PKI Tutorial - Part 1: Planning
Martin Kiaer
How you understand PKI, which stands for Public Key Infrastructure - public key infrastructure. In this 4-part series, I will give you a brief overview of how to design, install, and troubleshoot a PKI based on Microsoft Certificate Services in Windows Server 2003. We also introduce gives you some common pitfalls and best practices for building and executing a PKI, we will focus on the issues needed to properly and flexibly build PKI from the start.
Why PKI is needed?
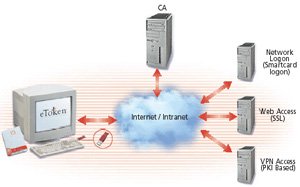 A few years back, most people talked about 2000 as the year of PKI. Many people believe that the mainstream of the market will eventually tend to use all the good aspects that PKI can provide. However, as you can guess, certificates and PKI have never really taken off. The simple thing is that it is not enough to draw attention to classification management and technical staff (who can see the value of PKI). However, after a while, PKI has become one of the hottest topics in large and medium businesses. The change in security, security and improvements in the Internet and when mobile communications technologies become a business enterprise, means that certificates and PKI are ready. For the mainstream of the business market like never before.
A few years back, most people talked about 2000 as the year of PKI. Many people believe that the mainstream of the market will eventually tend to use all the good aspects that PKI can provide. However, as you can guess, certificates and PKI have never really taken off. The simple thing is that it is not enough to draw attention to classification management and technical staff (who can see the value of PKI). However, after a while, PKI has become one of the hottest topics in large and medium businesses. The change in security, security and improvements in the Internet and when mobile communications technologies become a business enterprise, means that certificates and PKI are ready. For the mainstream of the business market like never before.
Therefore, the big PKI problem with you is why you need to care? Basically, that is the decline in certificate management. You can see that today certificates are everywhere and often they are used without knowing you have ever worried about their viability. One of the most common scenarios for which certificates are used is:
- Encrypt files and disks (certificates used to protect private keys)
- Multi-factor verification is like smart cards
- IPSec
- Digital signatures
- RADIUS and 802.1x authentication
- Wireless networks
- NAP (Network Access Control) and NAQ (Network Access Quarantine) for a principle
- Code signs and drivers
- SSL / TLS for HTTP-based traffic protection
As you can see, certificates are used in many different locations and its main purpose is to add security to your IT infrastructure and solutions. But if you look at the list above, you can imagine that this also means you have to manage a lot of certificates, the more or less the number depends on the features you want to use in the facility. infrastructure and how to decide how to supplement them. PKI is simply a central way of managing the release, renewing, revoking certificates and building your own trusted path. The certificates and PKI we will cover in this series are based on X.509 v3, which means that we can take advantage of some of the advantages of using certificates, and that will be see more in part two of this series.
Important :
The intention of this series will tell you quickly the overview of the most important areas, so you can easily get the PKI platform. However, building a PKI can be a big project and if you are an IT administrator interested in security, you may need to look deeper into the links we provide at At the end of each part of the lesson.
Planning for PKI
The author put the planning phase at the beginning of the lesson because the planning part is very important anyway and would like to show how to make a plan to get the best performance through a number of areas. You should focus. The most common mistake for companies when installing Microsoft Certificate Services (by setting up a PKI) is that they often ignore the plan, and as a result, cost a lot of resources and money. Finally, they realized that there might not be some important issues when entering the Add / Remove Windows Components menu in Windows 2000 or Windows 2003 servers and putting a check mark before Certificate Services components.
The aspects you should consider during the planning process or for the PKI are:
- Check if your security policy is ready to update PKI
- Create one or more certificate policies
- Create a statement in using the certificate
Let's look carefully at the sections below.
Check if the security policy is ready to update PKI
Brian Komar, author of the popular book ' Microsoft Windows Server 2003 PKI and Certificate Security ', has written numerous articles for Microsoft and has many presentations on various PKI topics that often state: ' PKI will make your organization's security policies in effect ', that's all he wants to say. Make sure that your company's security policy targets your company's IT and business strategy, then implement this strategy with security applications and services that will depend on the credentials. just. When a security policy needs to be approved by management or committee members (who are responsible for the company's business strategy), you will basically get a ray of light. Green to advance with PKI implementation. Are you lucky enough, in case your company does not have a centralized security policy, consider the following URL for templates for different security policies based on standards. ISO 17799.
The SANS Security Policy Project
RFC 2196, 'Site Security Handbook'
Open Directory Project - Security policy samples
Create one or more certificate policies
Indeed, policies are not the most interesting things in the world, but they are nonetheless important. If you want to avoid all valid PKI issues, it is best to consider having a certificate policy (CP). The certificate policy describes how and who releases and distributes certificates to a topic (such as user topics, computers, and devices, etc.). This can be a daunting task but you should not be too worried. Please follow the steps below and you will easily make certificate policy for your PKI.
1. Take a look at RFC 3647 (the component you can find through this document).
2. Then look at a certificate policy, although this policy may be more detailed than the policy you need. The X.509 Certificate Policy for the United States Department of Defense (DoD) - Policy for the US Prevention Commission (DoD).
Create a statement in using the certificate
At this point, we have almost completed the planning section, but still need to create a statement in certificate use (CPS). CPS is very similar to the certificate policy, except that it focuses on CA security (certificate authority) during operations and certificate management issued by CA. A CPS is usually much shorter than the security policy and includes information about who is responsible in case the certificate cannot be used to adequately protect what it is given. For example, an SSL / TLS connection when a customer is entering their credit card number. Other components included in a CPS are how to be eligible, re-created, and destroyed by the CA department responsible for issuing certificates. You can view a CPS as an agreement between the certificate user and the company responsible for issuing the CA. Here we have some examples for a CPS, which may be more familiar to you.
1. You can look through RFC 3647 about CPS here.
2. Alternatively, you can see VeriSign's CDP here
Unlike certificate policies, a CPS is always made available to the public so that a user with a certificate can always access CPS. In each certificate that your CA issues, there will be a link to indicate the location where CPS is published. We will take a closer look at this issue in part two of this article.
Conclude
We have already shown you an overview of some important issues to consider in the planning phase of building a PKI, it would be good to consider the information in this article from a It is important to build a PKI in a highly secure environment. Remember that this series only serves as a brief guide to help you get a PKI in the shortest possible time. If you want to get more details about planning, design and installation, take a look at the links we will cover below. In the next lesson we will continue to look closely at the various design and installation options you have with the best practices possible.
 Part 2: Design
Part 2: Design
 Part 3: Installation
Part 3: Installation
 Part 4: Troubleshooting
Part 4: Troubleshooting
The information expanded
All Microsoft PKI articles http://www.microsoft.com/pki
If you want to see how Microsoft does PKI, go to http://www.microsoft.com/technet/itsolutions/msit/security/deppkiin.mspx
And finally, the book - Microsoft Windows Server 2003 PKI and Certificate Security at http://www.microsoft.com/mspress/books/6745.asp
You should read it
- ★ Apache 2 supports SSL / TLS: Step-by-step instructions (continued Part II)
- ★ 7 most popular email security protocols today
- ★ Secure the installation of ISPConfig 3 with Certificate Class1 SSL of StartSSL
- ★ 10 important Windows Group Policy settings need to be done immediately
- ★ Use Group Policy Filtering to create a NAP DHCP enforcement policy - Part 1