Learn about digital content management (DRM)
The digital revolution has empowered consumers to use digital content in their own new and creative ways, but also makes copyright owners nearly unable to control the assets. Their gray matter is being distributed rampant, illegally, or in other words, their copyright is being seriously compromised.The gray matter is not only music, but also movies, video games and any other media that can be digitized and transmitted in many different forms (primarily through sharing Unauthorized on the Internet).
What is DRM?

DRM (Digital rights management) - Digital content management is a series of access control technologies to limit infringement of copyrighted digital content.In a more intelligible way, DRM was born to control what users can do with digital content.In this article, we will find out what DRM is, how copyright owners are implementing this concept, and what needs to be done in the future to better control digital content. .
In general, digital content management is an extensive term related to all programs designed to control access to copyrighted materials by means of technology.In essence, DRM replaces the ability to control inherently passive and ineffective copyrights from the owner of digital content and puts that digital content under the control of a computer program. count.Applications and digital content management methods are endless, here are just a few examples of digital content copyright management for your reference and a more general look:
- A company puts its servers to prevent the forwarding of sensitive employees' emails.
- The e-book library server restricts the right to access, copy and print user documents based on constraints set by the copyright holder of the content.
- A movie studio attaches a software to a DVD to prevent users from making copies of a second copy from that DVD.
- A music maker releases titles on a type of CD, accompanied by bits of information aimed at tampering with extracting software.
Although there are many opinions that DRM methods are sometimes too strict, especially those used in the film and music industry, implementing digital content copyright management is also a The problem should be done to direct consumers to more civilized use of copyright.The distribution of digital content over the Internet through the file sharing network has made traditional copyright laws obsolete in actual operation.For example, every time someone downloads an MP3 file of a copyrighted song from a free file-sharing network instead of buying a CD, the copyrighted music label and the artist who created the song did not receive it. Any amount that should have been received. In the case of the film industry, several studies have estimated the loss of revenue from illegal distribution of DVD content that falls into about 5 billion dollars a year.The nature of sharing information on the Internet makes it impractical to sue individuals for violating the law in this way, so companies are trying to regain control of their copyright distribution by making Consumers cannot make unauthorized copying or sharing of digital content.
The problem is that once you have purchased a DVD, which means that the product belongs to you, you will have full legal rights to make a copy of it for your own use. .This is the main idea of fair use licensing in copyright law, while there are specific cases that deny copyright protection in favor of content users, including stars Copy protected documents for personal use and copy any content in the public domain. Most digital content management programs cannot consider all fair use cases carefully because computer programs will not be able to make subjective decisions.Before we continue to debate DRM, take a step back and find out what DRM requires from a programming standpoint.
Structure of DRM
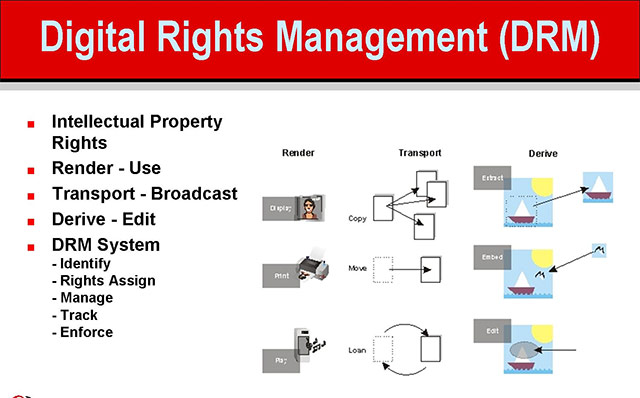
An ideal DRM system is to ensure flexibility, complete transparency for users and complex barriers to prevent unauthorized use of copyright.First-generation DRM software is almost exclusively looking to control piracy.While second-generation DRM programs focus on finding ways to control viewing, copying, printing, changing and everything else users can do for a digital content. .
A digital content management program will work on three levels:
- Set copyright for a piece of content.
- Manage the distribution of such copyrighted content
- Control what consumers can do with that content after being distributed.
In order to achieve these levels of control, a DRM program must effectively identify and describe three entities, including users, content and usage rights, as well as the relationship between these three entities.
