Botnet Echobot spreads across a wide range, specifically targeting Oracle and VMware applications
A relatively new botnet named Echobot has contributed to 26 dangerous exploits, while using exploits as a tool to spread quickly. According to statistics, most of the exploits codes that Echobot contributes to are for IoT devices that have not been updated with security patches. However, many enterprise applications Oracle WebLogic and VMware SD-Wan are among the targets - a point to be particularly careful about.
Echobot is based on Mirai malware, which is like hundreds of other botnets that appear after the source of a malware is made public. It was first revealed (https://unit42.paloaltonetworks.com/new-mirai-variant-adds-8-new-Exloits-target-additable-iot-devices/) earlier this month by researchers Secure security at Palo Alto Networks. Experts have found this botnet at the time of 'only' part of 18 exploits worldwide.
- Telegram has just suffered heavy DDoS, but no significant damage was recorded
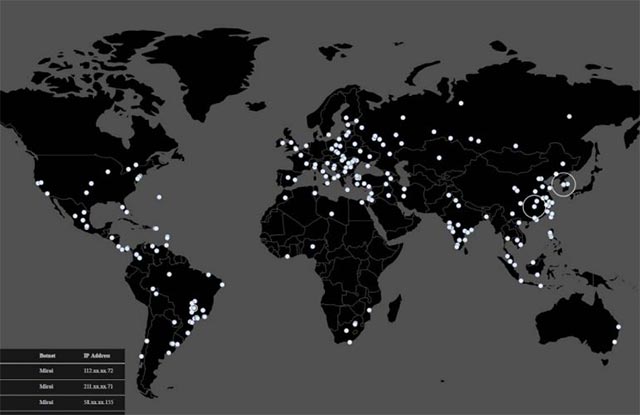 Echobot Botnet is spreading rapidly around the world
Echobot Botnet is spreading rapidly around the world
IoT devices become the main target
Popular security researcher Larry Cashdollar of Akamai's network security intelligence response group (SIRT) observed a new version of Echobot botnet, adding a new series of exploits to help it expand. spread.
"I have counted a total of 26 independent exploits that are being used to spread this botnet. Most of these are command execution vulnerabilities that are well known in other networked devices. each other, "said Larry Cashdollar.
- Shade ransomware, the nightmare of 5 years ago is showing signs of returning
 Target of Echobot variant
Target of Echobot variant
The goals of the latest Echobot variant include networked storage devices (NAS), routers (routers), network video recorders (NVRs), IP cameras, IP phones and presentation systems. wireless presentation systems.
The old holes that have been around for decades have been exploited again
Larry Cashdollar and colleagues are having difficulty identifying the vulnerabilities used by this botnet, because some of them have been publicly discovered, but there are no designated tracking numbers. specific for each case.
Cashdollar's team overcame the problem by contacting MITER and thanks to the organization reallocating the vector identification number, he found the CVE symbols missing.
This effort plays an extremely useful role not only for the research of Cashdollar and his colleagues, but also for other experts when finding vulnerabilities exploited in nature because the CVE number is a system. Standard classification is used by the infosec community.
Cashdollar has also compiled a list with the errors used by the new Echobot variant as follows:
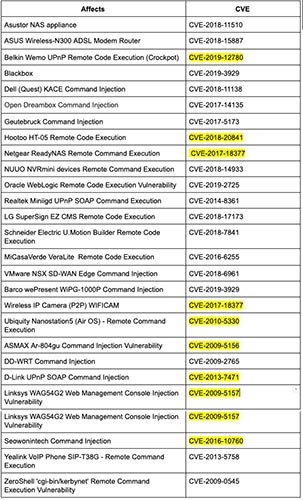 list with vulnerabilities used by new Echobot variants
list with vulnerabilities used by new Echobot variants
- Microsoft warned about malicious spam campaigns using vulnerabilities in Office and Wordpad
One important aspect this researcher warns is that the author (s) of the botnet expanded the target list beyond the IoT device range, and added exploits targeting Oracle WebLogic. VMware SD-WAN server and network software, which is used to provide cloud services, private data storage centers, and SaaS-based enterprise applications - play a critical role with many organizations and businesses.
In addition, the team also noted the phenomenon of old security vulnerabilities that have been around for decades that have been exploited by this botnet, suggesting that malware authors are completely unaware. mind the age of the vulnerability, provided they still have excellent performance for devices that have not been patched.
This shows that many vulnerable systems are still being used, and most likely they become good prey for Echobot background updates not timely security patches.
- GoldBrute botnet campaign is trying to hack 1.5 million RDP servers worldwide
Research by Larry Cashdollar and colleagues revealed more information about Echobot only using the same attack code originating from Mirai, and the most obvious difference is in the exploits that are helping it. spread quickly around the world.
Larry Cashdollar noticed that the command and control servers (C2 Server) were set for domains akumaiotsolutions [.] Pw and akuma Pw, although they were completely non-resolving to IP addresses.