WinRAR remains one of the biggest security risks on Windows.
To this day, there remains an ancient Windows program that causes security problems. That's right; despite being over 30 years old, WinRAR still surfaces multiple times each year with security vulnerabilities, making it notorious for unfortunate reasons.
WinRAR is being actively exploited.
Late on December 9, 2025, CISA quietly released a press release adding "two known vulnerabilities being exploited" to its list of known vulnerabilities, detailing the software being actively exploited.
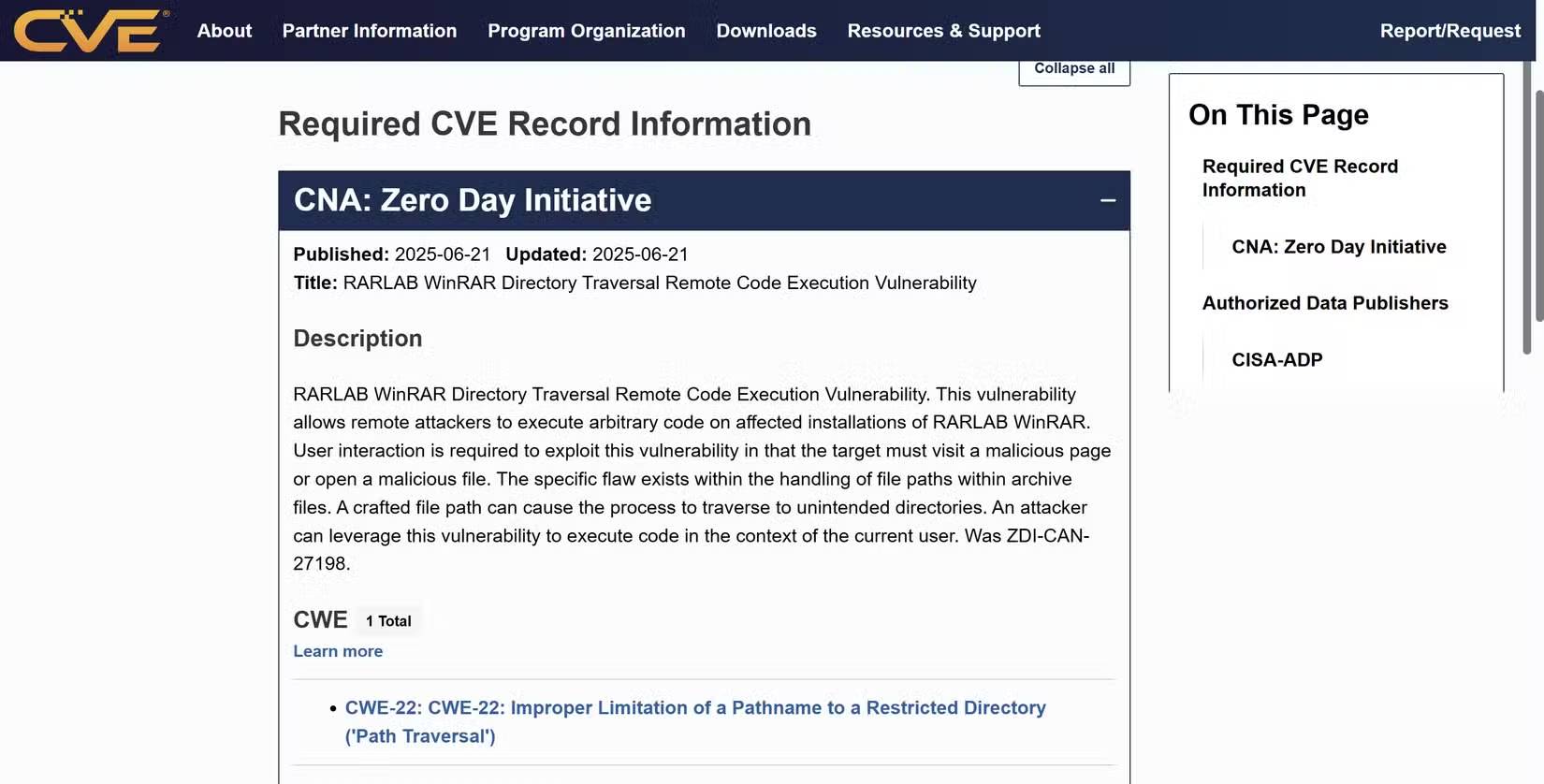
This time, WinRAR is being exploited by a remote code execution vulnerability via folder browsing. Essentially, an attacker exploiting this vulnerability can remotely execute code on a computer with WinRAR installed when the user interacts with a malicious page or file. This vulnerability, tracked with the code CVE-2025-6218, could allow an attacker to place dangerous files throughout the operating system, install malware, etc.