Take an example of a simple DRM software for a website that supports downloading MP3 files.You log in to the website you have registered to download a song that you love, such as the song 'Cat Bui' by the late musician Trinh Cong Son.Your subscription level allows you to download five songs each month.In this case, the entities that DRM needs to manage will include users and content of 'Sand Dust' by Trinh Cong Son.Identifying users and content are quite simple tasks.You already have your own customer ID number and each MP3 file on the site can also have a specific product number linked, the more difficult part is to identify the rights, ie the way in which you okay and not allowed to do anything with that content.Can you download that file?or have you downloaded five MP3 files limited in the month?Can you copy the file or download the encrypted and locked file, respectively?Can you extract a piece of the song for use in your own audio mixing software?Usage rights include not only rights and constraints, but also any obligations relating to that transaction.For example: Do you need to pay extra for this download?Will you get any privileges when downloading this song?
All of these will be included in the relationship between you, the song and the related rights.
DRM technology
Still following the example above, suppose you've only downloaded three files for this month, so this download is still within the five-song limit a month that you've been granted registration, and assuming You have received additional promotional discounts of 20,000 credits for the next month if you download this 'Sand Dust', then you can copy files under fair use .Suppose a copyright owner refuses to grant anyone permission to extract their digital content.The DRM structure for the MP3 file you down may look like the following:
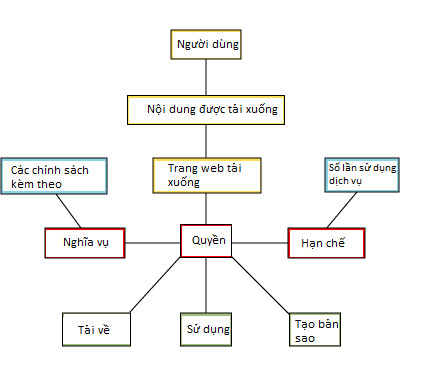
Please note that although user status remains the same each time you log in to the site, the relationship between users, content and rights may change.The structure of DRMs must be able to adapt to changing conditions.If you upgrade your subscription to an unlimited download level instead of just five downloads per month, DRM software will also have to adjust to that new relationship.DRM structure must be attached to the technology of the website so that it can adjust relationships quickly.This is one of the reasons why seamless DRM settings will be difficult to implement, because without specific standards, digital content management software will not be easily linked to commercial tools. e-commerce is available on the page.However, controlling data downloaded from a website is not too complicated, the more difficult part is how to control what users do with digital content when it belongs. their own.How will the website enforce your use of the newly downloaded MP3 file?How do they know you won't create a new copy of that MP3 file?This is when DRM works.If in the case of a large media company trying to prevent people from copying electronic documents, this is not difficult.
Companies like ContentGuard, Digimarc, InterTrust and Macrovision are businesses that specialize in providing automated DRM solutions, including everything you need to set up your own DRM structure, tailored to specific situations. .
For example, ContentGuard's complete DRM toolkit allows copyright owners to create and enforce licenses for their digital products and services, including all types of digital data, from movies to downloaded software.The RightsExpress software uses the MPEG Express expression language and guides the copyright holder through the process of identifying a piece of content, identifying the user and determining the right to use.From there, the copyright owner can set the access level and encryption mode for each specific content, creating a custom interface that allows users to get content based on those settings, developing a real model. User identity verification exam and user usage tracking of that content.
DRM protection ring
Continuing with the above example, you still have 2 times to download the song 'Sand dust', the computer simply understands that.But the computer will not understand that you copied it to your MP3 player and laptop, or that you use a new desktop computer and you need to create another copy.
Many companies have taken measures in 'desperation' to try to limit digital content from spreading illegally over the Internet, as well as eliminate some of the rights consumers can take. with the content they bought.
A typical DRM encryption program usually provides an encryption key that works permanently.In this case, the keys must be associated with the user's machine ID number.The key will only decrypt the file when it is accessed from the computer it originally was on.If not, the user can simply forward the key along with the encrypted software for all the people he knows.
