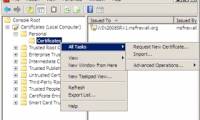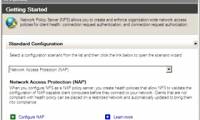
Deploying IPsec Server and Domain Isolation with Windows Server 2008 Group Policy - Part 4
in this article we will show you how to test clients and how security certificates are assigned, removed automatically as well as how clients are connected or ...