
Small businesses how to fight hackers?
hackers can crash websites, destroy data and may have other bad behaviors for your corporate network ...

hackers can crash websites, destroy data and may have other bad behaviors for your corporate network ...

one of the most effective and popular ddos attacks today is based on hundreds of computers being hijacked (ie zombies). these zombies are often controlled and managed through irc

statistics show that these 10 ghost computer networks (botnets) are controlling 5 million computers and distributing 135 billion spam every day - accounting for 80% of the current
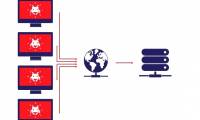
a botnet is a network of computers that have software installed to do a certain job. people often talk about botnets with a worse meaning than good because the botnet is used by a

if you're a counter-strike player, be careful.

researcher from newsky security recently discovered a hacker nicknamed anarchy, only 24 hours to build a botnet from 18,000 huawei router devices.

security researchers have discovered a botnet spread of malware through at least three new vulnerabilities published in microsoft office.
researchers at akamai have discovered a botnet with more than 14,000 ip addresses used to spread malware, using smart technology called fast flux.

the us government recently issued a warning about the possibility of a malware backed by the korean government, which is 8 years old.