Some products, such as those protected by Macrovision SafeCast or Microsoft Product Activation, use a web-based licensing policy to prevent unauthorized use of content.When the user installs the software, his computer will contact the server, then verify the license and receive the rights (access key) to install and run the program.If the user's computer is the first case that requires permission to install this particular software, the server will return the appropriate key.If the user shares the software with their friends and the friend tries to install the software, the server will deny access.In this DRM model, users often have to contact the content provider to be allowed to install software on another machine.
A DRM method is less common than digital watermark.The FCC is trying to request a "broadcast flag" that allows a digital video recorder to identify whether it is allowed to record the program.Flag is a piece of code sent with a digital video signal.If the broadcast flag indicates that the protected program, DVR or DVD recorder will not be able to record the program.This DRM model is one of the rather complex protection models, because it requires both means and devices that can read the broadcast flag.This is when Philips video content protection system (VCPS) appears.VCPS technology helps read the FCC broadcast flag and determines if the device can record the program.An unprotected disc can be played on any DVD player, but if the disc has a broadcast flag, it will only be able to record and play on the VCPS integrated player.
DRM vendor Macrovision has used an interesting approach in products that help protect their recent DVDs.Instead of making a DVD impossible to copy, Macrovision RipGuard will exploit errors in DVD copying software to prevent it from copying itself.It is a piece of code in software on a DVD, and its purpose is to confuse another code called DeCSS.DeCSS is a small program that allows software to read and extract encrypted DVDs.Macrovision developers studied DeCSS to discover its vulnerabilities and then built RipGuard to enable those vulnerabilities and disable copy functionality.However, DVD users have also found many ways to 'rip' RipGuard, mainly by using ripping software that does not use DeCSS or by tweaking the code in the data extraction process based on DeCSS.The 1998 Digital Copyright Act disabled an illegal DRM system in the United States, but many people still actively seek and publish methods to overcome DRM's security restrictions.
Controversy about DRM
Recent unseen DRM models have established an antagonistic relationship between digital content providers and digital content users.Over the years, a number of controversies regarding DRM technology have emerged.
For example, in 2005, Sony BMG distributed CDs that led to litigation and numerous media issues.The problem stems from the conflicts between the two software on the CD: MediaMax of SunnComm and Extended Copy Protection of First4Internet (XCP).The incident raised questions regarding copyright owners being allowed to "go far" in protecting their content.
From the beginning, MediaMax software did not involve copyright protection but only tracked user activity.Whenever someone plays a CD on their computer, MediaMax will send a message to the SunnComm server, so Sony-BMG can find out who is listening to the CD and how often they listen to the CD.And the problem is that there are no clear signs or statements from the publisher about MediaMax activity, and worse, there is no easy way to uninstall this software.
However there is another bigger problem.First4Internet's Extended Copy Protection limits the number of copies a person can make from a CD is three.First, it runs in the background of the user so that users cannot detect it, and creates a hidden area (sometimes called a rootkit) in the Windows operating system, potentially causing a risk. security when the computer is infected with a virus.Computer viruses can hide indefinitely in Extended Copy Protection without being detected.Virus scanning software often cannot reach files in rootkits.In addition, Extended Copy Protection slows down the calculation process, and automatically connects to the Sony-BMG server to install copy protection updates.And there is no easy way to uninstall it.Some users had to reformat their hard drive to remove the files and negative effects that Extended Copy Protection caused.Finally, Sony had to recall millions of discs with DRM model integration, and had to agree to release tools to display hidden files.
However, after such incidents, DRM has not disappeared forever but continues to cause problems for businesses and consumers.For example, a computer game called Spore by Electronic Arts (EA) was released in 2008, along with what many players consider an DRM system to be excessive and difficult to disqualify. quit, that's SecuROM.SecuROM has excessively limited the rights of those who have purchased the game, such as only allowing Spore installation up to 3 times, after 3 times but still want to install more, players will have to contact EA and provide the company with information such as proof of game purchase, reasons for using over 3 installments and other related information.EA finally relaxed the DRM restrictions on the game, but they still faced some fair use lawsuits shortly afterwards.