However, to be fair to WinRAR, things aren't entirely as they seem. Although this vulnerability is being actively exploited, WinRAR's developers, RARLAB, patched it in June 2025. The problem is that not enough users are installing the latest version of the application, creating a security issue that could easily be resolved.
To date, security researchers have seen CVE-2025-6218 exploited multiple times. Hacker News has found reports from numerous security companies, including BI.ZONE, Foresiet, SecPod, and Synaptic Security, indicating that this specific vulnerability is being exploited by at least two, if not more, threat actors.
You've probably heard about other major security vulnerabilities in WinRAR.
If that's the case, why do people still install it?

WinRAR was first launched as a graphical user interface (GUI) in 1995. In fact, WinRAR is a pretty good compression software and for a long time, it was one of the most popular Windows tools for any installation, especially since Windows didn't originally support the RAR format .
But over the years, WinRAR has developed some serious security vulnerabilities, making it a laughing stock to anyone familiar with Windows and security (plus its notorious perpetual trial version – a fertile ground for attackers to exploit).
For example, in 2018, a 20-year-old source code vulnerability was discovered in WinRAR that allowed attackers to create archive files that extracted files outside the intended directory. This vulnerability exploited an extremely outdated and vulnerable 20-year-old DLL designed to handle a specific file type (ACE files) that shouldn't have been used, enabling millions of attacks. Instead of patching the DLL, WinRAR completely removed support for ACE files, but the damage was already done. With so many people using outdated versions of WinRAR, this vulnerability remained active for years.
File parsing is often the root cause of problems in WinRAR, similar to the ACE vulnerability. Over the years, numerous vulnerabilities believed to be related to WinRAR's file handling have emerged concerning ZIP, RAR, TAR, CAB, and LZH files, allowing buffer overflows, directory browsing, remote code execution, etc.
Why always WinRAR?
A program can't always have every problem, right?
The ACE vulnerability highlights one of WinRAR's biggest problems: outdated source code. According to reports, the development team was unable to patch the bug because they had to deal with outdated source code, so removing the feature entirely was easier.
That outdated source code is partly to blame for WinRAR's problems. It still supports older and less common archive formats, some of which are practically obsolete. This old parsing code—much of it written decades ago—creates vulnerabilities that modern, minimalist archiving software doesn't have.
Each type of storage requires custom code, and each parser becomes a potential vulnerability.
Then you have those users who still use WinRAR. Most users install WinRAR simply because it's something they do regularly, without considering whether they'll actually use it, given that better archiving tools are available and Windows now integrates many of the most popular formats.
Outdated software is often exploited as it becomes vulnerable over time, and the combination of old source code, outdated technology support, and a lack of updates makes WinRAR a particularly attractive target.
It's time you ditched WinRAR!
At least update it.
If you're still using WinZIP, why?
Every format you could use with it is either supported by a better tool or has simply been discontinued and replaced by more modern tools.
Furthermore, modern alternatives like PeaZip are faster, safer, and free to use, even without an unlimited free trial.
Furthermore, you don't need WinRAR to create or open RAR files. All modern archiving and compression tools can do that, and there are no serious security vulnerabilities.