copy it to the USB drive.
- Plug this USB drive into the infected computer and load the Windows Command Prompt by going to START | PROGRAMS | ACCESSORIES .
- Select the USB drive by typing that drive letter, for example, W: for example.
- Then run the utility from the command line by typing the following command:
STOPGPCODE -r -i -o
eg: STOPGPCODE -r W: RECOVERED -i С: -o W: SORTED
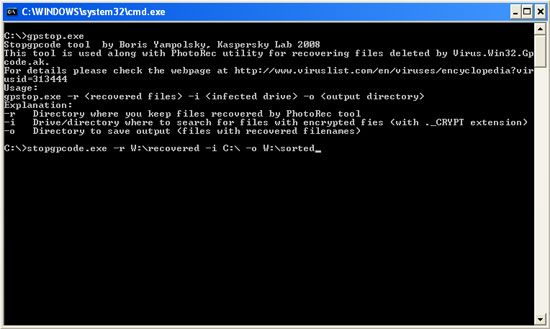
The utility will process the entire disk and compare the size of the encrypted and restored files. The program will use the file size to detect the original location and the name of the restored file.
The utility will detect the correct name and location of each file, recreate the root directory and file names within the directory. If the utility cannot specify the original file name, the file will be saved to a folder named "conflicted".
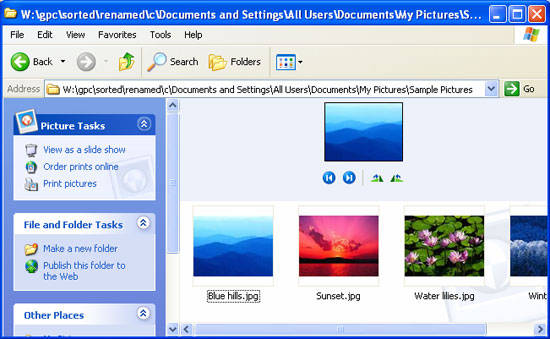
You can download Stopgpcode here.
Decrypt files with StopGpcode2
Some files encrypted by Gpcode.ak can be decrypted without using the RSA private key. They can be decoded by the steps below:
- Find all encrypted files with the ._CRYPT extension from the victim computer and copy them to a removable storage device in a folder named encrypted .
- Follow the commands in 'Restoring Files' and save the restored file with the correct restored names to the removable drive in the folder named 'backup'.
- Match unencrypted copies of files with encrypted versions in the 'encrypted' folder. You can find unencrypted versions of files in your backup. If you lose the image, you may have a copy left on the camera's memory card. Often you can get copies for encrypted files on network resources. There are files you need to search and copy to the folder named 'backup'.
Note: You must ensure that files saved to the backup folder must have a different name in the 'encrypted' folder - everything needs to be distinguished except the extension ._CRYPT.
- Create a folder named 'decrypted' where you will save the decrypted file. Download the Stopgpcode2 tool that can help you decrypt these files.
-
Launch StopGpcode2 from the command prompt ( Start > Run > cmd.exe ) - make sure the full path for the folders 'encrypted', 'backup' and 'decrypted'. For example, if the tool and the directories are in the root directory of drive E: then you need to execute the following:
e: stopgpcode2.exe e: encrypted e: backup e: decrypted
When the program executes, you will see the tool start decrypting your files.
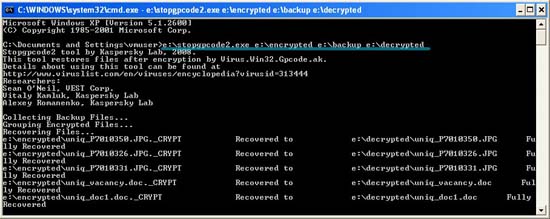
- After completing the decryption, it will display a message that has completed 'Done'. You can now open the 'decrypted' folder and check which files the tool can decrypt.
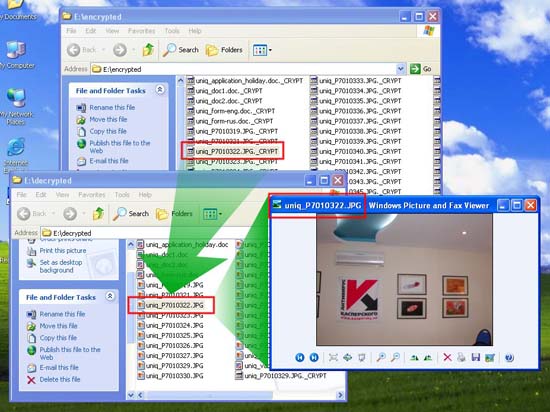
L prefers: The tool may not be able to decrypt all files. In this case, it will notify you of the problem.
In addition, you should not test the tool on a virtual machine. The results obtained on the virtual machine will be much different than on real machines.