Apple and its customers are also concerned about downloading movies from iTunes - a company's download service.Apple released their personal Macbook notebooks, in October 2008, with little information regarding the applicable DRM models.In fact, these Macbooks have been installed with a high-bandwidth digital content protection system (HDCP).Due to the lack of awareness of this technology, many customers bought Macbooks and tried to play movies downloaded from iTunes on external monitors, but were not viewable at all.HDCP blocks any movies playing on analog devices to prevent the recording of content from copying software, but most customers who buy content only want to see it on a wider screen, and HDCP has Do not allow them to do so.
DRM standards

There is no universal standard for DRM.At this time, many digital entertainment companies are choosing raw methods, in which users cannot copy, print, change or transfer documents.The most concerning issue that DRM-related activists have to do is the fact that the current DRM trend is overcoming the protection measures prescribed under traditional copyright laws.For example, when you play a DVD, some DRM models will not allow you to skip the introduction, which has nothing to do with copyright protection.More disadvantaged than consumers are libraries and educational institutions that store and lend digital content, they may suffer a lot if DRM software has a limited level. High becomes the standard.The library will not be able to store a software with a time-limited encryption key and it is not possible to lend a device-specific license to view the content using its traditional lending model.
Arguments against digital content copyright management are based on issues such as user privacy, technological innovation and rational uses.As stated, under copyright law, fair use doctrine allows consumers the right to copy copyrighted content that they have acquired for their own purposes. Other theories such as first sale , which allows content buyers to resell or remove content he has purchased and limited term theory will limit the duration of copyright after a certain period of time.As we have seen in the case of Sony-BMG, the company secretly monitors consumer activity and hides files on the user's computer, which is infringing on the user's privacy.These can be considered as approaches of spyware applications rather than a legitimate copyright management model.DRM systems can also affect the ability to innovate technology because it limits the use and format of digital content.Third-party vendors will not be able to develop support products and utilities if the computer code in that software is protected indefinitely by DRM, and consumers will not be able to upgrade legally. their own hardware when it is protected by a DRM program.
According to Professor Ed Felten of Princeton University, DRM not only affects the freedom of technology development but also limits the freedom of speech.When Professor Felten tried to publish an article about a faulty DRM system in 2001, producers in the music industry threatened to sue him.Some companies argue that his research will encourage people to ignore DRM programs, and this is illegal in the United States.The Digital Millennium Copyright Act ( DCMA ) guarantees the protection of a DRM program regardless of whether it respects the fair use doctrine. The groups fighting for consumer rights in many countries are lobbying Congress to modify part of the DCMA law, because according to DCMA , trying to neutralize DRM or spleen is illegal. According to consumers' advocates, DCMA offers an improper advantage to copyright owners by not setting limits on the types of DRM programs they can use. In essence, DCMA encourages anti-competition and makes it increasingly difficult for consumers to easily enjoy the content they have bought.
In fact the digital content field is increasingly being consolidated today, perhaps we should wonder whether any DRM system can harmonize the interests of both copyright owners. and consumers or not.When DRM becomes a standard in the fields, the result will be what experts call "reliable computing".In this setting, DRM methods will ensure the protection of copyrighted content along each step, from content creation to uploading until the content is downloaded and used when it is in user hand.The computer will automatically know what users are allowed to do with a piece of content and will take appropriate actions.With the adoption of standards, consumers will at least benefit in part, because DRM-encoded media will be available on all devices.Hopefully in the future, publishers will be able to find the most optimal way, harmonizing the interests of copyright holders as they are, with the rights of consumers who are copyright users. !
- Authenticate what two factors are and why you should use it
- How does the Windows Product Activation (WPA) work?
- Learn about the process of licensing copyright on Windows
- Find out how fingerprint security technology works
You should read it
- ★ W3C ignores all criticisms and approves the EME standard for copyright content restrictions
- ★ Things to know when disputes about copyright claims on YouTube
- ★ This is how to check your Windows 10 is Win copyright or not?
- ★ Marilyn Monroe 'resurrected' in AI form, will human image copyright no longer exist after death?
- ★ YouTube launches a new anti-piracy tool, notifying authors if their content is stolen