
How to Create a Website Privacy Policy
a website privacy policy tells visitors to your site exactly what information you collect from them and what you do with it. they're also required by law in most countries and

a website privacy policy tells visitors to your site exactly what information you collect from them and what you do with it. they're also required by law in most countries and
discussed herein are ways through which a pc user can be able to utilize the group policy snap-in to develop or edit the lists of applications that load automatically when you log
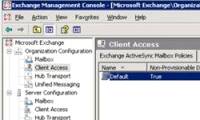
exchange server 2007 service pack 1 (sp1) contains advanced features around exchange activesync (eas). you will see throughout this article, a new exchange activesync policy

in this article, i will show you how to use ldp to determine which mailbox manager policy is being applied to a user's mailbox. i had to do this when i found that a wrong mailbox

although we are familiar with the concepts and terms related to microsoft's network access protection (nap) and cisco nac technologies, we still have to consider the new network

the main remote assistance scenario within a corporate network environment is the support of workstations in the corporate network and in a domain. the user's computer must be
in the previous part of this series, we showed you how to configure the vpn component used to allow external users to access our network. in this part 4, we will go

in the previous series of articles on this topic, we showed you how to configure a security policy so that windows checks whether the client is requesting access to the network
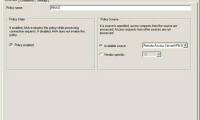
in the previous articles, i have shown you how to create an authentication policy for both the computer to be checked and without checking. in this article, we will continue the
in the first five years of a series of how to create a site-to-site vpn between the main office isa firewall and the branch office, we have focused on issues related to creating