
2007: Super sophisticated Trojan will be raging
the extremely sophisticated technique that this trojan uses will become popular in 2007, a security expert warns. named 'rustock', the later trojan family first appeared nearly a

the extremely sophisticated technique that this trojan uses will become popular in 2007, a security expert warns. named 'rustock', the later trojan family first appeared nearly a

security researchers have discovered a new type of trojan keylogger that captures not only keyboard operations but also mouse operations.
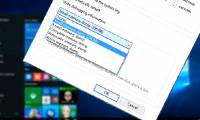
when trying to open any * .dmp file created by windows debugging tools, you will find the language used in it extremely strange. sometimes you are curious to know exactly what

the design has a movable joint that makes the phone slide and fold less durable than a bar phone. but this does not mean that simple bar phones are hard to break down. typically,

the following general article can be very helpful for those who download movies online, giving a better view of the versions of telesync, cam, screener, ..

in the next article of the tutorial series on photoshop, we will present some basic steps to create the effect of out-of-bound photos.